How Sensitive is Your Non-Sensitive Data
In today’s digital world keeping private data like emails, phone numbers, names, addresses or IPs secure from theft or vulnerability is not as easy as putting a lock on a door. With the ability to share, store and transmit sensitive data across computer systems we have created another problem. Even taking all the precautions doesn’t guarantee the safety of your personal information. There are many ways that your data or online account info can be stored by another individual or in a company’s data management system, which makes it vulnerable to data leakage.
Once you’ve decided to share even a tiny bit of your personal information, your privacy is over. One might think that such non-sensitive data like emails is no big deal, however, this can potentially lead to phishing attacks and consequently to a data breach. One of the most representative sensitive data examples is credit card information but that doesn’t mean that email addresses don’t also need to be protected.
October Findings: “Non-sensitive Data” Databases with more than 120M Records
It is not a difficult task to gain access to databases containing the personal information of individuals. Although the data provided there is not necessarily considered sensitive, the fact that it can be accessible by anyone including cybercriminals is shocking. In October we have located and reported three large databases, with more than 120 million records combined:
- The first one was simply called “database” and contained what looked like scraped LinkedIn related data. We found 49 million records in total that were hosted by two IPs. Data fields included full name, personal email, location, skills, employment history (all taken from their LinkedIn profile). We could not identify the owner of the MongoDB hosted database due to the lack of recognizable patterns in the dataset structure.

- The second database was operated by a Florida-based company, which specializes in job search aggregation. There were more than 22 million records hosted on a public Elasticsearch.
Data included email, IP, name and a potential area where the candidate would seek a job.

- The third database contained around 48 million records with information on a person’s name, work email, phone, and employee details.
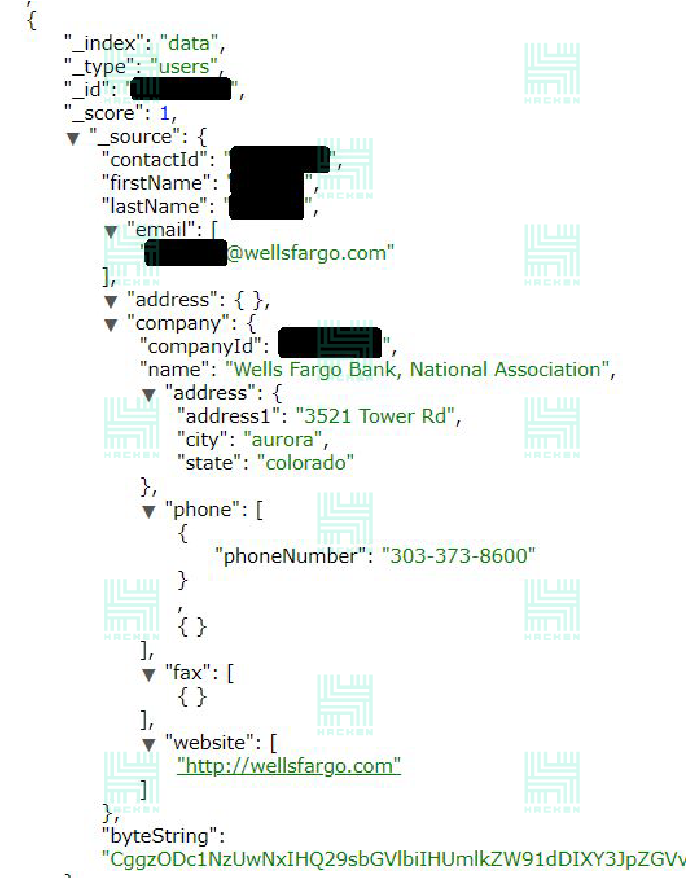
However, part of this data is now uploaded to HaveIBeenPwnd system, so you can check whether your profile has been scrapped.
What’s interesting is that all these databases did not contain any sensitive personal data such as credit card details or passwords but they did contain a lot of private information like an individual’s professional background, name, phone number, email address, address, and even their IP. The question is whether it’s that safe or not?
Scraping Your Data
Nowadays information is priceless and while some think of legal ways to gather it, malicious users are always searching for new methods to bypass the sensitive data security in order to use the private information of individuals for their own purposes. One of the most widely used methods to gather data from the Internet is called web scraping or data scraping.
The term refers to the use of a variety of methods for collecting data from the Internet using software that simulates user browsing behavior. While it may not seem that serious, data scraping is quite a controversial topic due to the risk of sensitive data being exposed and the breach of confidentiality. It is important to note that the web scraping can easily be confused with web crawling which is an entirely different thing. In the case of web crawling, the targeted data on web pages is being downloaded automatically using applications called crawlers (for example, Googlebot). The web crawling process involves the creation of searchable indexes or databases and is generally used to build search engines.
How Not to Be Scrapped: Basic Steps
Data scraping is an easy way to steal confidential data from web pages that have not taken the necessary steps to ensure sensitive data protection. There are things all of us can do to ensure our private information won’t be stolen by cybercriminals or scammers. Here are some of them:
- Try to provide only the bare minimum of required information when creating a new profile or account online.
- Analyze whether the data you plan on making public can be used to harm you in any way.
- Use different email addresses and passwords for your bank than you do for social network accounts.
- Consider any other private information you’ve already shared online and whether this information combined with the one you’re making public now can be potentially risky.
- Always read the Terms of Service before you agree to them. Check what kind of your private information you agree to share with other websites or applications.
- Contact the website’s support to ensure that their sensitive data storage is reliable.
What is the GDPR?
When you hear the term ‘personal data’ then the GDPR or General Data Protection Regulation applies immediately. Enforced from 25th May 2018, the law provides data protection and privacy for all individuals within the European Union and European Economic Area as well as their confidential data exported outside these areas. It means that gathering, processing, selling and buying private information of citizens from those areas is illegal without their prior written consent. However, the GDPR can also apply if a business is operating in the USA if it uses private information of European Union citizens. Non-compliance and exposure of the GDPR sensitive data (name, address, phone number, email address, IP, job title, cookies etc.) can lead to significant fines of up to 20 million euros.
Conclusion
In conclusion, many aspects of our lives are now connected through the internet including social networks, cloud services, bank accounts, emails, online shops, etc. This means that a lot of your confidential information is potentially at risk. You may consider data such as email addresses, phone numbers or IP addresses to be less important and of lower risk than credit card details but when you think objectively about what your emails contain, the reality is that we often keep all our info in one place.
When you scan through your emails you will often see that they actually contain a lot of sensitive personal data such as contacts, tax forms, invoices, photos, reset passwords for every one of your accounts or even credit card PINs! We are often unaware that a malicious actor can easily gain access to all that data and take advantage of it just by hacking an email address. Cybercriminals can use that private information to steal your identity and make financial transactions in your name, including taking out loans and opening bank accounts etc. By getting access to your calendar, planner or travel itinerary it gives them the inside knowledge of when your house might be empty, so they can break in or potentially do something even worse.
Don’t let the idea that this only happens to celebrities or important CEO’s mislead you, the reality is that one in four email accounts get hacked. Forewarned is forearmed. With all that said, do you still think that your non-sensitive data is that non-sensitive?
How Hacken can Help
At Hacken, we take security extremely seriously, and all the checks are performed according to the highest standards. If you have any questions about the topic or need a consultation, feel free to contact our Team!
Read also:
How Blockchain Can Help SME Challenge Legacy Rivals
Phishing of Crypto Hodlers, Traders, and Stock Exchanges
More than just a Data Breach: a Democratic Fundraising Firm Exposure
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.

Table of contents
Tell us about your project
Read next:
More related Prompt Injection Attacks: How LLMs Get Hacked and Why It Matters
Prompt Injection Attacks: How LLMs Get Hacked and Why It Matters6 min read
Discover
 LLM Red Teaming: A Playbook for Stress-Testing Your LLM Stack
LLM Red Teaming: A Playbook for Stress-Testing Your LLM Stack5 min read
Discover
 5 Circom Security Pitfalls That Can Break Your Proofs
5 Circom Security Pitfalls That Can Break Your Proofs10 min read
Discover