Ethical Hacking In Action: How To Steal $1.1M From A DeFi Smart Contract
A case study of ethical hacking detailing how Hacken’s L1 Researcher and Auditor, Bartosz Barwikowski, uncovered a deeply hidden bug in Weft Finance’s smart contract, exploited it to extract $1.1 million in assets (on a mainnet ledger copy) and ultimately helped secure the platform, leading him to confidently stake his own assets there.
The Beginning: Audit of Radix DLT
In April 2023, I began auditing the Radix DLT virtual machine. Radix is a Layer 1 protocol with a strong emphasis on being user-friendly for both developers and users. It offers numerous built-in features for DeFi, and its design aims to mitigate common issues seen in other protocols.
During a three-month audit, I identified eight critical issues within Radix DLT. These included a bug that allowed minting any number of tokens, a flaw enabling bypassing authentication, and six separate issues that could lead to application crashes. After these were addressed, I conducted another three-month audit, at the end of which Radix DLT achieved a perfect score of 10 out of 10. The results were publicly shared, reinforcing Radix’s commitment to transparency and security.
Read more about Radix Engine Code Audit
Diving into the Ecosystem: Discovering Weft Finance
Having completed the audit, I found myself increasingly interested in the Radix ecosystem. From a developer’s perspective, the protocol was a pleasure to work with, offering a smoother experience than many other blockchains I had encountered. I was confident in its security after the issues had been fixed, so I bought some Radix tokens, added liquidity, and began exploring its decentralized applications.
In April 2024, I stumbled upon Weft Finance, a lending and borrowing platform operating on Radix. The project was intriguing, offering a staggering 82% APR on USDC. My immediate thought was that such high returns usually come with significant risk, or worse, are a sign of a scam. To determine which it was, I decided to dig deeper into their smart contracts, which were fortunately open-source.
The Technical Deep Dive: Exploring the Vulnerability
The Weft Finance smart contract was complex but initially appeared solid: it had undergone an audit with another security firm. To ensure there were no hidden issues, I wrote a program to simulate the closing of all loans and the withdrawal of all lent funds. This simulation was crucial—it would reveal if the platform could cover all loans and if there were enough funds to repay lenders.
The system seemed robust, even when I tested scenarios involving a sudden 10-20% drop in collateral value. However, I noticed something concerning in the liquidation process. The process was designed to take collateral first and then require the user to repay the loan in the same transaction, similar to how flash loans work. While this approach wasn’t inherently flawed, it was a complex function, and complexity often leads to mistakes.
The Exploit: Leveraging the Liquidation Process
The crux of the issue lay in the handling of delegatees—secondary loans created without collateral. The smart contract allowed the creation of a delegatee linked to a delegator (the original loan holder) by using the link_cdp function. This function was supposed to ensure that the sum of all loans remained less than 100% of the collateral. However, there was no validation to prevent the creation of a delegatee with an active loan but no collateral.
How Adding a Delegatee With Debt Should Work?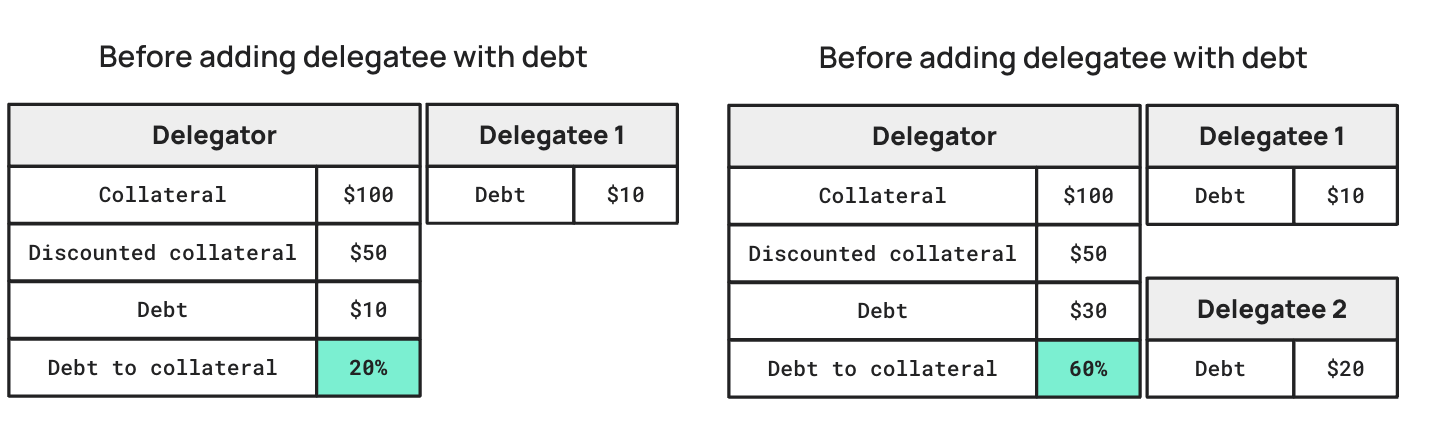
A loan of a new delegatee should be added to the sum of all debts, and debt to collateral should be less than 100% for a successful transaction.
How Adding a Delegatee With Active Loan Actually Worked?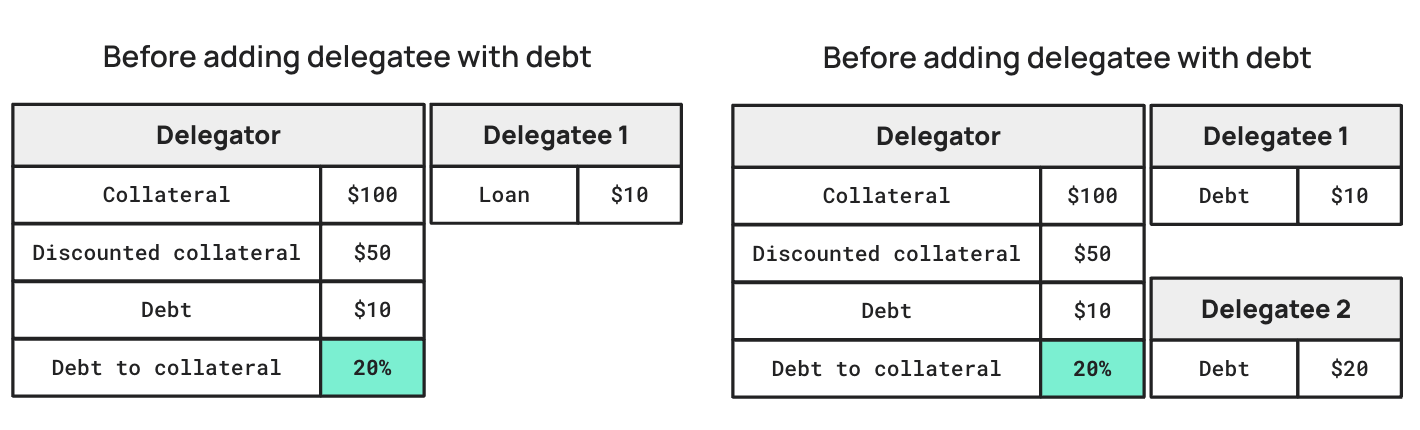
All loans were assumed to be backed by collateral. However, the link_cdp function failed to update the total debt of the delegator. While this wasn’t a critical issue yet, it had the potential to become one.
Creating a Loan With No Collateral
This oversight created a significant vulnerability. By initiating liquidation twice, I could temporarily remove all collateral from a loan and create a delegatee with an active loan, bypassing the requirement for collateral. The link_cdp function failed to update the sum of loans correctly, allowing me to manipulate the loan system and effectively borrow assets without the necessary collateral.
Coding the Exploit: The Technical Details
With the vulnerability identified, I began coding the exploit. This was no small task—the final exploit script was over 1,000 lines of code, and it took me about 30 hours to complete. The code accounted for multiple edge cases, such as rounding errors, transaction costs, and forced liquidation scenarios. The goal was to simulate this on a copy of the mainnet ledger, ensuring the exploit would work in the real-world environment.

Once the code was ready, I executed it in a simulated environment that mirrored the mainnet conditions. The exploit was devastatingly effective—it stole everything within 15 minutes, completing roughly 1,000 transactions and extracting 22 million XRD and 69,000 USDC, valued at $1.1 million at that time.
Contacting Weft Finance: Ethical Hacking in Action
Upon confirming the exploit’s effectiveness, I immediately reached out to Weft Finance through Telegram. I informed them of the critical issue in their liquidation process and negotiated a bug bounty. Over the next two days, after sharing the exploit code and providing a detailed explanation of the issue, I worked with them to fix the bug.
To demonstrate my confidence in the remediation, I staked $11,500 of my own assets on their platform, believing in the security of the system post-fix. The remediation not only secured Weft Finance but also reinforced the importance of thorough audits and continuous monitoring.
Final Thoughts: Lessons Learned
This experience underscored several key lessons for both developers and auditors:
- Simplicity is Key: Keep smart contracts as straightforward as possible. Complex functions like flash loans introduce significant risk and should be implemented only when absolutely necessary.
- Rigorous Testing: Testing must cover all possible scenarios, including edge cases that might seem improbable. The more comprehensive the testing, the better the chances of catching critical bugs before they can be exploited.
- Proactive Auditing: Regular audits are essential, especially for new ecosystems like Radix. In this case, Weft had undergone an audit with another security firm, which was helpful but missed a critical, deeply hidden vulnerability. It’s important to either work with multiple auditors or choose one with extensive experience in your specific tech stack.
- Bug Bounty Programs: A well-structured bug bounty program can save platforms from disastrous outcomes. Incentivizing ethical hackers to find and report vulnerabilities is crucial for the long-term health of any blockchain ecosystem.
This case study highlights the vital role that thorough audits and ethical hacking play in securing blockchain technologies. The Radix DLT and Weft Finance ecosystems are now more robust thanks to these proactive measures, protecting both the protocol and its users.
Follow @hackenclub on 𝕏 (Twitter)
About Me: Bartosz Barwikowski
I am a Layer 1 blockchain researcher and auditor at Hacken, where I have identified over 70 critical vulnerabilities in blockchain projects within the past year. My deep expertise spans all levels of blockchain architecture, with a particular focus on Layer 1 protocols. In 2020, I co-founded a blockchain cybersecurity and decentralized identity startup, successfully raising $250k in a pre-seed round.
My journey in the crypto space began in 2014 when I started trading and mining Bitcoin. By 2017, I had written my first smart contract, which led to my involvement in developing secure dApps and various blockchain implementations. Over the years, I have co-founded multiple startups dedicated to decentralized identity technology, aimed at replacing passwords with public-key cryptography capable of managing millions of users.
Since joining Hacken in June 2022, I have been instrumental in detecting vulnerabilities in Layer 1 protocols and have played a key role in developing internal fuzzing services based on OSS-Fuzz and ClusterFuzz as well as the Wasmcov code coverage tool for WebAssembly. In 2023, I identified and helped resolve a critical bug in Binance’s zkSNARK-based Proof of Reserves system. I hold certifications from C4’s CryptoCurrency Security Standard Auditor, Certified Ethereum Professional, and Certified Bitcoin Professional programs. I also graduated with a degree in Computer Science from the Warsaw University of Technology.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.

Table of contents
Tell us about your project
Read next:
More related Blackbox and Graybox Penetration Testing for EBSI (APIs and Web Apps)
Blackbox and Graybox Penetration Testing for EBSI (APIs and Web Apps)3 min read
Case Studies
 Protocol and Tokenomics Audit of PhronAI’s AI-Powered Layer 0 / Layer 1 Blockchain
Protocol and Tokenomics Audit of PhronAI’s AI-Powered Layer 0 / Layer 1 Blockchain6 min read
Case Studies
 Securing Crypto Exchange Against Vulnerabilities – Gate.io Success Story
Securing Crypto Exchange Against Vulnerabilities – Gate.io Success Story5 min read
Case Studies