Securing Crypto Exchange Against Vulnerabilities – Gate.io Success Story
Gate.io Security Challenge

Gate.io is listed among the top 10 crypto exchanges according to CoinMarketCap. Since its founding in 2013, the company has remained committed to making the safety and security of its users its top priority, which requires strong safety measures to protect its traders from hackers and fraudsters.
To do this, Gate.io published a bug bounty on HackenProof with 6 in-scope assets:
- 2 web assets (Website & API)
- 2 mobile apps (iOS & Android)
- 2 desktop apps (Windows & Mac)
Gate.io has set the bounty range from $50 to $5 000, depending on the severity:
- Critical: $3 000 – $5 000
- High: $900 – $2 000
- Medium: $300 – $500
- Low: $50 – $150
Gate.io Bug Bounty Results
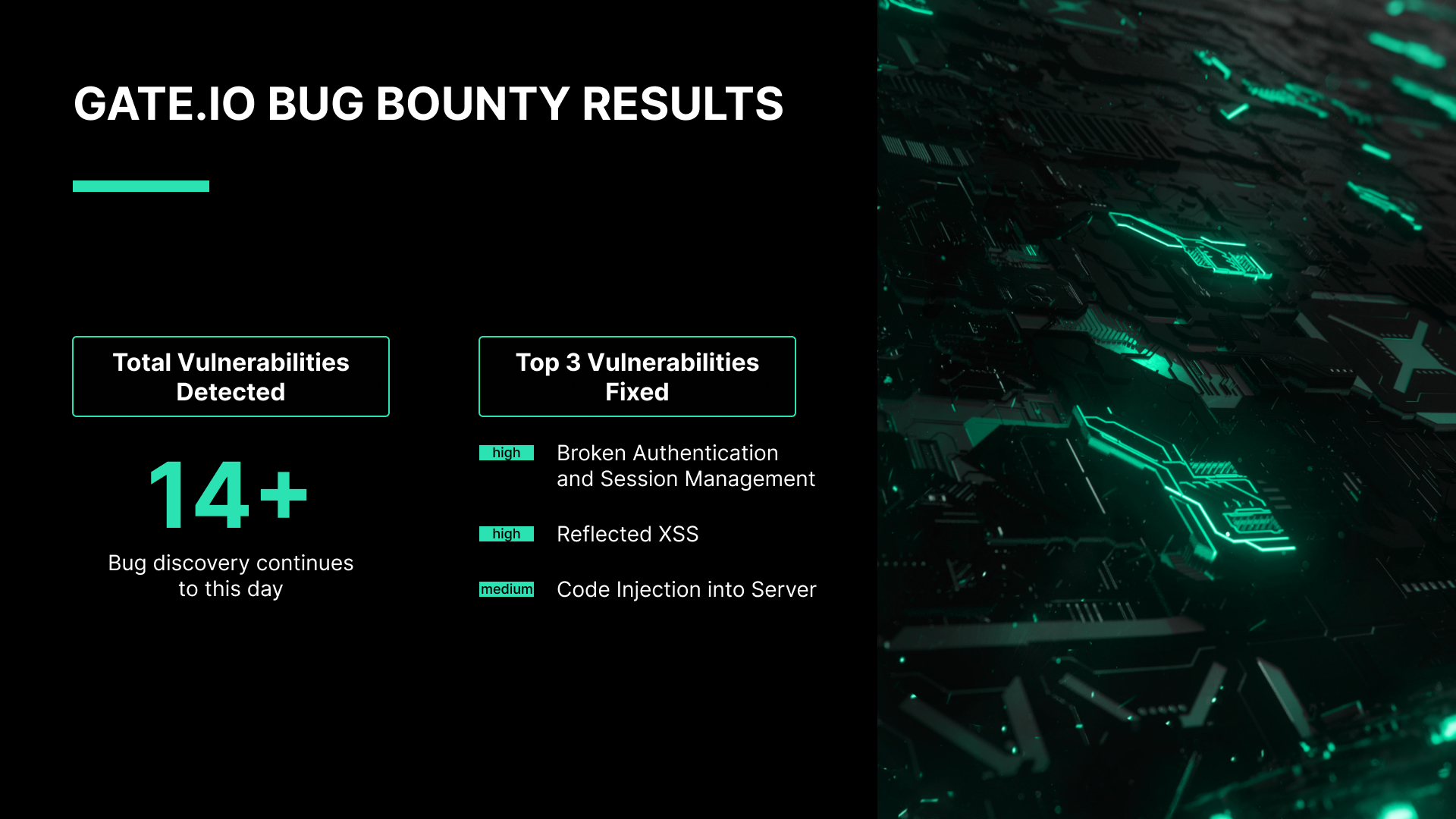
HackenProof whitehats have identified 14 vulnerabilities so far.
This success story describes the top 3 vulnerabilities which the company has fixed:
- Broken Authentication and Session Management | High
- Reflected XSS | High
- Code Injection into Server | Medium
Broken Authentication and Session Management
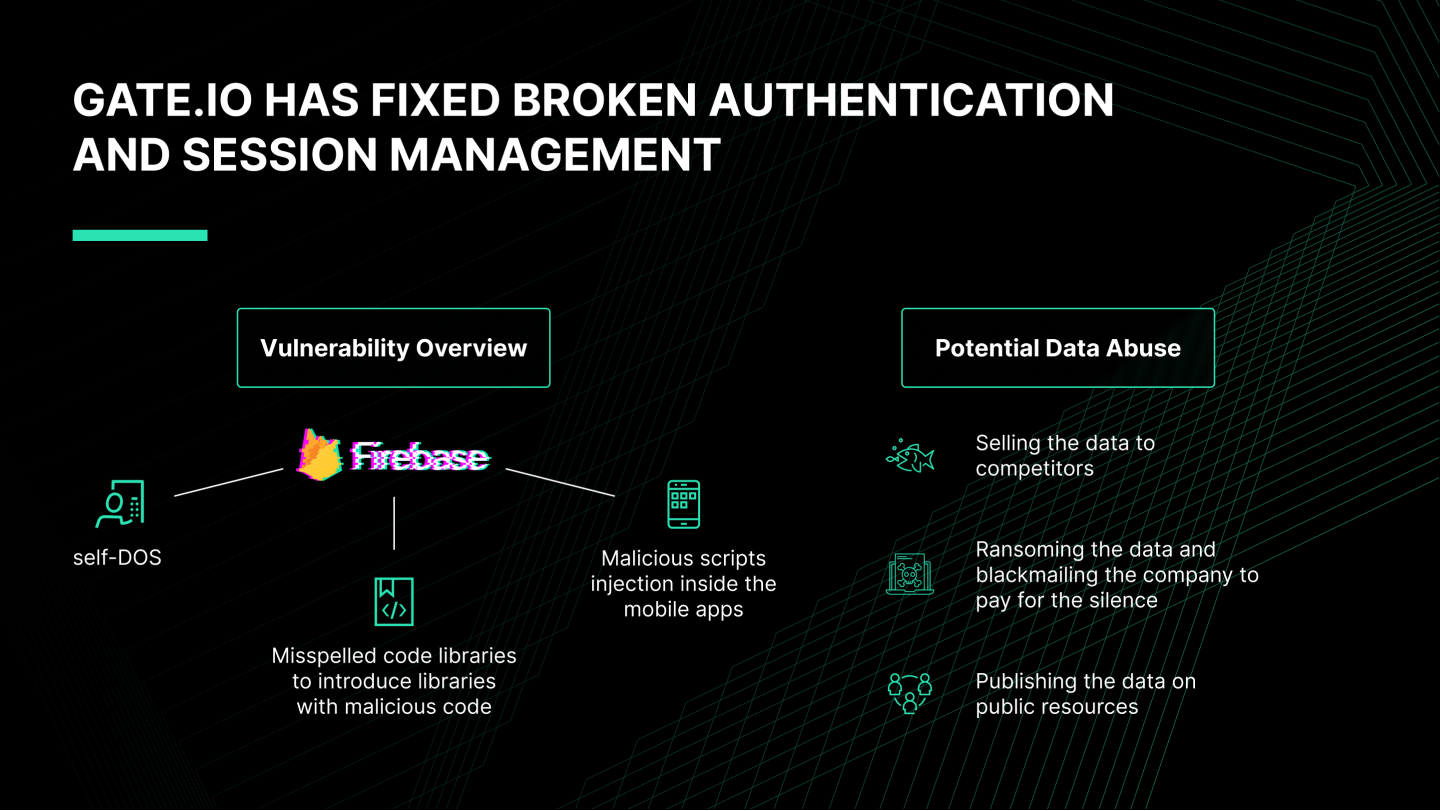
A hacker could create a new Google Firebase user for the Android app.
They could create it without administration rights using API.
Potential Damage
Google Firebase is an analytics tool for measuring user performance inside mobile apps. Creating an unauthorized account inside this tool would lead to system manipulation and data leakage.
The attacker could harm the infrastructure in 3 ways:
- Set up self-DOS
- Misspell code libraries to introduce libraries with malicious code
- Inject malicious scripts inside the mobile app
The attacker could use the data in 3 ways:
- Sell the data to competitors
- Ransom the data and blackmail the company to pay for the silence
- Publish the data on public resources
Reflected XSS

A hacker could inject a malicious script into the ranking page.
They could do this using a reflected XSS attack.
XSS injection is when an attacker can inject a malicious script into a website or app.
The script is triggered when a victim visits the infected page.
A reflected XSS is when the malicious part is added to the URL string.
A victim would still access the legitimate website, but their data would be compromised.
For example, this link can be safe – hackenproof.com.
While this link could be dangerous:
https://gate.io?ranking_id=virus.hash;onload=setTimeout;#1/-alert(666)/
Potential Damage
The attacker could harm Gate.io users in 3 ways:
- Steal data from cookies
- Steal data from account information
- Impersonate account owner
Cookie data can be used for session hijacking or donation. Session hijacking is when an attacker can impersonate a victim inside an app. Session donation is when an attacker tricks the victim into performing actions inside the attacker’s account. For more cookie exploits, check out this source.
Stealing data from account information could include things like names, addresses, and finances.
Impersonating the account owner could have led to stealing the funds.
Code Injection into Server
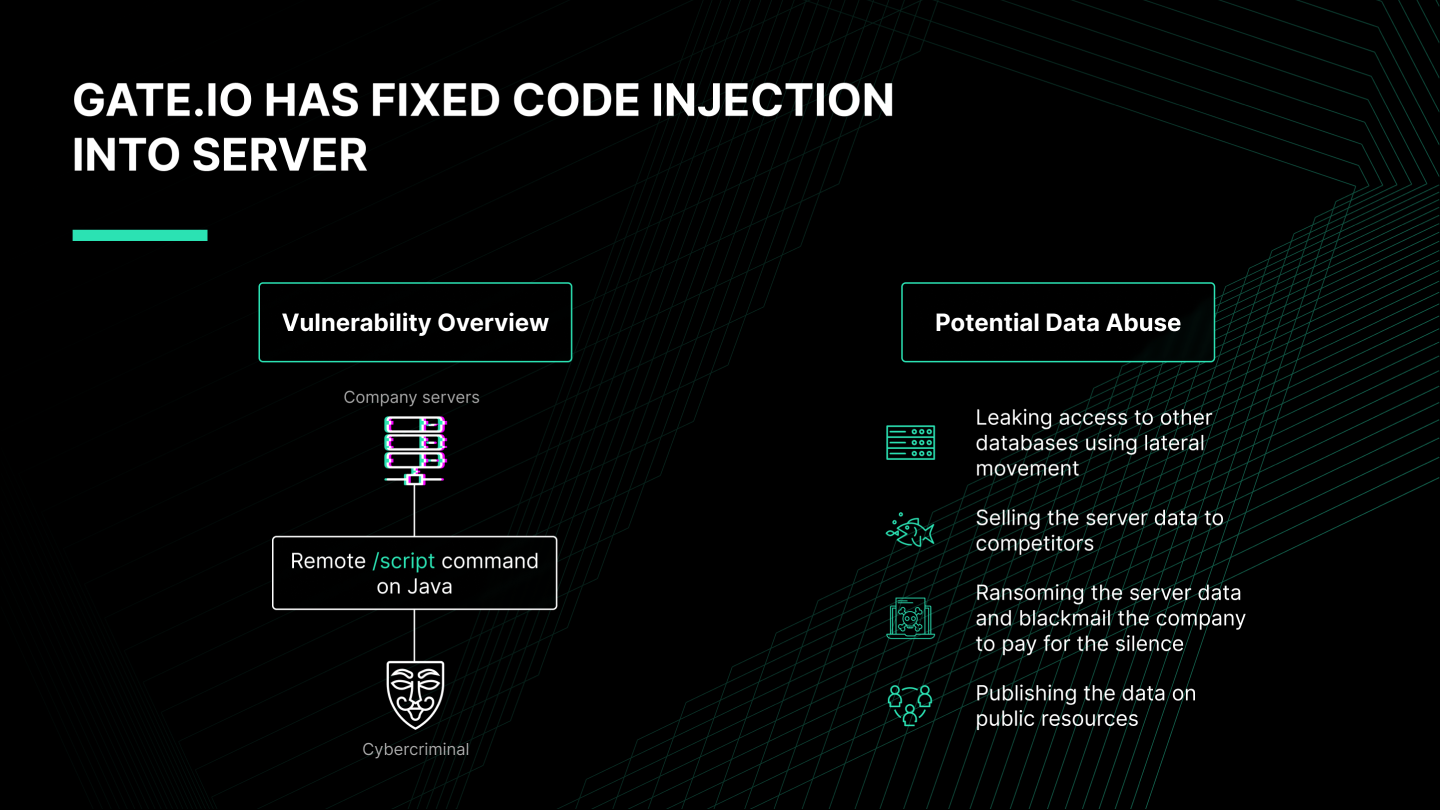
A hacker could inject a malicious script into the company server.
The attacker could do it remotely by using the /script command on Java.
Remote code execution is one of the most critical issues because it can compromise server data.
Potential Damage
The attacker could harm Gate.io in 4 ways:
- Gain access to other databases using lateral movement
- Sell the server data to competitors
- Ransom the server data and blackmail the company to pay for the silence
- Publish the server data on public resources
Resulting Measures

Once these vulnerabilities were identified, the Gate.io team expedited addressing them as quickly as possible to ensure the platform remains secure and users are protected from potentially malicious actors.
The company remains steadfast in its commitment to a safe and secure trading environment on its different platforms:
- Rated AAA by CER
- Verified by Blockchain Transparency Institute’s (BTI) market surveillance report
- Rated 4.5 by Forbes Advisor
- Became one of the first mainstream exchanges to be audited to show 100% Proof of Reserves
Publish Bug Bounty For Crypto Exchange
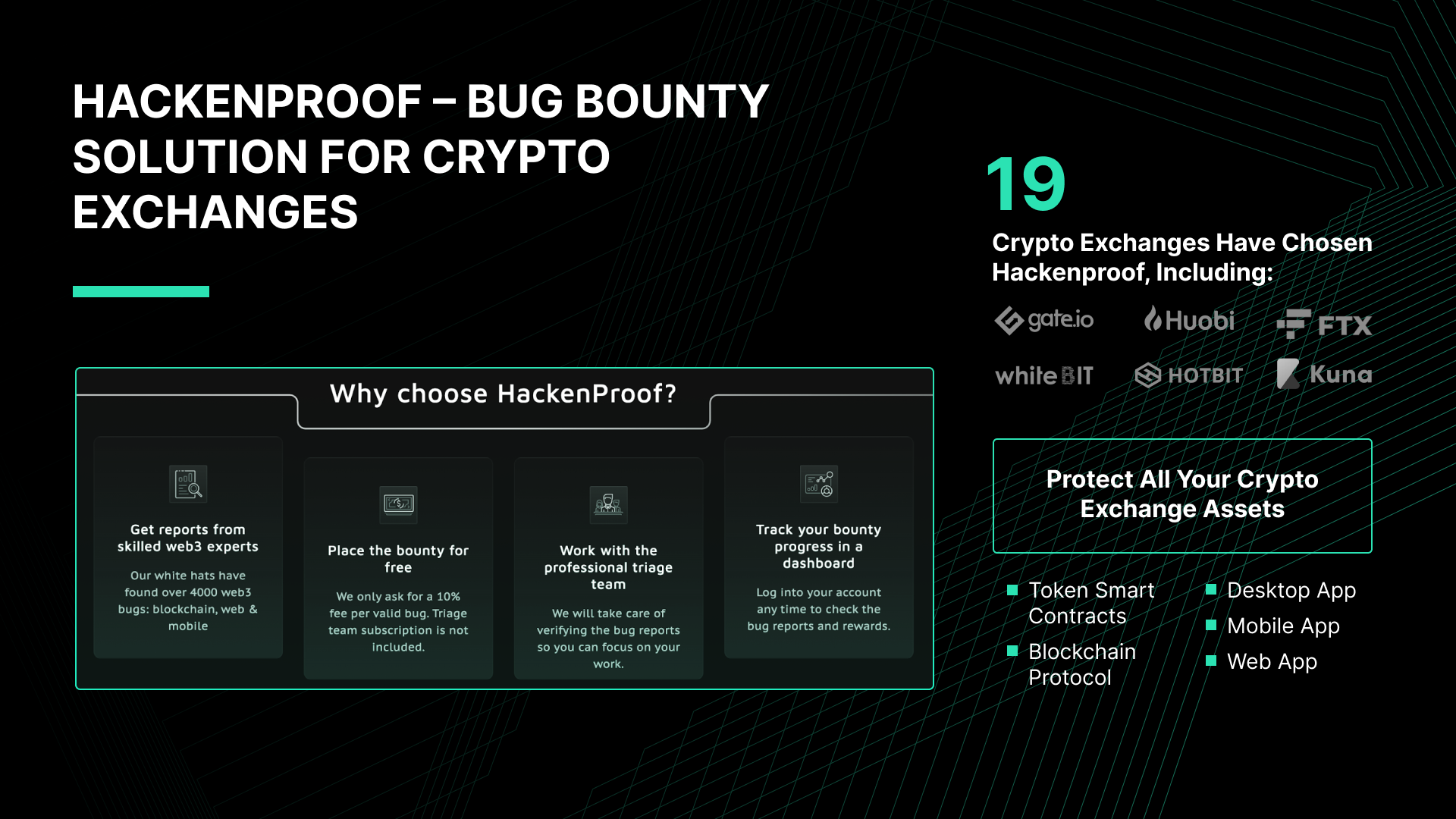
HackenProof is a bug bounty platform for crypto exchanges.
The platform connects crypto exchanges with ethical hackers.
Once whitehat hackers identify the exchange’s vulnerabilities, they deliver a report to the exchange.
Most of the reports are raw and need to be verified. For this reason, the HackenProof triage team takes on this responsibility and saves time for the exchanges. Then, the exchange developers fix these vulnerabilities.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.
Table of contents
Tell us about your project
Read next:
More related- Europe’s Top CEX–WhiteBIT–Trusts Hacken For Security
7 min read
Case Studies
- Coinmetro Crypto Exchange: Deep Security Approach
4 min read
Case Studies
- Hacken & KuCoin: pentests and bug bounties as CEXs’ keys to users’ trust
5 min read
Case Studies