DDoS attacks: mechanism, damage, and prevention
Distributed denial of service (DDoS) attacks have been heavily affecting businesses for the last 20 years. They have become one of the most powerful instruments in the hands of malicious actors striving to bring down targeted resources by overloading them with too much traffic. The malicious or unusual traffic may include requests for connections, incoming messages, or fake packets. DDoS attacks may vary in terms of sophistication depending on the capacity of the victim’s servers and attackers’ qualifications.
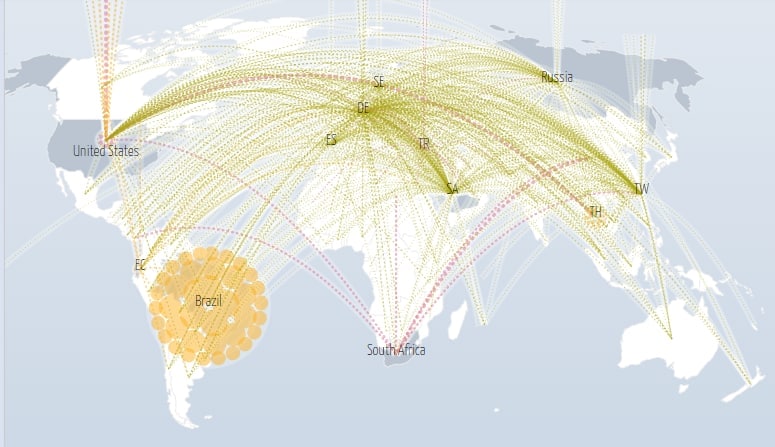
There are resources providing daily information on DDOS attacks and their geographic distribution. For example, let’s look at the DDOS map provided by Digital Attack Map. We see that as of April 2021, the DDoS attacks are mostly targeting 3 regions including the USA, Brazil, and Europe.
There are 7 Open Systems interconnection model layers included in the Internet network connections. A particular type of DDoS attacks is designed to target specified layers, for example:
- Layer 3 (Network Layer). Smurf Attacks, IP/ICMP Fragmentation, ICMP Floods, and spoofed-packet flood and UDP attacks;
- Layer 4 (Transport Layer). SYN Floods, TCP Connection Exhaustion, and UDP Floods.
- Layer 7 (Application Layer). HTTP-encrypted attacks.
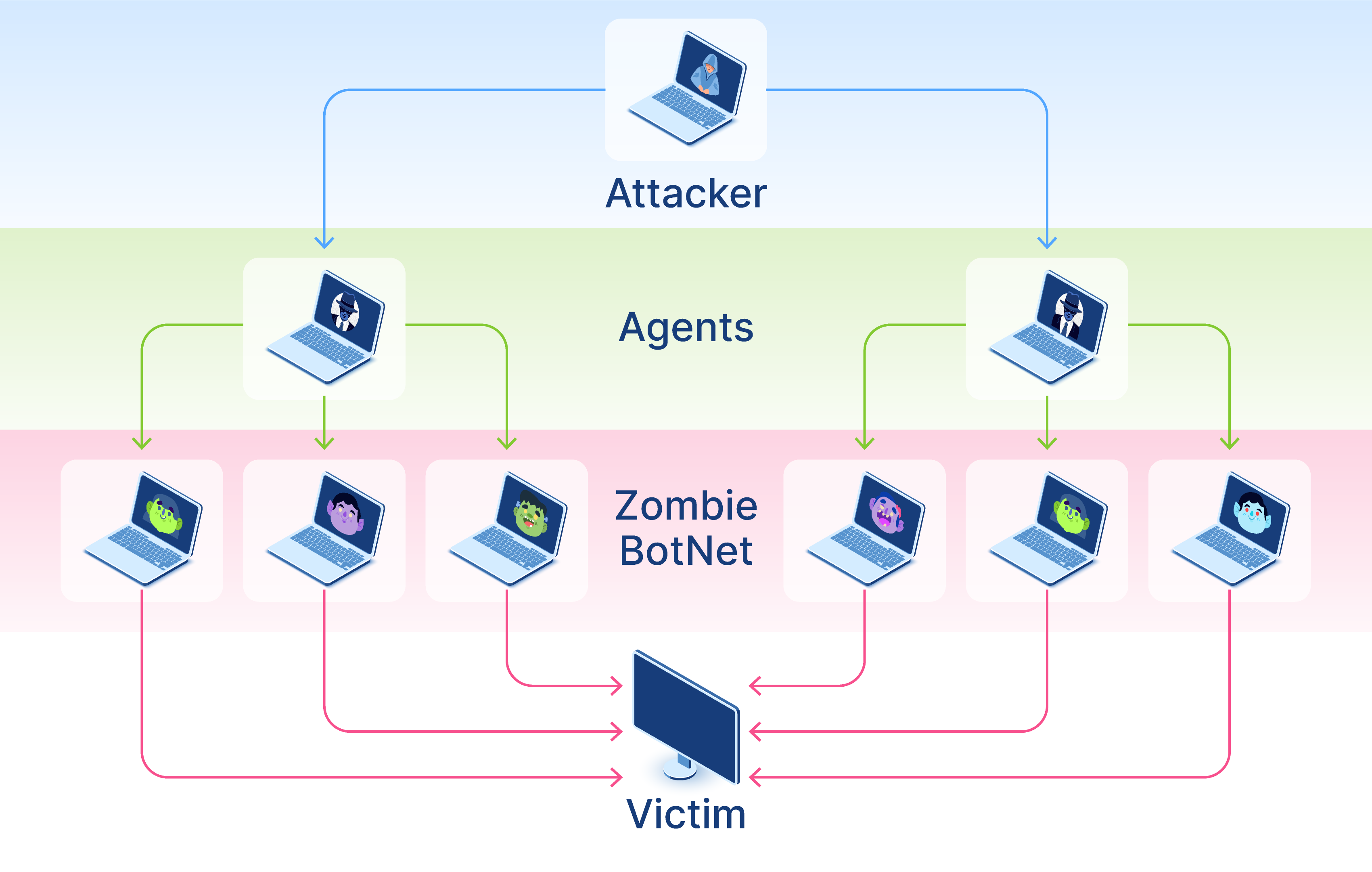
In most cases, hackers commit DDoS attacks using a network of hacked computers that may be also referred to as zombie computers. Malicious actors add new devices to their botnet by carrying out phishing attacks, using mass infection techniques, and performing malvertising crimes. These devices are used by malicious actors to flood targeted resources so that the amount of data sent is greater than the victim’ bandwidth capacity. The network controlled by hackers may encompass thousands and even millions of zombie computers. The function of the botnet is to send legitimate HTTP or HTTPS requests to overwhelm the targeted web server. Taking into account the amount of time required by a hacker to develop a network of zombie computers, cybercriminals and malicious groups have developed the business model under which botnets are sold or leased to hackers on the black market. However, in some cases, malicious actors may misconfigure computers or trick users to become a part of a botnet even without the need to hack their computers.
The list of indicators of an experienced DDoS attack may include internet disconnection, slow access to files, issues when accessing websites, the large number of spam emails, etc. In most cases, victims cannot easily detect a DDoS attack.
There are 3 basic types of DDoS attacks:
- Volume Based Attacks (the network’s bandwidth is overwhelmed by the massive volume of traffic sent). May have either a long-term or burst natures depending on the hacker’s purposes and capabilities;
- Protocol Attacks (are focused on the exploitation of server’s resources vulnerabilities);
- Application Attacks (target specified web applications, may be viewed as the most sophisticated type of DDoS attacks).
DDoS attacks take place since hackers succeed in exploiting 3 key vulnerabilities including technical debt, monocultures, and system complexity that are attributable to most businesses.
- Monocultures: the replication and frequent use of a single service by IT departments. As a result, hundreds of the same instances may exist. As a result, malicious actors may use a particular malware to simultaneously target many systems;
- Technical Debt: businesses often neglect the importance of following the security best practices when developing new solutions simply to save some time and resources. When companies skip the completion of specified security steps and fail to pay the so-called debt back, then hackers can easily compromise vulnerable systems to add them to their botnet network;
- System Complexity: the more interconnected systems the companies develop, the more difficulties they face when trying to control them. When a company loses control over information flow due to system complexity, it becomes vulnerable to DDoS attacks.
To remain undetected malicious actors manipulate DNS traffic by exploiting various IP addresses assigned to a resource. The botnets rapidly swap IP addresses at random. This method is called Fast Flux DNS.
DDoS attacks are not performed for fun. There are objective factors boosting hackers’ motivation to commit such wrongdoing. The key driver behind DDoS attack is financial stimuli. An attacker requires a victim to pay a solid ransom to stop the attack. DDoS attacks may be also used by businesses to cause financial damage to their competitors. In this case, it is one of the methods of wars between competitors. You may find more info on methods used by companies to beat competitors in the following article. DDoS attacks are also a form of demonstrating disagreement with national policy by crashing government websites. In this case, there are ideological considerations behind DDoS attacks. DDoS attacks are a popular tool to hamper the economic development of certain countries.
Damage to businesses caused by DDoS attacks
The scale of damage experienced by a company due to DDoS attacks depends on their complexity and nature. In most cases, these attacks target websites, thereby, crashing their functioning. As a result, companies that sell goods and services via websites may lose not only money but also reputation. The website downtime may also affect the company’s SEO that will lead to a decrease in the number of new clients. The longer a website is unavailable due to an experienced DDoS attack, the bigger the damage faced by a company. Frequent DDoS attacks faced by a company may also affect its relationships with a hosting provider unless it takes measures to prevent such challenges in the future.
Often, DDoS attacks are simply an instrument in the hands of hackers to put out companies’ security systems thereby creating favourable conditions for committing further cyberattacks. Also, the restoration of the normal functioning of web resources requires companies to spend a significant amount of time. As a result, their IT specialists cannot work on implementing other projects until they address all issues caused by DDoS attacks.
Experienced DDoS attacks may have a negative impact on businesses’ partnership relationships. Taking into account the interconnections between different economic players and the globalization of supply chains, a DDoS attack on a particular player may cause the disruption of the whole chain and may also lead to the compromise of data of other companies. That is why businesses are interested in cooperating only with reliable partners with a clear history of data compromises or system crashes. When speaking about the public-private partnership, government institutions partner only with the companies that are highly resistant to cyberattacks, including the DDoS ones. The businesses that have recently fallen victim to DDoS attacks have low chances to collaborate with the government. Overall, DDoS attacks cause serious damage to businesses and the slower their response to them, the higher the risks that this damage may become irreversible.
DDoS attacks: statistics and overview of recent incidents
The year 2020 set up a few records of DDoS activities:
- The number of committed DDoS attacks crossed the 10 million level and every month more than 800,000 attacks took place;
- The year to year increase in the number of DDoS attacks equalled 20% in 2020.
- SYN-floods amounted to 79.7% of all DDoS attacks;
- The average attack duration was close to 40 minutes. However, there were also attacks that could last up to a few days;
- The average volume of data used to commit the attack was close to 1 Gbps;
- The proportion of DDoS attacks over 10 Gbps was close to 20% in 2020 compared to 10% per cent in 2019;
- >80% of attacks were using 2+ vectors ;
- China (1.6 mln botnets), the USA (1 mln botnets), and India (1 mln botnets) were the leaders by the number of functioning botnets;
- The average cost of 1 experienced DDoS attack for an enterprise amounted to $50,000 in lost revenue;
- The probability of a repeat attack within 24 hours after the initial attack was close to 25%.
Let us view some of the recent major DDoS attacks:
In October 2020, Telenor Norway experienced a DDoS attack that lasted 3 hours. Close to 400 Gbps of traffic were directed to the entity’s web resources. The attack was carried out by malicious actors who required the company to pay as a ransom 20 bitcoins. The company refused to pay a ransom, however, its major services were not affected. The attack caused the temporary crash of emails and websites but the crucial services including voice calls and SMS were not affected. The company did not experience huge damage only due to the hard efforts contributed by its tech support. The reasons behind the hackers’ choice to attack the Norwegian telecom provider was related to the attractiveness of the information it stored. Namely, Norwegians demonstrate high demand for iGaming services but the country’s regulators forbid this activity. That is why people in Norway use telecom providers to register on foreign iGaming platforms.
In February 2020, the cryptocurrency exchange Bitfinex reported on the experienced DDoS attack that made it offline for close to 1 hour. Malicious actors were trying to exploit several platform features concurrently to increase the load. The exchange used various protection mechanism to protect itself from DDoS attacks and that is why the experienced damage was minimal. Almost simultaneously, the cryptocurrency exchange OKEx experienced 2 DDoS attacks of 200 and 400-gigabyte severity respectively. The attacks did not cause any damage to the exchange.
In September 2020, powerful DDoS attacks were launched against the Hungarian financial institutions and the telecom company Magyar Telekom. According to the information provided by Magyar Telecom, the volume of data traffic used to commit the attacks was 10 times higher than ever recorded in Hungary. Russian, Chinese, and Vietnamese hackers were likely to stand behind the attacks. As a result, the Hungarian financial entities including OTP faced temporary disruption of operations.
In August 2020, the New Zealand stock exchange (NZX) was offline for 2 consecutive days due to the experienced DDoS attack. The attack affected the exchange’s network connectivity and since the NZX main website was down the exchange could not publish any announcements. However, according to the statement made by New Zealand’s financial regulator, the Financial Markets Authority, the exchange did not prepare itself for potential DDoS attacks and did not take the required preventive measures to avoid the incident. The exchange’s servers lacked adequate DDoS protection.
Thus, companies representing different sectors of the global economy suffer from DDoS attacks. However, the level of damage experienced by businesses due to DDoS attacks varies depending on their DDoS resistance capacity. The better a company is prepared for a potential DDoS attack, the higher the possibility that this attack will not cause any visible damage to its functioning.
How to protect your business against DDoS attacks?
There are measures companies can take to mitigate the negative impact of DDoS attacks or fully prevent them. To mitigate the financial and operational implications caused by a DDoS attack companies need to know how to detect them. Here is the list of common indicators of this type of cyberattack:
- unavailable or slow servers;
- multiple requests coming from the same IP address within a short period;
- 503 service unavailable when no maintenance processes take place;
- abnormal increase in the volume of traffic.
Measures to be taken to prevent DDoS attacks:
- regular network reconfigurations to reveal weaknesses via internal and external audits;
- staff training aimed at teaching employees on how to detect a DDoS attack and how to act upon detecting such security incidents;
- identification of vulnerable assets such as cloud services, data centres, traditional installed services, and infrastructure servers;
- information backup;
- development of risk analysis mechanisms;
- control of access to the application or resources: the ports, protocols, and application the interaction with which should not take place needs to be prohibited to access the resources. This measure will mitigate the size of potential damage caused by a DDoS attack;
- cooperation with DDoS mitigation service vendors;
- the use of products making web resources resistant to DDoS attacks.
The last point is of the greatest importance for SMEs since the bandwidth and computing power of their servers often is not sufficient to deal with modern DDoS attacks. In April 2021, a new highly promising project disBalancer announced its future entry into the market with the solution that makes businesses resistant to DDoS attacks by allowing them to utilize the free computing power and bandwidth of the devices of users who are connected to the system. Thus, when the client’s web resources experience a spike in traffic, the malicious traffic is distributed in the system so that the client’s web resources continue functioning in a normal way. Here we can see how disBalancer works.
There will be main nodes deployed in each region to which users will be able to connect. When the malicious traffic comes through their resources, they will earn tokens, DDOS tokens. The solution offered by disBalancer is likely to be very effective since one of the main reasons behind businesses’ failure to protect against DDoS attack is the lack of computing power and bandwidth to process high volumes of incoming traffic.
Overall, DDoS attacks have become widespread in modern business and although they may be committed for various purposes, they cause very negative implications for businesses. Malicious actors have been developing the mechanism of these attacks for decades, however, security companies have not sat back and issued a number of security solutions aimed at making companies resistant to DDoS attacks or mitigating to the minimum the damage they cause to entities. Generally, companies need to realize that unless they prepare themselves for potential DDoS attacks, they are likely to fall victim overnight.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.
Read next:
More related- Best Practices For Secure MetaMask Snaps Development
10 min read
Discover
- Curve Finance Liquidity Pools Hack Explained
6 min read
Discover
- Wallet Security: Best Practices For Keeping Your Crypto Safe
8 min read
Discover