Hacken Research: How Safe is Your NFT Wallet?
Decentralized Finance has been the most discussed topic within the cryptosphere in 2020. However, other subsets in the blockchain industry have also been making a splash, particularly Non-fungible tokens – or NFTs – which have seen record-breaking sales throughout October.
Non-fungible tokens are used to represent assets that have different values among themselves. This includes collectibles, art, real-estate, game items, and much much more. NFTs allow physical assets to be represented in the digital world, facilitating proof and transfer of ownership and they make digital items completely unique, given that blockchain assets can not be duplicated.
Much like Bitcoin or other cryptocurrencies, NFTs are stored and used through a cryptocurrency wallet. As so, it is important to understand what type of wallet will be used, how secure it is.
Methodology
| Public Security Audit | Public security audit announcement with an indication of the auditor company |
| Bug Bounty Program | Public bug bounty program |
| Password Requirements | Minimum 8 symbols. It also must contain uppercase letter, lowercase letter and digit |
| Hierarchical Deterministic Feature | Hierarchical Deterministic feature support |
| Customizable Mnemonic Length (12/18/24) | Possibility to customize mnemonic phrase length |
| Absence of Major Hack Cases | |
| Can be Connected to Top Defi Platforms | Possibility to connect wallet to most popular DeFi platforms |
| Wallet Connect | Wallet Connect feature support |
| Open Source | Whether the application source code is in a public repository |
What key factors make up a great NFT wallet?
Hacken, a leading cybersecurity company focusing on blockchain technology, decided to review 9 wallets in particular because they are non-custodial, meaning that they allow the private keys to be stored on the user side, thus offering full ownership of the asset at hand. All of the wallet reviews support one of the following: Android, IOS, Desktop, or Browser extension application.
Hacken looked at several factors impacting usability, compatibility and, most importantly, security. Fields included supported blockchain platforms like Ethereum and Bitcoin, ability to connect to top DeFi platforms and to customize the number of words of the mnemonic phrase.
Hacken also looked at Hierarchical Deterministic capabilities that allow users to easily generate new private and public keys and if they had WalletConnect – an open source protocol providing wallets with QR code scanning or deep linking capabilities.
Security-wise, the Hacked research team looked at whether the wallets under review published public audit results, if they had a bug bounty program, strong password requirements, and if there have or haven’t been any security breaches in the past. They also looked at whether the wallets had made their code open source.
The results are as follows:
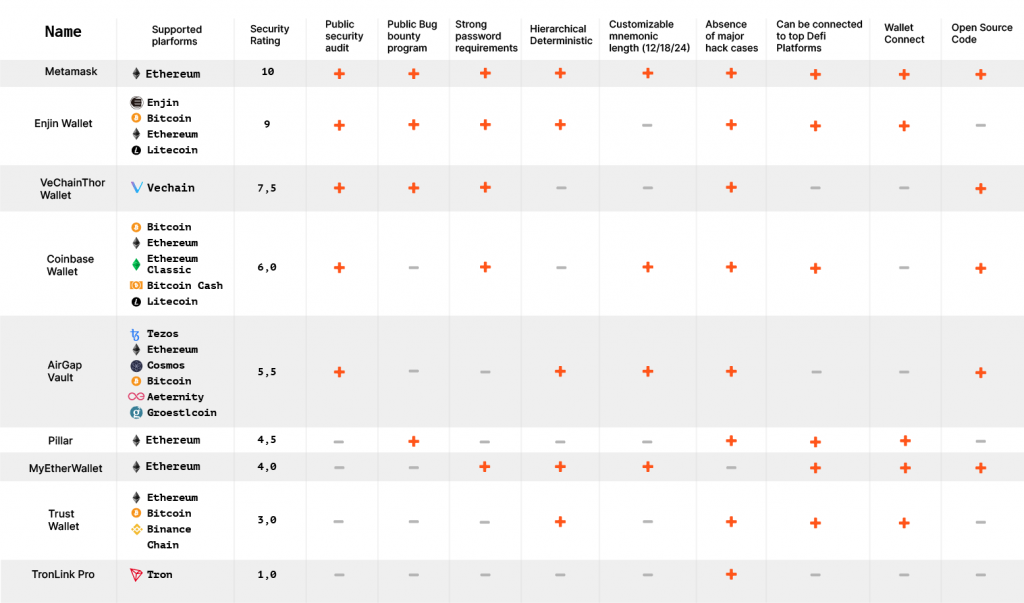
The Results: Taking a Deeper Look
Looking closely at the results, we can see that only 5 out of 9 wallets have conducted a public security audit and announced the results. Security audits are conducted by independent third-party auditors that ensure the wallet follows the most rigorous security standards. Companies that publish information on their latest audits provide transparency, a highly valued commodity in the world of cryptocurrencies, and also increase consumer confidence in the product itself. While audits may not be completely foolproof, they are the closest it gets.
We also found that only 4 out of 9 wallets have ongoing bug bounty campaigns. While not as crucial as public security audits, bug bounties can be an extremely useful tool. By giving independent developers in the community a chance to earn a bounty on any bug found, a company will put its security to test and see how it performs against multiple unexpected attack vectors.
Out of the 9 wallets evaluated, only 5 of them had open-source code. Not only does open-source allow the community to better understand the project, it also allows them to build from it, encouraging industry-wide innovation. Again, transparency is key in the cryptosphere, and nothing is as “see-through” as an open-source project.
5 out of the 9 wallets have strong password requirements. This means that 4 out of the 9 wallets allow the user to protect their private key with a 6-digit PIN, which can be a huge security risk, making the private key prone to brute force attacks.
What’s the Safest Choice?
Looking at each wallet individually, we can surmise that Metamask is the most secure choice, having scored an overall 10 in security, offering both a public security audit, bug bounty programs and being completely open-source. A key feature of Metamask is that it supports Ethereum tokens only, which are the most popular form of NFTs on the market.
The least safe wallet on the list is TronLinkPro with a 1 out of 10 score in security, offering none of the three aforementioned security features and no strong password requirement. This makes the wallet vulnerable to brute force attacks should the device be compromised.
Myetherwallet does not provide information about security audit or public bug bounty program, and while the project is open source and has strong password requirements, it has previously fallen victim to a major hack incident, making it the third least safe wallet with a score of 4.
While the Vechain Thor Wallet offers the same security features as Metamask, it is not as practical as it does not allow a direct connection to DeFi platforms and it only allows for Vechain tokens which are not very popular. However, Vechain is the second most secure wallet on the list with a score of 7.5.
The Coinbase wallet offers a balanced mix between security and ease of use. While it does not offer bug bounties, it supports five blockchain platforms and can be connected directly to major DeFi platforms. It scored a 6 in overall security.
Conclusion
As NFTs continue to make waves in the cryptosphere with record-breaking art auctions and innovative use cases like decentralized domain names, it is clear that the sector will continue to grow.
However, it is important to ensure that users are aware of the risks being taken when interacting with NFTs. Needless to say that each user should carry out their own research, but this post can act as a starting point to do just that.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.

Table of contents
Tell us about your project
Read next:
More related Bybit Hack Investigation: The Biggest Crypto Heist In History
Bybit Hack Investigation: The Biggest Crypto Heist In History12 min read
Insights

