Dangers of Laravel Debug Mode Enabled
We have spent the last couple of weeks researching Laravel, a popular open-source PHP framework intended for the development of web applications. Like many similar frameworks it includes a debug mode with a special interface, allowing developers to view the internal state of network connections for the purpose of identifying errors and misconfigurations, before going live.
The Problem
There is nothing wrong with having a debug mode enabled, but the real danger is to have this mode on while the system is live. We have used both BinaryEdge and Shodan search results to see how many servers are exposed and came up with a shocking list of 566 IPs.
Here is an example of how the debug interface looks in a web-browser and what kind of parameters are open to view in plain text (hint – almost all digital keys are there sometimes):
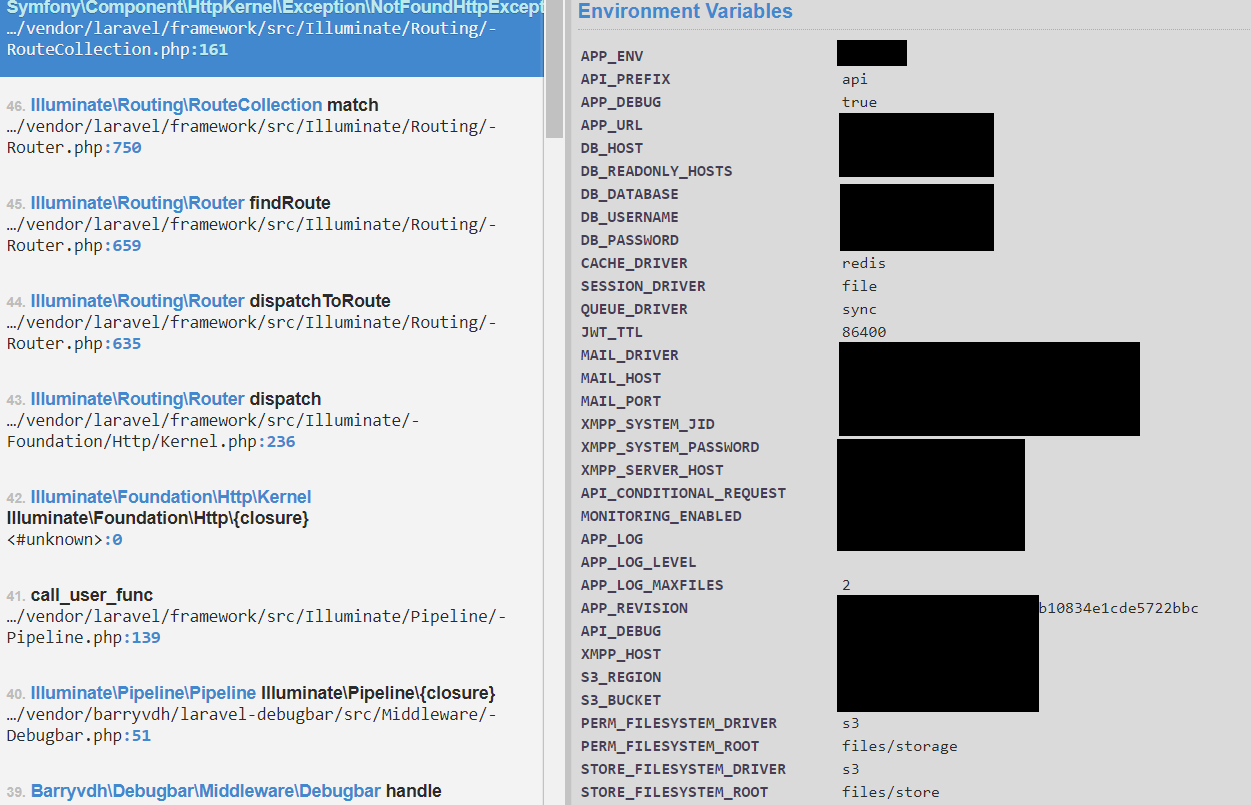
Interest for Attackers
Note that not all servers show the full details of passwords and databases in debug mode. However, the screen above should give you an understanding of the level of detail available for those who accidentally or on purpose may come across this.
Apart from the web server disclosing some system information data in the HTTP response, such as application keys, database connection strings, passwords, secret credentials etc, debug mode enables extra debugging behaviors that assist not only developers, but also potential attackers.
This information might help an attacker gain more information and potentially focus on the development of further attacks with which to target the system.
A Breached Company
For the last two weeks we have responsibly notified 22 companies whose sensitive data was exposed in such a manner. One of the companies that inadvertently exposed its production data via the debug mode interface was Swedish-based PrestoDaycare, a child tracking and monitoring platform start-up.
PrestoDaycare positions itself as a digital toolkit that integrates technology into traditional schools. This allows teachers to manage the classroom by creating digital student portfolios, registering attendance and scheduling 1-on-1 conferences. It also allows teachers to communicate with the parents by updating the online calendar, tracking student progress, and issuing grade reports.
However, it appeared that the admin section on their homepage was misconfigured in such a way that anybody who may have misspelt the URL would be directed straight to the debug page which contained practically all the company’s credentials in one place including secret keys, database locations, credentials administrator passwords, and many more sensitive details.


Responsible Disclosure
On September 26th we tried to get in touch with the Company to alert them to the potential security breach but were only able to leave a voicemail and send a notification email which went unanswered. An additional email was sent to the local CERT authority.
With the assistance of Sweedish Twitter followers, we finally got the attention of the PrestoDaycare developers and they replied with the following statement:
We would again like to express our thanks for reaching out to us on this matter. We have, as a GDPR-compliant organization, notified the incident as per the directive. The reason for the information leak was a bug in the handling of error events in the web app, which caused the web app to act as it was in debug mode (which it wasn’t configured to be).
Summing Up
The data breach was secured within an hour although we don’t know how long it had been left unnoticed and if any secure information had already been accessed.
There still remains at least 5 companies who have not responded to the notifications and have Laravel interface set in debug mode.
How Hacken can Help
At Hacken, we take security extremely seriously, and all the checks are performed according to the highest standards. If you have any questions about the topic or need a consultation, feel free to contact our Team!
Read also:
An Interview with Bob Diachenko, Hacken’s Director of Cyber Risk Research
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.
Tell us about your project
Read next:
More related- Best Practices For Secure MetaMask Snaps Development
10 min read
Discover
- Protecting Web3: Q3 2023 Security Insights Report
2 min read
Discover