KuCoin September 2020 Hack: Hacken Research
Last 2 weeks, the hottest crypto market topic was the KuCoin Hack. Our team highly values the need for user awareness of such threats, so here is a presentation of the research that was carried out by our specialists. Nevertheless, the issue of preventing such situations is of greater importance at the moment. Our experts have prepared recommendations on what to pay attention to and what to do to avoid such attacks.
Background
On September 25, 2020, the cryptocurrency exchange KuCoin was hacked. The estimated stolen cryptocurrency amount is more than $275 million in various cryptocurrencies.
On the official website, the KuCoin team explained that the hack was made because of a leakage of the private keys of KuCoin hot wallets. As a result, 1,008 BTC was stolen, along with 14,713 BSV, 26,733 LTC, 9,588,383 XLM, Omni, and EOS-based tether (USDT) worth $14 million, $153 million in ether and ERC20s, and over 18 million XRP.
All stolen USDT tokens have been blocked by the Tether team. Blocking is good for such hack cases. Thanks to these procedures, the exchange has already been able to return funds equivalent to $64 million. Nevertheless, it contradicts the main idea of cryptocurrencies, namely decentralization. For example, your bitcoins cannot be blocked in any way.
The hacker made withdrawals from the KuCoin hot wallets to the following addresses:
- ETH: https://etherscan.io/address/0xeb31973e0febf3e3d7058234a5ebbae1ab4b8c23
- BTC https://www.blockchain.com/btc/address/1TYyommJW3uhjhcnHhUSuTQFqSBAxBDPV
https://www.blockchain.com/btc/address/12FACbewf5Fy9nmeaLQtm6Ugo5WS8g2Hay
- LTC: https://live.blockcypher.com/ltc/address/LQtFoidy5TmLrPP77MZzgMRffqPsmRfMXE/
- XRP: https://bithomp.com/explorer/r3mZvvHVLPtRWAujzBsAoXqH11jhwQZvzY
- BSV: https://blockchair.com/bitcoin-sv/address/15mC7zKbLyErSKzGRHpy6gyqS7GyRpWjE
- XLM: https://stellarchain.io/address/GBM3PJWNB5VKNOFXCDTTNXPMUNBMYTLAAPYDIIKLHUGMKX7ZGN2FNGFU
- USDT: https://omniexplorer.info/address/1NRsEQRg5EjmJHbPUX7YADVPcPzCQBkyU7
- TRX: https://tronscan.org/#/address/TB3j1gUXaLXXq2bstiSMfjQ9R7Yh9DdDgK
As we found out from the transactions, the hacker sold the stolen cryptocurrency from the above addresses on decentralized exchanges like Uniswap and anonymized the stolen cryptocurrencies through the mixing services. A key advantage of Uniswap, a decentralized exchange, is that it enables users to retain full custody of their digital assets when exchanging them. However, hackers took advantage of its pros and misused the service platform.
The fact that a hacker uses decentralized exchanges negatively affects their reputation but at the same time confirms their reliability. Uniswap is completely decentralized and is a reliable service for exchanging cryptocurrencies. Everyone can exchange cryptocurrency without fear of blocking.
Why could the hack have happened?
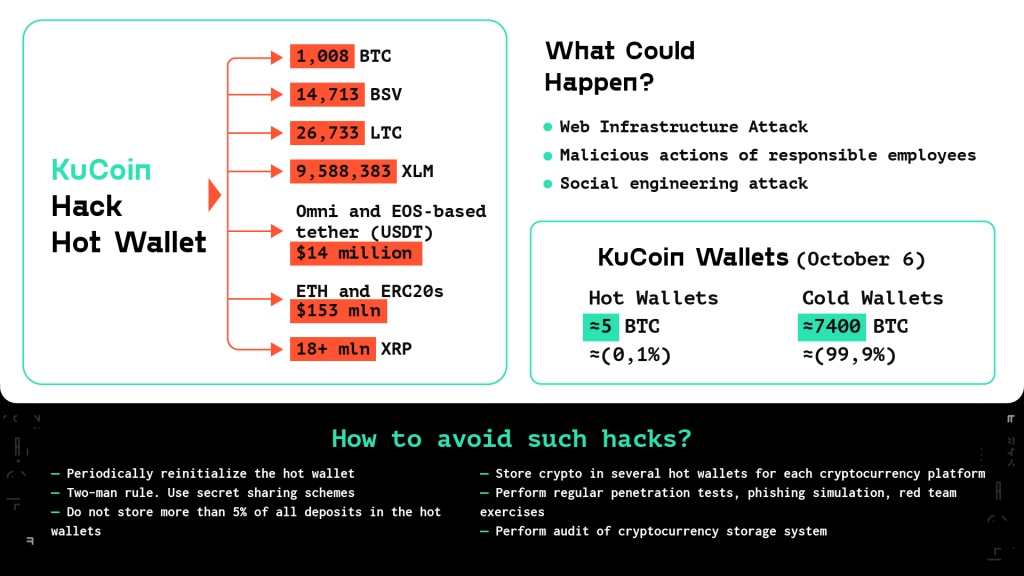
- Malicious actions of responsible employees.
This could have been done by someone from the exchange staff who had the appropriate access.
- Attack on web infrastructure.
An attacker could gain access to the exchange’s hot wallet services. Nevertheless, we consider such a version unlikely.
- Social engineering attack.
Hackers could obtain access to private keys as a result of a phishing attack by using exploits, viruses, and backdoors on employees who had access to private keys.
According to the twitter of Johny Lyu, the Kucoin team has found the suspects of the security incident. However, no specific reason was given.
Will KuCoin cover the losses?
Despite the exchange claiming to reimburse all losses to users, we can see that there are not enough funds on the identified KuCoin wallets to pay off the losses caused by the hack. In addition, the exchange did not have a secure asset fund from which to recover losses. Perhaps these funds are kept in bank accounts of the exchange or in “secret” wallets, but we do not have such information.
Talking about other exchanges, we can note that some of them really do have insurance funds, like Bittrex Digital Asset Insurance.
Who is at risk?
First of all, in the risk group we include exchanges with huge amounts of funds stored in the hot wallets. Some of them:
- Poloniex: https://etherscan.io/address/0xa910f92acdaf488fa6ef02174fb86208ad7722ba
- Coinoine: https://etherscan.io/address/0x167a9333bf582556f35bd4d16a7e80e191aa6476
- FTX: https://etherscan.io/address/0x2faf487a4414fe77e2327f0bf4ae2a264a776ad2 https://etherscan.io/address/0xc098b2a3aa256d2140208c3de6543aaef5cd3a94
How to avoid such hacks?
- Periodically reinitialize the hot wallet. KuCoin’s hot wallet key pairs have not been changed for 3 years. The first transactions were made on September 17, 2017.
- Two-man rule. Use secret sharing schemes. One of the most popular ways is to use Shamir’s Secret Sharing scheme.
- Do not store more than 5% of all deposits in the hot wallets. The other 95% must be stored in a cold wallet.
- Store crypto in several hot wallets for each cryptocurrency platform. Each wallet must have its own private key.
- Perform regular penetration tests, phishing simulation, red team exercises.
- Perform audits of the cryptocurrency storage system that is included in SOC2 and/or ISO27000 auditing procedures: https://gemini.com/blog/gemini-completes-soc-2-review-a-worlds-first-for-a-cryptocurrency-exchange-and-custodian
Conclusion
The KuCoin exchange hack showed us that some exchanges have to pay more attention to common security standards. Some respectable exchanges have already passed SOC-2 audits. SOC 2 examination on an annual basis demonstrates that an exchange cares about the safeguarding of its clients’ data and deposits.
Regardless of the reason for the hack, we recommend that exchanges adhere to generally accepted rules for storing client funds and perform regular audits.
Also, we can see that a hacker decided to exchange stolen cryptocurrencies on DEX services such as Uniswap. Unlike centralized exchanges, DEXs can’t block their users’ funds — only specific projects can block their tokens (for example Tether). We feel that this increases user confidence in the reliability of decentralized services.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.
Table of contents
Tell us about your project
Read next:
More related- Ripple Hack Explained: A Deep Dive into the Recent XRP Heist
3 min read
Insights
- Understanding the Recent Hack on Ledger Connect Kit
2 min read
Insights
- KyberSwap’s $47M Reentrancy Attack: A Deep Dive into the Exploit
2 min read
Insights