Nearly 30% of Q3’24 DeFi Hacks Could Have Been Prevented With an Automated Incident Response Strategy
Today, Hacken, in collaboration with the leading crypto compliance security and monitoring platform Extractor, unveils the Q3 2024 Web3 Security Report, offering an exclusive look into the latest security trends and preventive measures within the Web3 space.
This quarter’s report, our most comprehensive yet, features groundbreaking insights into Automated Incident Response Strategies—a proven solution that could have saved nearly 30% of all DeFi losses over the past three months, covering incidents up to September 30. We believe this strategy, combined with bug bounty programs and third-party audits, should be made a mandatory component of all comprehensive security frameworks.
Key Insights: A Deeper Look into Web3 Security
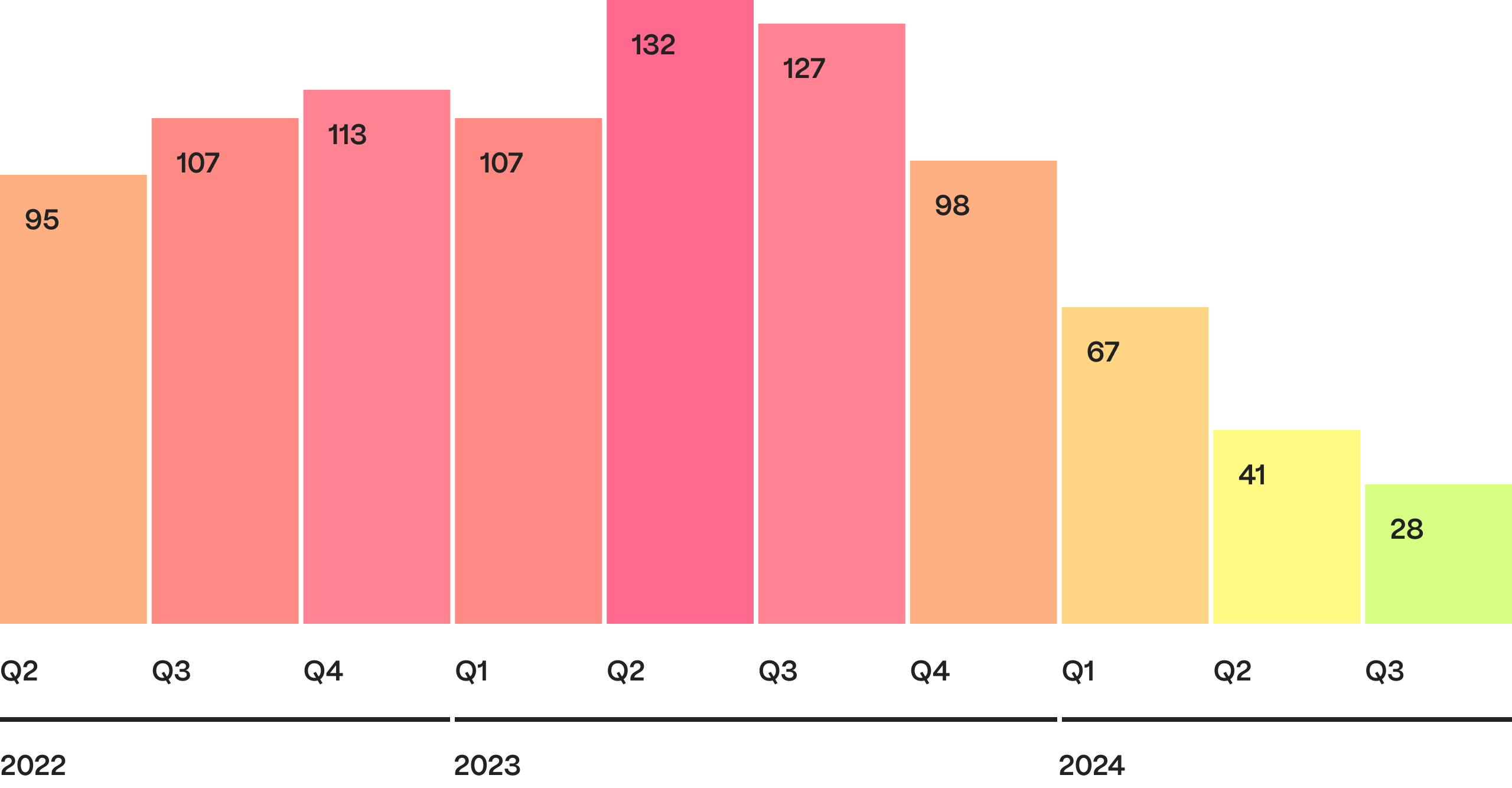
While the number of hacks has decreased to the lowest in three years, with only 28 incidents, the overall situation remains concerning. A staggering 95% of all stolen funds were lost forever, marking a grim trend compared to previous quarters when 50-60% of stolen assets were frozen or recovered. The high rate of unrecovered funds underscores the critical need for more robust post-incident planning.
The Crown Jewel: Automated Incident Response Strategy
At the heart of this quarter’s report is our Hacken Extractor’s Automated Incident Response Strategy—a cutting-edge approach designed to detect and mitigate attacks in real time. Had this strategy been widely implemented, it could have prevented nearly 30% of all DeFi losses in the past three months, translating into potential savings of over $25.6M.
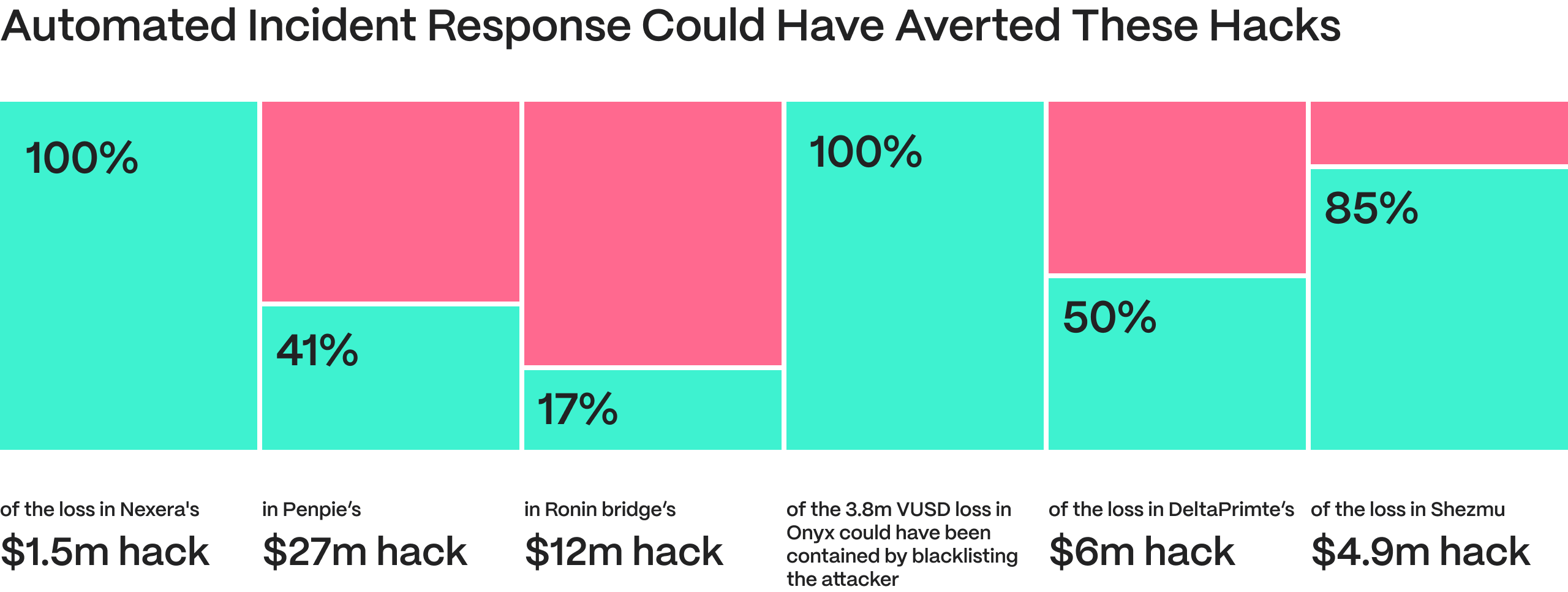
Our report highlights step-by-step incident response strategies for several high-profile DeFi hacks, including those involving stablecoins, compliance flaws, and upgradable contracts. From preventing 17% of the Ronin bridge’s $12M hack by flagging suspicious withdrawals to fully averting Nexera’s $1.5M loss by automatically pausing contracts during a malicious proxy upgrade—these and other cases demonstrate how real-time monitoring and automated responses can significantly reduce financial losses before an attack unfolds.
CEXs and Bridges: Usual Targets
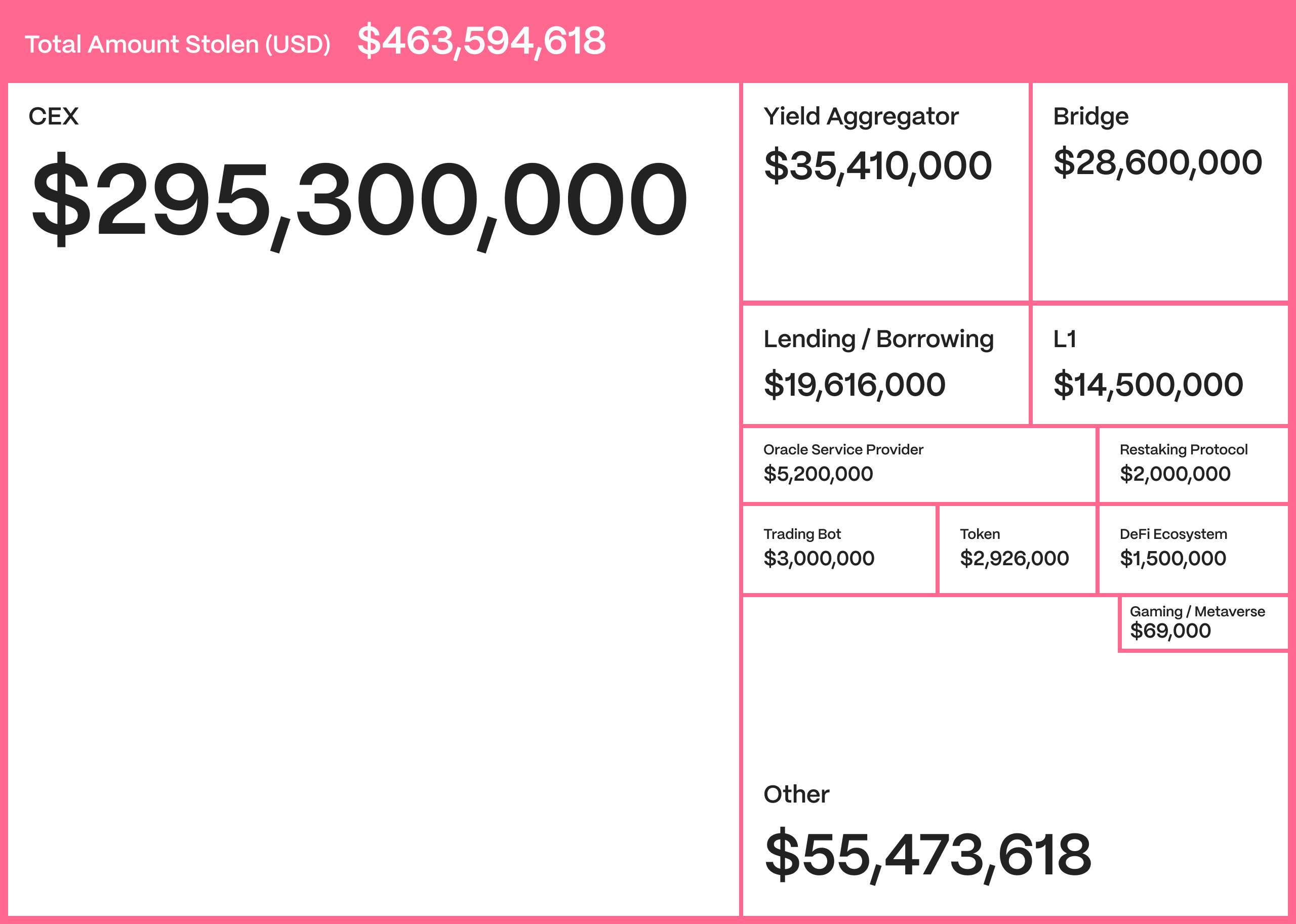
CEXs are the largest pools targeted by hackers. Bridges remain the frequent targets for attacks.
Other Report Highlights:
- Hacking Trends: Despite fewer attacks, $463M was still stolen, with centralized exchanges and bridges being the top targets. The highest share of value lost was reported in Asia.
- Recovery Challenges: A staggering 94.9% of funds were lost without recovery, making this the worst quarter for recovering stolen assets in 2024.
- Preventable Exploits: 28.7% of DeFi exploits could have been prevented, with Extractor’s Automated Incident Response Strategy as a key factor in safeguarding those funds.
- Again, the Biggest Losses Come From Access Control Compromises. Access control is the most dangerous attack, with losses double those of all other attacks combined. Smart contract vulnerabilities most commonly appear after new versions are deployed.
- Rug Pull Scams: Despite a decline in traditional rug pulls, there was a surge in memecoin launches on Base, Tron, and Solana. On pump.fun, Solana’s memecoin platform, over 2 million coins were launched recently, with only 89 reaching a market cap of $1 million. This suggests many rug pull scammers have shifted to these platforms, launching low-value coins that mimic rug pull behavior without showing signs of legitimate activity.
Practical Solutions: Securing Web3’s Future
Our Q3 2024 Web3 Security Report serves as both an analysis and a guide for Web3 projects aiming to secure their ecosystems. Our blockchain security experts recommend the following:
- Take Contract Upgrades Seriously: Ensure all smart contract updates are thoroughly audited and tested before deployment to prevent introducing new vulnerabilities.
- Bug Bounties Over Forced Bounties: Proactively offer bug bounty programs to incentivize security researchers to report vulnerabilities responsibly, rather than exploiting them.
- Implement Automated Incident Response: Deploy real-time monitoring and automated response systems to detect and mitigate attacks swiftly, minimizing potential losses.
- Enhance Private Key Security: Use hardware wallets and secure key management solutions to protect private keys from unauthorized access and malware.
Access the Q3 2024 Web3 Security Report
Our Q3 2024 Web3 Security Report is an essential resource for understanding the current threat landscape and taking actionable steps to protect digital assets. With exclusive insights into our Automated Incident Response Strategy, the report offers real-world solutions that could significantly reduce losses in the DeFi space.



