Complete Cryptocurrency Audits List Research
Over the entire existence of cryptocurrencies, several thousand different projects have been launched. Most of them have already ceased to exist and are no longer listed on any exchange platforms, but there are still a handful of projects that are operating and growing.
Many of these “living” crypto companies, however, have failed to invest proper time and resources into their own security. This leaves many of them open to hacks, exploits, and loss of investors’ funds.
We decided to investigate how many of these active projects have abided by basic security best practices, including getting third-party code audits done and launching bug bounty programs for white hat hackers.
In this research, our Hacken team reviewed 1,053 cryptocurrency projects.
Statistics
We found that 76.5% (see Fig. 1.) of projects have either not passed a security audit or have not publicly disclosed the fact they had been audited.
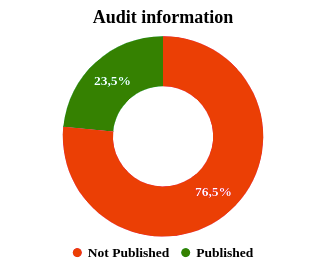
The remaining 247 (23,5%) projects have all undergone at least one audit.
Our specialist cybersecurity team ranks regular code audits as one of the most essential security measures a crypto project can take to avoid hacks. However, the presence of third-party security audits does not mean that the project is 100% secure.
The only time audits are not as important are when the crypto project boasts a significantly large community – such as Bitcoin, Ethereum, etc – since all updates go through the test network, and during this period many enthusiasts and bug hunters send bug reports.
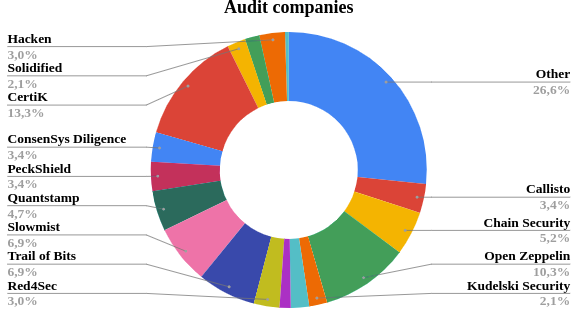
According to the information, we have collected, the number of security companies engaged in audits is not large. Most of the audits (see Fig. 2.) were performed by the following companies:
- CertiK
- Hacken
- Slowmist
- Open Zeppelin
- Kudelski Security
- ConsenSys Diligence
- Chain Security
- Red4Sec
- Callisto
- Trail of Bits
- Quantstamp
- Solidified
- PeckShield
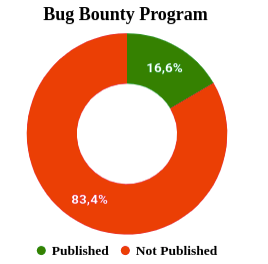
Our results also show that a majority of projects do not have active bug bounty programs. In fact, only 16.6% (see Fig.3.) were found to have live bug bounty programs when our research was conducted.
In short, a bug bounty program is a deal offered by crypto services and platforms whereby individuals can receive recognition and compensation for reporting bugs, especially those pertaining to security exploits and vulnerabilities. This is a way to detect software and configuration errors that can slip past developers and security teams and later lead to big problems.
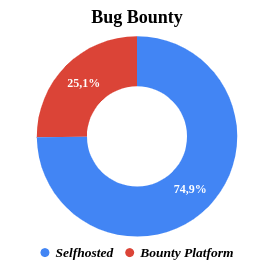
Only 25.1% (see Fig.4.) of projects who have launched a bug bounty program do so via a third-party managed program.
It should be noted that the most effective bug bounties are ones issued on well-known bug bounty platforms so that the maximum number of ethical hackers can participate in it. If the project lists its own bug bounty program and hasn’t built up a substantial community, then it greatly limits the number of potential hackers who will take part.
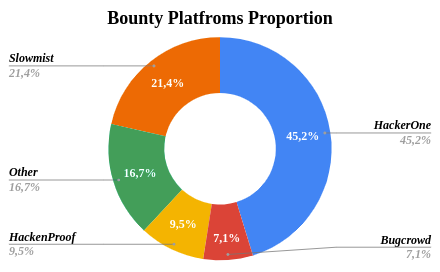
The list of bug bounty platforms that choose cryptocurrency projects is much smaller than the list of audit companies. Most of the bug bounty programs (see Fig.5.) are listed on the following platforms:
- HackerOne
- Bugcrowd
- HackenProof
- Slowmist
Conclusions
As apparent from research results, only 23.5% of projects performed security audits of their tokens or platforms. The results show that there are many auditors in the market, and while there is no monopoly currently, some stand out from the rest.
In terms of the bug bounty programs themselves, only 16.6% of projects have an active bug bounty program. Out of all the bug bounty platforms we looked at, we identified these key market leaders:
- HackerOne
- Bugcrowd
- HackenProof
- Slowmist
Overall, it’s clear that a vast majority of functioning crypto projects on the market right now have not invested in their own security. A complete list of audits will be published on cer.live website in the middle of January.
Subscribe
to our
newsletter
Be the first to receive our latest company updates, Web3 security insights, and exclusive content curated for the blockchain enthusiasts.

Read next:
More related Bybit Hack Investigation: The Biggest Crypto Heist In History
Bybit Hack Investigation: The Biggest Crypto Heist In History12 min read
Insights
 DeFi Security Risks and Hacks in 2021
DeFi Security Risks and Hacks in 20219 min read
Insights
 Hacken Research: How Safe is Your NFT Wallet?
Hacken Research: How Safe is Your NFT Wallet?5 min read
Insights