Flash Loan Attacks: Risks & Prevention
Flash loans have become an increasingly popular feature in decentralized finance (DeFi) ecosystems, offering individuals and businesses quick access to large amounts of capital without collateral. With flash loans, borrowers can receive funds that are immediately returned to the lending platform at the end of a single transaction block.
However, the ease of access to these loans has also led to an increase in flash loan attacks, which are a type of exploit where malicious actors can take advantage of the temporary liquidity provided by flash loans to manipulate prices or steal funds. These attacks can have devastating consequences for both individuals and DeFi platforms, causing millions of dollars in losses.
In this article, we will explore the risks associated with flash loan attacks and provide actionable steps that developers and entrepreneurs can take to protect themselves and their users. We will examine real-world examples of flash loan attacks and discuss how these attacks can be prevented through improved security measures and best practices.
How Do Flash Loan Attacks Work?
Flash loan attacks rely on the temporary liquidity provided by flash loans to manipulate the price of a cryptocurrency, exploit vulnerabilities in a DeFi smart contract, or steal funds from a protocol.
To execute a flash loan attack, an attacker typically follows a three-step process:
- Borrowing: The attacker takes out a flash loan from a DeFi platform and borrows a large sum of cryptocurrency without providing any collateral.
- Manipulating: Using the borrowed funds, the attacker manipulates the price of a targeted cryptocurrency or exploits a vulnerability in a DeFi smart contract.
- Repaying: The attacker repays the flash loan, usually within the same transaction block, and returns the borrowed funds to the lending platform.
The key to the success of a flash loan attack is the ability to repay the loan within the same transaction block. This allows the attacker to take advantage of temporary liquidity without providing any collateral, which makes it difficult for lending platforms to protect themselves against these types of attacks.
Simple Flash Loan Example
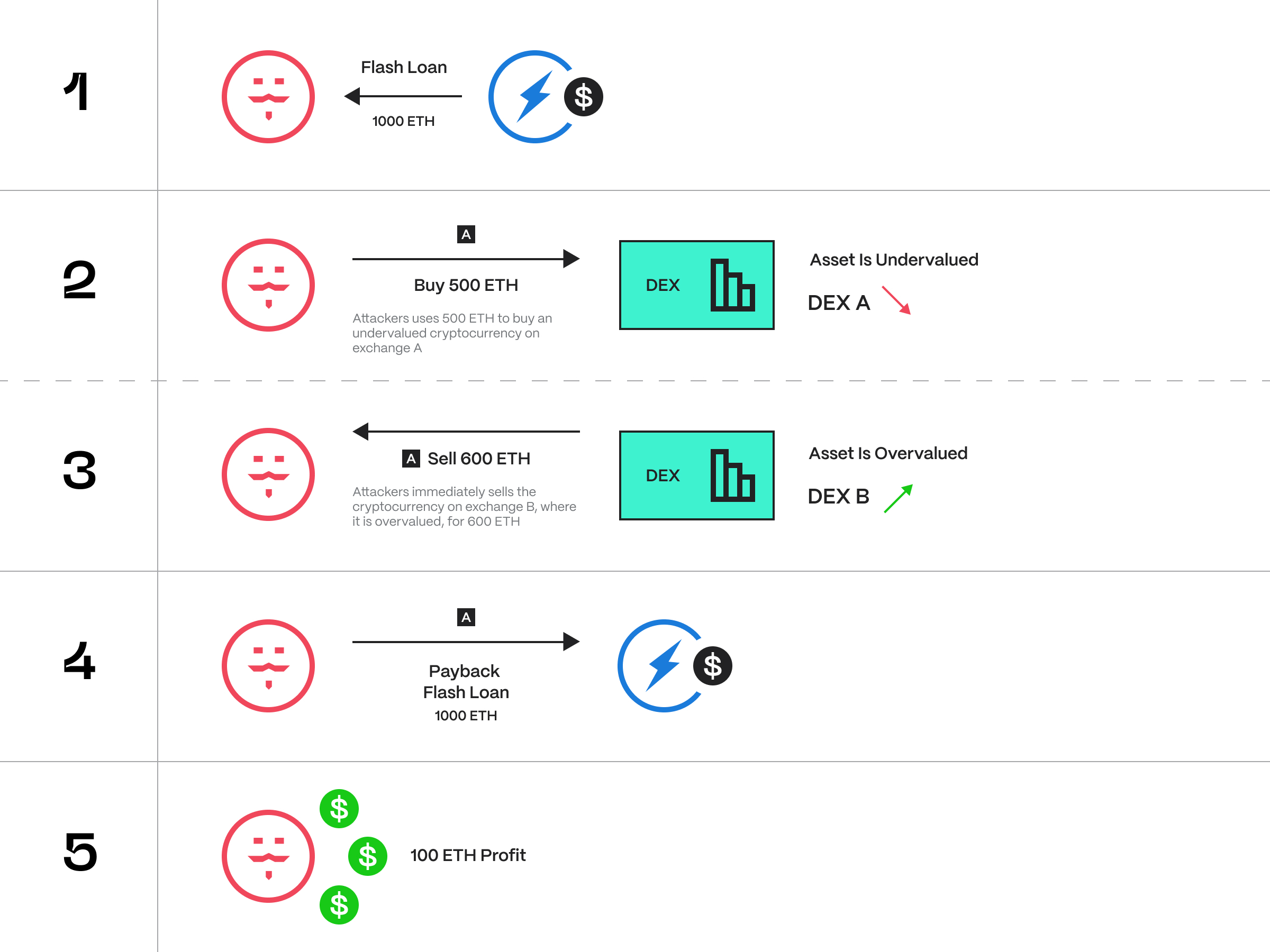
Let’s say an attacker wants to exploit a vulnerability in a DeFi smart contract to steal funds. The attacker first takes out a flash loan of 1000 ETH (worth around $1.8 million at the time of writing) from a lending platform. The attacker then uses 500 ETH to buy a cryptocurrency that is undervalued on one exchange and overvalued on another exchange.
For example, let’s say that the cryptocurrency XYZ is undervalued on exchange A, where it is trading at 1 ETH = 10 XYZ, and overvalued on exchange B, where it is trading at 1 ETH = 12 XYZ. The attacker uses the 500 ETH to buy 5000 XYZ on exchange A, where it is undervalued, and then immediately sells the 5000 XYZ on exchange B, where it is overvalued, for 600 ETH.
Now the attacker has 1100 ETH: the original 500 ETH plus the 600 ETH profit from the arbitrage trade. The attacker repays the flash loan of 1000 ETH, plus any fees and interest, and keeps the remaining 100 ETH profit.
This is an example of a flash loan arbitrage attack. This attack takes advantage of price discrepancies between different exchanges to generate profit. Arbitrage is not inherently malicious; many traders use flash loans for legitimate purposes. However, it becomes malicious when used to steal funds from the protocol by exacerbating a vulnerability in a DeFi Smart contract.
Flash Loan Attack Types
It’s worth noting that this is just one example. A real-world flash loan attack could take many different forms depending on the specific vulnerability or manipulation tactic being used.
Price manipulation: Attackers can use flash loans to manipulate the price of a cryptocurrency by artificially inflating or deflating its value. This can cause significant losses for traders who have placed orders based on manipulated prices.
Arbitrage: Attackers can exploit price discrepancies between separate decentralized exchanges (DEXs) by using flash loans to execute arbitrage trades. While this attack is not necessarily malicious, it can still cause losses for legitimate traders.
Smart contract exploits: Attackers can use flash loans to take advantage of vulnerabilities in DeFi smart contracts, such as reentrancy bugs or integer overflow errors. This can allow them to steal funds from the protocol or execute other attacks.
It’s essential to highlight that flash loans, in most cases, are not vulnerabilities in and of themselves. Attackers leverage them to quickly acquire substantial sums of money, which can consequently cause significant alterations to the impacted systems.
Real-World Cases Of Flash Loan Attacks
Euler Finance: $197m (March 2023)
One of the latest and, at the same time, the biggest hacks. The hacker exploited an error in the rate calculation within the platform itself.
Vulnerability explanation: Euler Finance platform users borrow and lend using two main types of tokens: eTokens (representing collateral) and dTokens (representing debt). A hacker exploited a flaw in the platform’s eToken function, which caused an incorrect conversion of borrowed assets to collateralized assets. The hacker involved two primary on-chain entities: a front-running bot and their personal wallet. They received initial funding from Tornado Cash, a sanctioned mixer, for gas fees and to create the necessary contracts.
Attack explanation: The hacker took a flash loan of about $30 million in DAI from the DeFi protocol Aave. They deposited $20 million of the DAI into Euler’s platform and received a similar amount in eDAI tokens. By leveraging the platform’s borrowing capabilities, the hacker borrowed 10 times the original deposited amount. They used the remaining $10 million in DAI to repay part of the acquired debt and continued borrowing until the flash loan was closed.
Conclusion: As a result of the attack, Euler lost around $197 million worth of cryptocurrency across DAI, wBTC, stETH, and USDC. Euler’s native token, EUL, also experienced a decline of more than 45%.
P.S. Not long after the attack, the hacker restored the funds to the platform.
Cream Finance: $130m (October 2021)
In October 2021, CREAM Finance suffered one of the largest DeFi hacks in history, with losses exceeding $130 million.
Vulnerability explanation: The vulnerability exploited in this attack was related to CREAM’s yUSDVault. The attacker’s goal was to mint a significant number of crYUSD tokens and exploit a flaw in the vault to double the perceived value of these shares.
Attack explanation: During the attack, two accounts took out flash loans from MakerDAO and AAVE. The DAI from MakerDAO was deposited into Curve’s yPool to create yDAI, which was used to mint yUSD. The ETH from AAVE served as collateral to borrow additional yUSD. The second address transferred approximately $500 million in yUSDVault tokens to the first address.
Repeating this process multiple times, the first address accumulated roughly $1.5 billion in crYUSD and $500 million in yUSDVault. The attacker redeemed the $500 million yUSDVault for yUSD, reducing the total supply of yUSDVault tokens in the vault to around $8 million. The attacker then deposited approximately $8 million in yUSD into the vault, effectively doubling its overall value.
CREAM’s PriceOracleProxy for yUSDVault tokens determined their value by dividing the vault’s total value by the total supply of yUSDVault tokens. By reducing the total supply of yUSDVault to around $8 million and depositing $8 million in yUSD into the vault, the attacker essentially doubled the perceived value of yUSDVault shares (crYUSD).
Conclusion: The first attacker address possessed $1.5 billion in crYUSD, which the vault now valued at $3 billion. The attacker used $2 billion and the previously withdrawn $500 million to repay their flash loans. The remaining $1 billion in crYUSD allowed the attacker to drain CREAM’s $130 million in available assets.
bZx: $1m (November 2021)
The hack was quite sophisticated, involving two distinct attacks. After targeting the first vulnerability, the hacker swiftly executed a second attack using a different method.
Vulnerability explanation: The core vulnerability in the first attack was BZx’s reliance on a single oracle for price determination, which allowed the attacker to manipulate the collateral pool using a flash loan. In the second attack, the vulnerability was BZx’s usage of the Uniswap spot price as an oracle, which was manipulated to inflate the value of the collateral.
Attack explanation: In the first attack, the hacker borrowed $10 million in ETH through a flash loan and used it to manipulate the collateral pool by taking a 5x short position on the ETH-wBTC trading pair, causing significant slippage. In the second attack, the attacker used a flash loan to inflate the Uniswap Synthetix USD price to $2, then deposited sUSD into BZx as collateral to borrow more ETH than they should have been allowed.
Conclusion: These attacks on BZx exposed the platform’s vulnerabilities, particularly its reliance on a single oracle and the susceptibility of its collateral pool to manipulation. The attacks resulted in losses of over $985K, highlighting the need for robust security measures and the importance of using multiple trusted oracles for price determination.
How To Prevent Flash Loan Attacks?
Considering the earlier examples, we can compile a list of key methods to safeguard against flash loan attacks.
- Use reentrancy guards to prevent unexpected contract calls. Use proper access control mechanisms, such as OpenZeppelin’s Ownable, to limit critical functions. Use well-tested libraries and frameworks like OpenZeppelin for contract development.
- As these attacks originate from external smart contracts, it’s prudent to validate the addresses allowed to utilize flash loan functionalities. Ensure that external contract calls are authentic and secure and limit interactions exclusively to trusted contracts.
- Employing thorough third-party smart contract auditing and validation is always a valuable security measure. Conduct comprehensive testing to identify potential vulnerabilities and collaborate with reputable auditing firms to review your contracts.
- Utilize a variety of oracles to obtain the most precise and safe price information, considering that some oracles might be vulnerable. Implement time-weighted average price (TWAP) mechanisms to minimize the risks tied to price manipulation.
- Regularly review and stay current with DeFi security best practices and vulnerability reports.
Final Thoughts
Flash loan attacks are a significant threat to DeFi protocols, as they can allow attackers to exploit vulnerabilities in smart contracts and steal funds. However, by implementing best practices such as reentrancy guards, access control mechanisms, and third-party auditing, developers and entrepreneurs can mitigate the risks of theft.
It’s also important to stay current with the latest security best practices and vulnerability reports, as the DeFi landscape is constantly evolving. By remaining vigilant and proactive in addressing potential threats, we can help to build a safer and more secure decentralized financial system for everyone.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.
Table of contents
Tell us about your project
Read next:
More related- Lightning Network: Everything You Need To Know
8 min read
Discover
- Understanding EigenLayer & Ethereum’s Restaking
8 min read
Discover