Regulator-ready stablecoin security for launch and scale
End‑to‑end security, Proof of Reserves, real-time threat detection & response, and regulator-ready evidence – so you can launch, list, and scale with confidence.

Trusted by Web3 leaders, enterprises, and governments since 2017.








- 1671
- public security assessments delivered
- 3084
- critical-to-medium vulnerabilities prevented
- $430B+
- in assets verified across PoR audits
- ISO 27001
- certified
Security evidence mapped to your jurisdictions
Whether you issue algorithmic, collateralized, or fiat-wrapped tokens – you need a verified security posture to enter regulated markets. We provide security evidence mapped to each regime.
End-to-end security solutions for stablecoin issuers
How we work with stablecoin teams
Define scope
Scope and threat-model your stablecoin’s specific design (fiat-backed, crypto-collateralized, hybrid) and operating model.
Prioritize risks
Identify and sequence fixes across smart contracts, infra, and ops – so controls that protect the peg ship first.
Simulate threats
Emulate real attackers: design threat intel and scenarios, run tabletop → purple team → live red team drills in a safe, segmented setup.
Test security
Run deep audits and testing – from code reviews to pentests, cloud infra, wallet, and custody environments.
Prove solvency
Launch with an initial proof of reserves, then align cadence to your disclosure policy.
Embed compliance
Implement a unified, security-driven program for MiCA, VARA, DORA, CCSS, ISO27001 – backed by regulator-ready, evidence-based controls.
Retesting & Certification
Move to continuous assurance with bug bounties, retesting, and recurring proof of reserves.
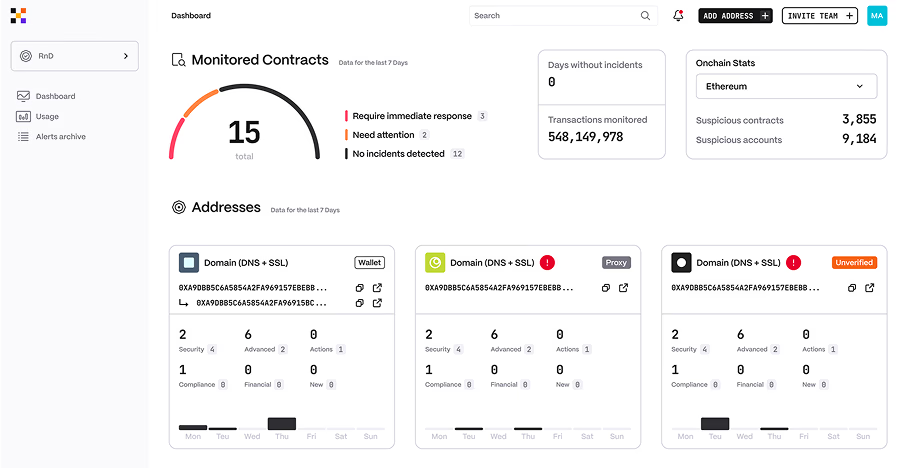
Continuous Monitoring with Extractor
Extractor by Hacken adds an extra layer of real-time visibility into your stablecoin's on-chain activity — tracking anomalies, suspicious transactions, and compliance-relevant events.
Key benefits:
- 1
Real-time on-chain threat detection
- 2
Continuous monitoring of risk and compliance signals
- 3
Configurable monitoring logic
What our clients say about Hacken
Hacken helps stablecoin issuers stay secure, meet current regulatory expectations, and navigate what comes next
Peg defense & token security
Mint/burn control and role management
Pause/circuit breakers and upgrade safety
Oracle architecture, fallbacks, deviation handling
Tokenomics/stability review (collateralized, algorithmic, hybrid)
Regulatory proofs
Proof of Reserves (continuous or scheduled)
Solvency attestations and reconciliation
AML/KYC & Travel Rule control evidence
ICT risk management mapped to ISO 27001, CCSS, DORA
Ecosystem protection
Apps/APIs and issuer portals
Custody/wallets and key management
Cloud & CI/CD and privileged access
Adversary emulations on real attack paths
Industry leaders rely on Hacken for security

Bybit Wins MiCAR License With Hacken's Security Evidence
Jul 18, 2025 2 min read

MEXC Exchange Security Reinforcement
Jun 18, 2025 2 min read

Europe's Top CEX, WhiteBIT, selects Hacken for Security
Jun 30, 2025 2 min read

EBSI APIs and Web Apps Secured After Hacken's Full-Scope Pentest
Sep 11, 2023 7 min read