White, Grey, and Black Box Testing
Penetration testing will allow you to avoid cybersecurity-related incidents that can damage the reputation of your company and cause a loss of significant funds. A successful implementation of exploiting the vulnerabilities will allow demonstrating possible ways of penetration into the informational systems as well as detecting critical security issues. It means there will be a possibility to allocate wisely financial and material resources on providing security where it’s needed the most.
The time frame, cost of the work, methods, type and the number of services, as well as the type of reporting, are determined at the stage of planning the test. There are 3 ways of performing a penetration test.
“Black Box” Testing
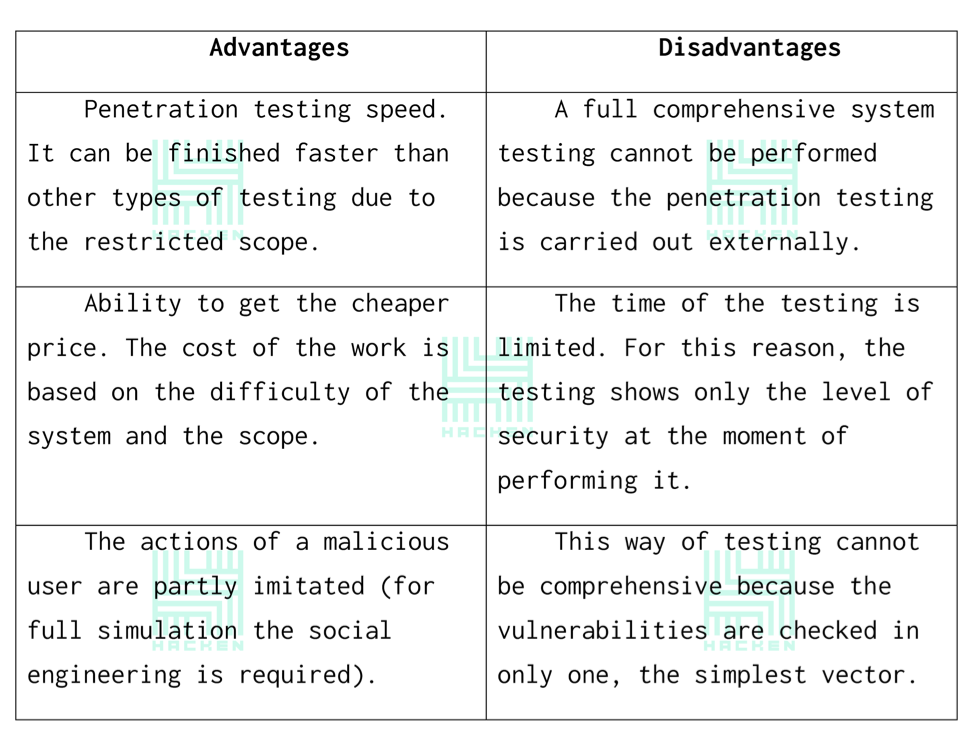
“Black Box” Testing is an action of an ethical hacker or pentester which imitates the behavior of a malicious user in order to check the security level of an external perimeter or/and a website.
In simple words, “Black Box” testing doesn’t require any knowledge of the system. Such testing has a restriction described in the scope and negotiated with a client. Application of social engineering for acquiring information is discussed separately.
Why the “black box”? The tested program for the pentester is like a black non-transparent box the contents of which can’t be seen. The goal of the technique is to find issues in the following categories:
- incorrectly implemented functional causing vulnerabilities;
- errors in connecting to the application from the Internet;
- errors in data structures or in providing access to the external databases;
- behavioral issues;
- poor system performance.
Therefore, we don’t have any idea about the structure and internal system’s set-up. It’s necessary to concentrate on what the program does instead of how it does it.
In order to carry out an extended “Black Box” testing, it’s recommended to use Bug Bounty programs located on specialized platforms such as HackenProof, HackerOne, BugCrowd etc.
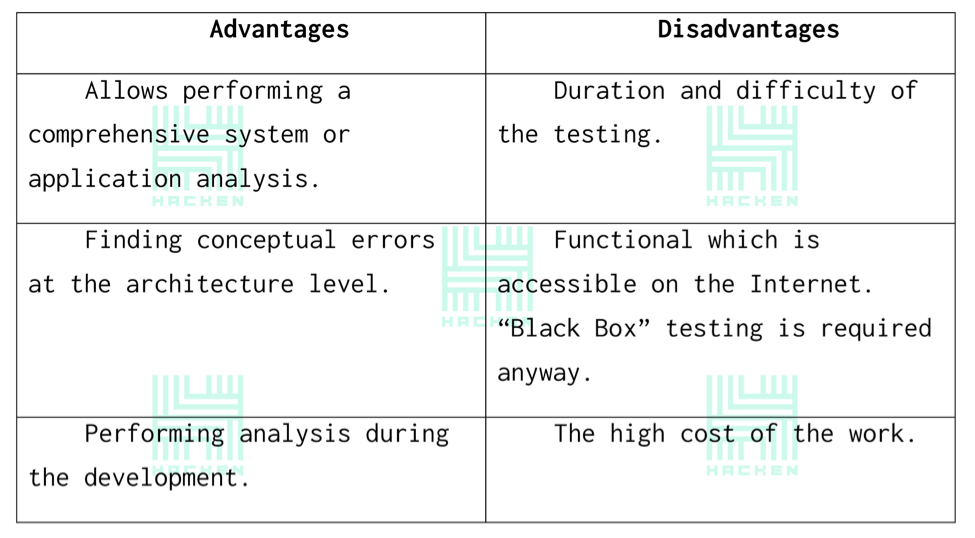
Advantages and disadvantages of “Black Box” testing
“Grey Box” Testing
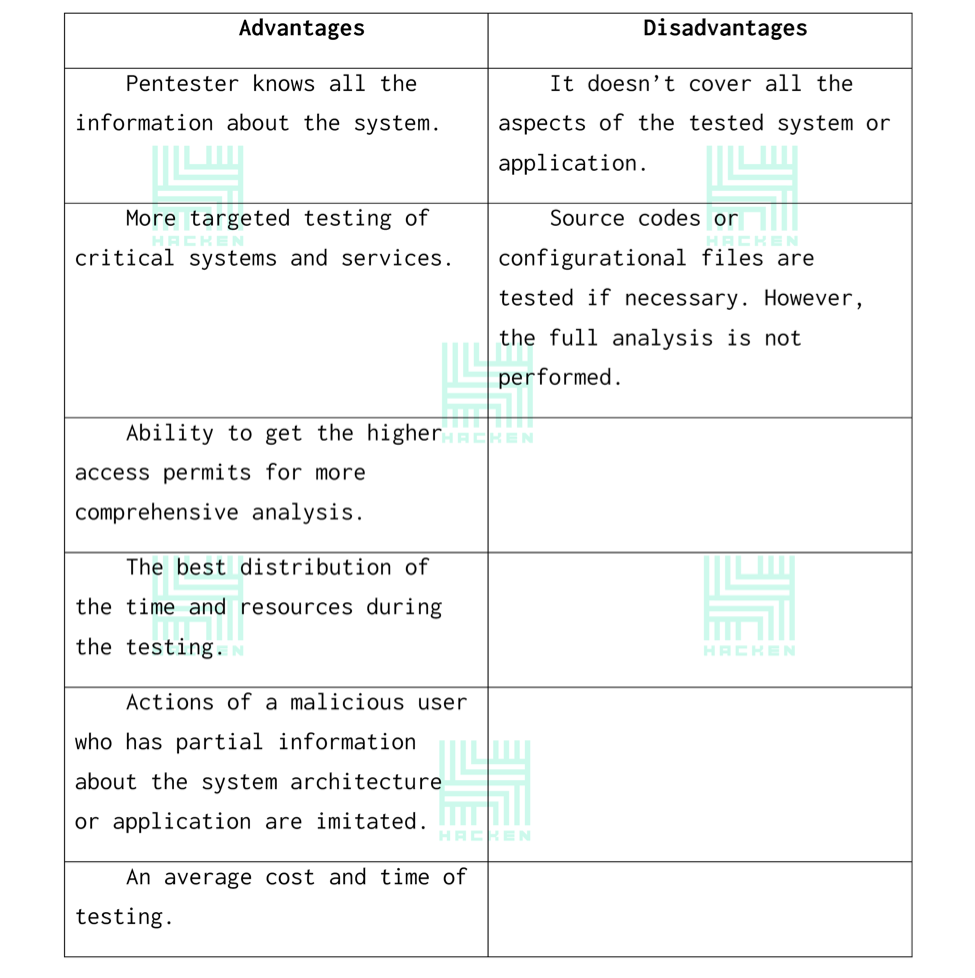
“Grey Box” testing is an action of an ethical hacker or pentester which is aimed at detecting system vulnerabilities supported by the client’s tech specialists. The client should provide all the information required for the testing to the perpetrator.
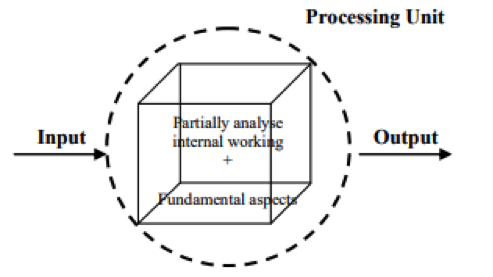
“Grey Box” testing is something between the full imitation of a malicious user’s behavior and performing a full analysis.
During the preliminary negotiations with the client, the tester compiles a list of questions required for the analysis. These are usually the following:
- The list of domain names, services, and IP addresses.
- Which services are the most critical and which information the client is afraid to lose.
- Ability to add accounts and IP addresses into the whitelist in order to prevent blocking. If there’s a necessity to check how the system security is provided, then the client and the tester are scheduling time during which the testing will be performed with the security on.
- If the exchanges are tested, then the finances for the testing operations are required.
- Additional questions about the architecture of the tested system which are coming up during the negotiations.
Advantages and disadvantages of the “Grey Box” testing
“White Box” Testing
“White Box” testing is the action of an ethical hacker or pentester aimed at detecting system vulnerabilities which include a full check of the tested system or application with the set exceptions in the security system, providing source code for the analysis (if it is not publicly accessible) etc. Tech specialists must provide all the information about the tested system.
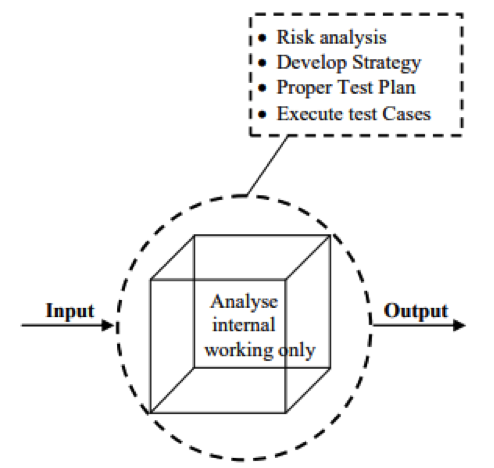
“White Box” testing is very similar to audit when everything is provided including source codes, server, and other equipment configurations, technical documentation, direct communication with tech specialists.
According to ISTQB (International Software Testing Qualifications Board), “White Box” testing is:
- testing based on the analysis of the internal structure of the system or its component;
- a procedure of creating or choosing test-cases based on the internal structure of the system or its component.
Advantages and disadvantages of “White Box” testing
Summing Up
If a partial malicious user’s behavior imitation is required then the “Black Box” testing should be requested, however, if a full imitation of a hacker is needed then it’s better to create a Bug Bounty program on special platforms such as HackenProof and others.
According to statistics of the projects carried out by our team, “Grey Box” testing is ordered more often. Such an approach allows partially imitating hacker’s behavior and maintaining communication between a client and a perpetrator at the same time.
“White Box” testing is necessary for performing planned and regulatory audits. Often SDLC (Software Development Lifecycle) principles are utilized during large enterprise projects’ development and a special employee or a team that controls secure code development is hired.
How Hacken can help
At Hacken, we take security extremely seriously, and all the checks are performed according to the highest standards. If you have any questions about the topic or need a consultation, feel free to contact our Team!
Tell us about your project
Read next:
More related Crypto Travel Rule: Global VASP Requirements in 2025
Crypto Travel Rule: Global VASP Requirements in 202511 min read
Discover
 What Is Web2.5? A Builder’s Guide to the Web2–Web3 Bridge
What Is Web2.5? A Builder’s Guide to the Web2–Web3 Bridge5 min read
Discover
 How to Choose a VASP License: Jurisdictions, Costs & Compliance
How to Choose a VASP License: Jurisdictions, Costs & Compliance5 min read
Discover