EOS Smart Contracts Audit Overview
What is a smart contract audit and why is it necessary to perform?
In general, an audit is performed to highlight any potential problems with a contract. There are, however, other areas where auditing can be used to test systems, networks, and applications in addition to checking smart contracts for bugs, vulnerabilities, and any loopholes. Any flaws in development may cause crashes, errors, and bugs that are common in the world of technology.
How do you avoid such potentially dangerous problems?
The answer is you cannot avoid them entirely but you can decrease their likelihood by auditing your system regularly. In some instances, this process can save a company a considerable amount of money and even more importantly, their reputation.
How do you recognize the need to perform an audit?
Usually, audits are ordered before the release of a new version of a program or after a system update.
If the aforementioned options are not relevant and you have not performed any updates for a long time or your app release was done a long time ago, you might incorrectly believe that everything is in order. However, we have to disappoint you - hackers do not sleep and the ‘bad’ guys are always ready to attack your system motivated by either money or personal ego.
That’s why performing an audit is the best way to avoid any of the above problems.
So let’s dive deeper into the auditing process and show you below an example of a HACKEN report.
The main parts of the report
The report is a key component of the auditing process, and it provides the customer with clear and informative findings. Normally a good report (e.g., a HACKEN report) should include the following:
- Introduction (the main information regarding the research)
- Scope (the scope of research)
- Executive Summary (a brief summary of the main findings)
- Severity Definitions (a risk table of vulnerabilities)
- AS-IS Overview (how the system should work)
- Audit Overview (a detailed overview of the findings)
- Conclusion (a summary of the research)
- Disclaimers
We have below reviewed the 4 most interesting parts of the report.
Executive Summary
An audit summary is given in the ‘Executive Summary’ section and contains a general conclusion about the security of the smart contract. It categorizes the smart contract into insecure, poorly secured, secured or well-secured. The executive summary presents all stages of the audit with a brief outline of the results at each stage. This section also contains statistics regarding any bugs found in the audit and their distribution by severity. An executive summary would be the first section to be reviewed by any third parties or top management since it contains the overall brief summary of the audit.
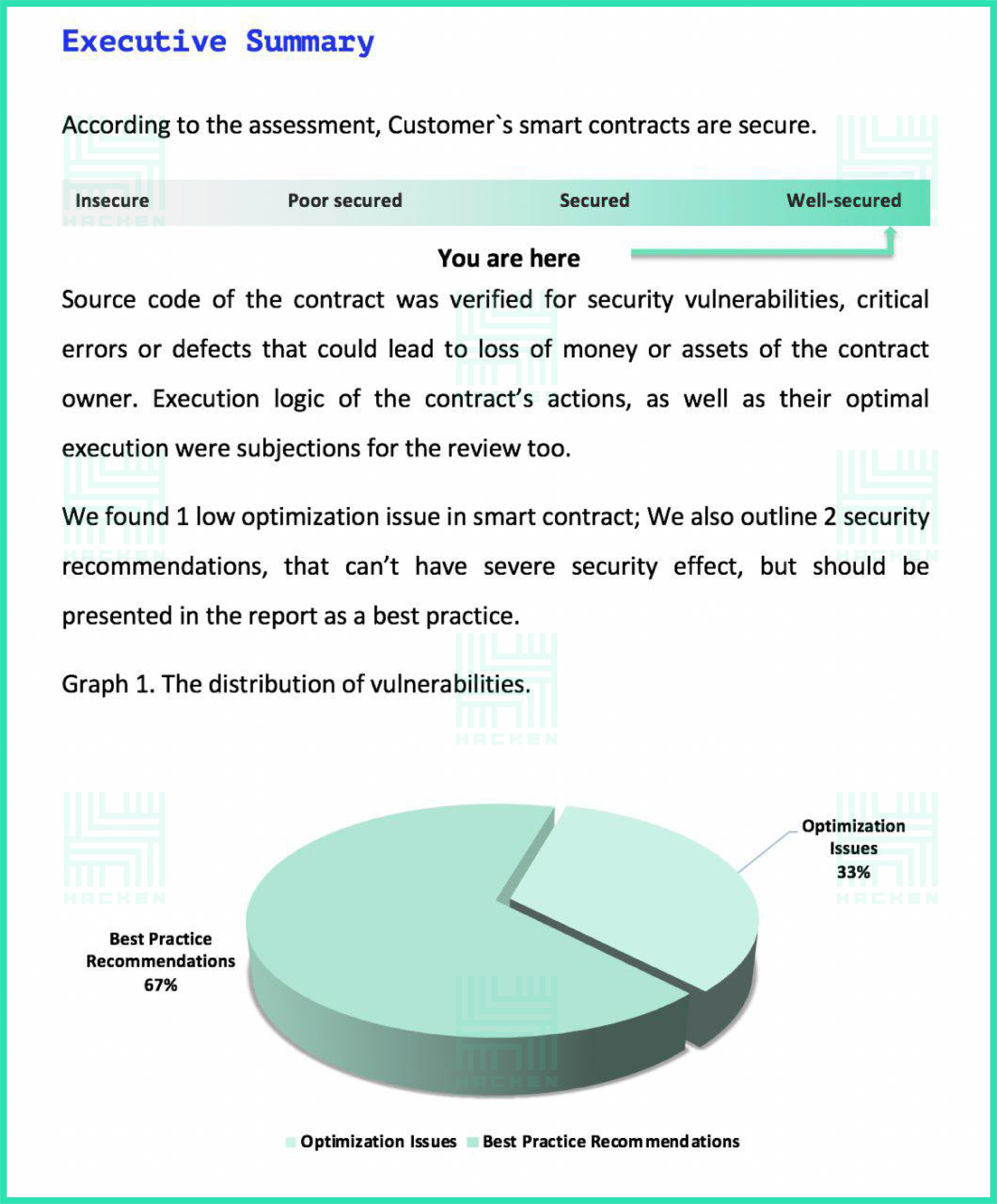
Severity Definitions
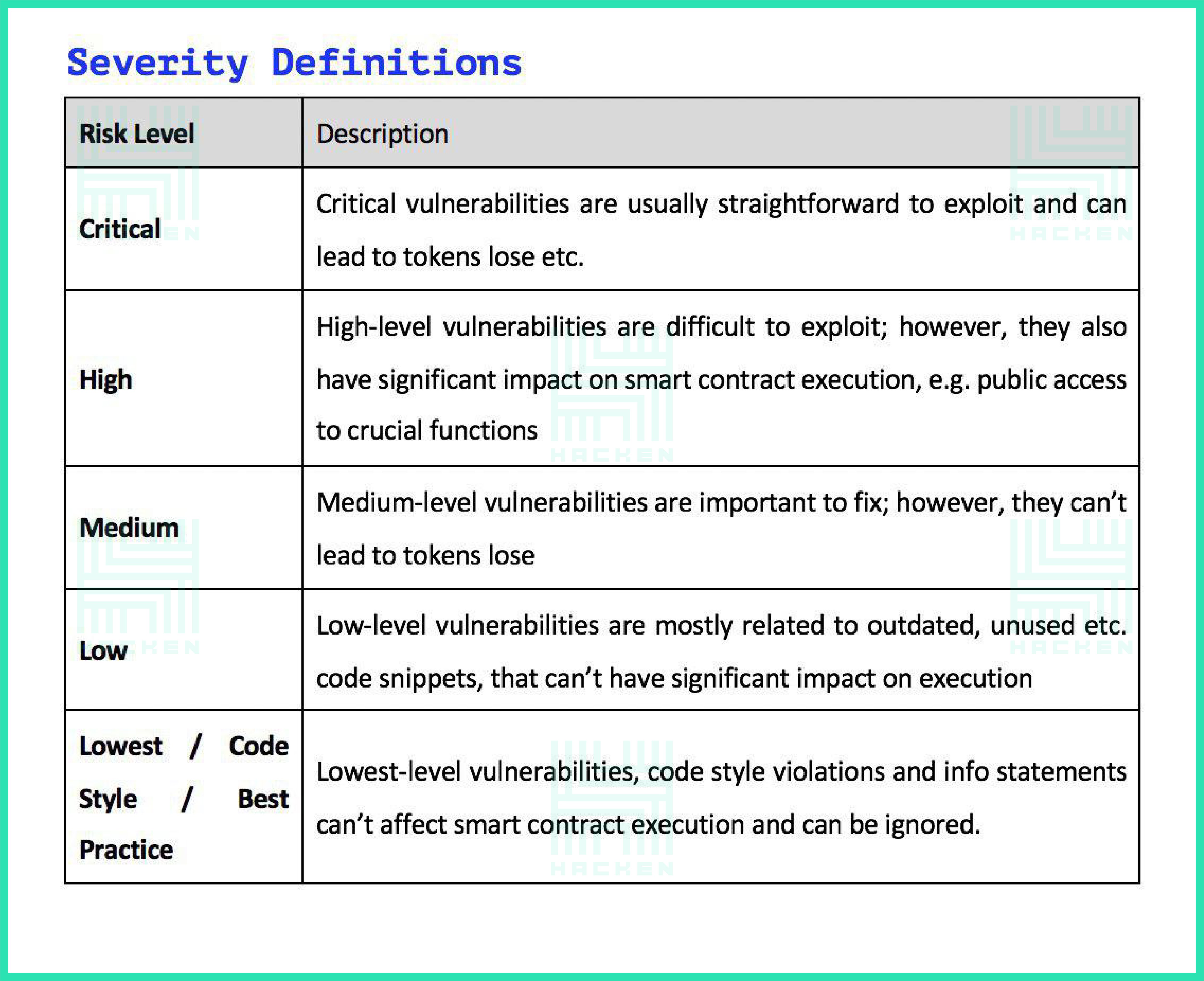
The table below shows a list of all potential vulnerabilities given in the ‘Severity Definitions’ section. It contains 5 standard, commonly used risk levels as follows
- Critical
- High
- Medium
- Low
- Code style / Best practice
A more detailed description of each of them is set out in the table below
AS-IS Overview
The functionality of the code is presented in the “AS-IS Overview” section.
What is defined in this section and how does it work?
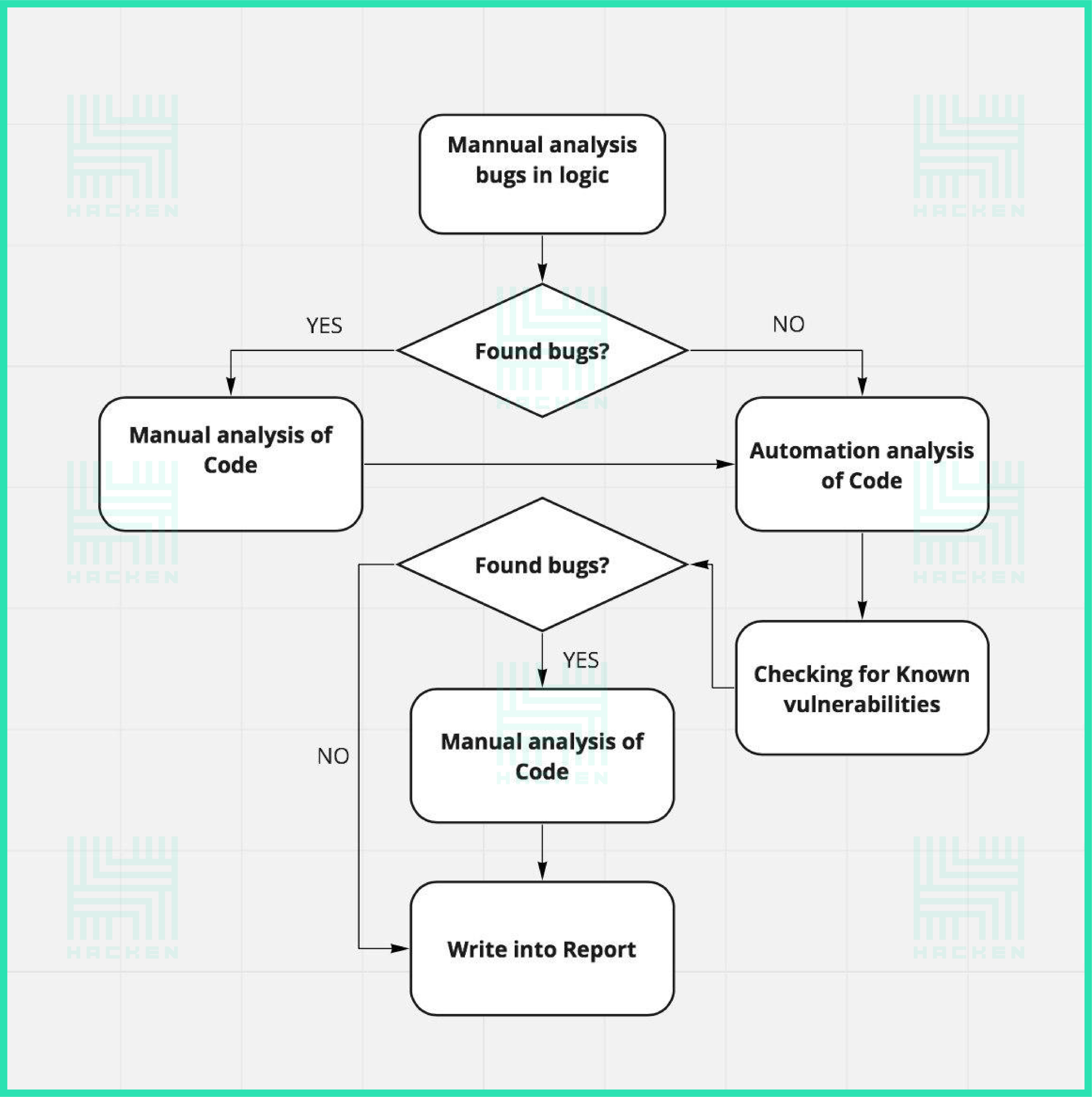
Here is a quick guide to understanding the diagram:
- Analyze the logic of the app (try to identify any problem areas)
- If any bugs are detected scrutinize each line of the code or suspected areas where they are detected.
- After a manual analysis, we proceed with automated analysis tools in order to check the entire code.
- We then test the app for any known or common vulnerabilities (we have an exhaustive list in place)
- If any common vulnerabilities are found we will then search again and scrutinize that particular area of code.
This process is how we search for bugs and vulnerabilities in a customer’s project.
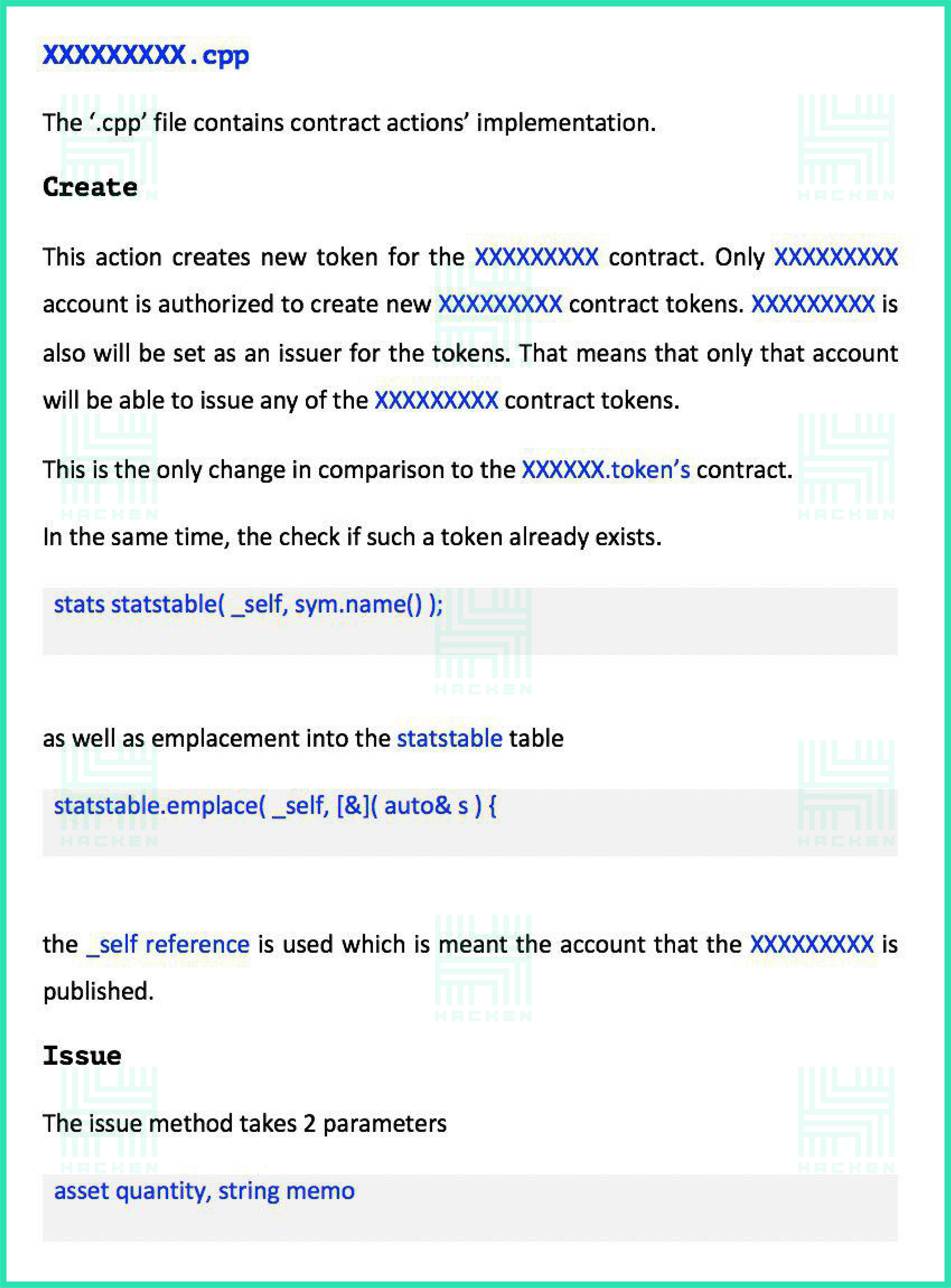

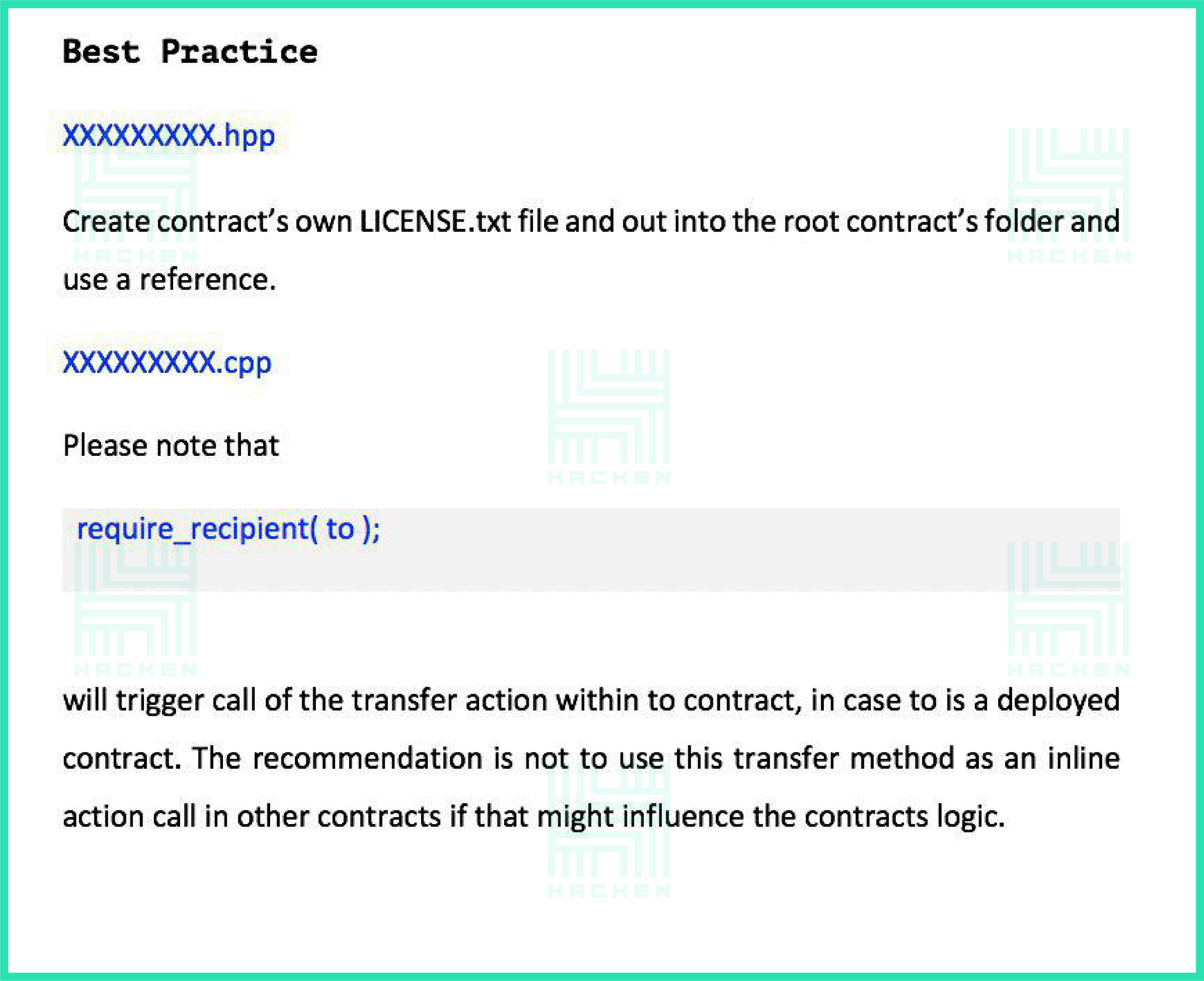
Audit Overview
The ‘Audit Overview’ section is where we share detailed findings from the audit.
- All findings (everything that was found as described below)
- Where they were detected (files, number of lines, etc.)
- Method of detection (tools and techniques used)
- Method of correction (recommendation for correction, the definition of standards)

HACKEN audits
Who is Hacken?
Hacken has considerable experience of successfully performing tests for online services including online stores, mobile pentests, cryptocurrency platforms, and online registration systems.
We’re a new world player in the cybersecurity market, keen on helping all businesses, including startups, to protect their image, reputation, and financial security.
Examples:
Auditing Price
The price depends on:
- Code volume
- Research time
- Individual researcher labor cost
The audit will differ according to the type of product under consideration’. The final cost of the report should then be verified with the auditing company.
Summary
As explained in the foregoing ‘EOS Smart Contract’ overview by HACKEN, an audit is vital for your applications, programs, systems and networks etc., and sooner or later you will need to perform one.
A good quality audit covers many aspects including the scope of research, description of findings, any discovered bugs, a table of vulnerabilities classified by risk, an as-is overview, program functionality and a detailed overview of findings.
If you need to audit an EOS smart contract or DApp you can order one from HACKEN as our experts can perform a high-quality audit that will guarantee customer satisfaction.
Table of contents
Tell us about your project
Read next:
More related What Is Web2.5? A Builder’s Guide to the Web2–Web3 Bridge
What Is Web2.5? A Builder’s Guide to the Web2–Web3 Bridge5 min read
Discover
 How to Choose a VASP License: Jurisdictions, Costs & Compliance
How to Choose a VASP License: Jurisdictions, Costs & Compliance5 min read
Discover
 What Is a Virtual Asset Service Provider (VASP) in Crypto?
What Is a Virtual Asset Service Provider (VASP) in Crypto?5 min read
Discover