Static Analysis of Android Mobile Applications — MobSF Manual
Static analysis is one of the stages of testing a mobile application. According to Hacken pentesters, the most convenient open source framework is MobSF. Based on the framework, we’ll show how the static analysis for Android applications is performed; mind that the Android application analysis doesn’t require performing any application functions.
Basic Information about MobSF
MobSF performs static analysis of applications: Android, Apple iOS, and Windows Phone, as well as dynamic analysis which is solely for Android applications.
The Process of Testing
Step 1
After installing MobSF, run the following script to start the server (let’s use the drive D as an example).
[pastacode lang="bash" manual="d%3A%0Acd%20.MobSF%0Apython%20.manage.py%20runserver" message highlight provider="manual"/]
Then go to the address http://127.0.0.1:8000 and get to the main page There are not too many functionalities here:
- file upload
- view previous scan reports
- transition to API documentation
- transition to GitHub project
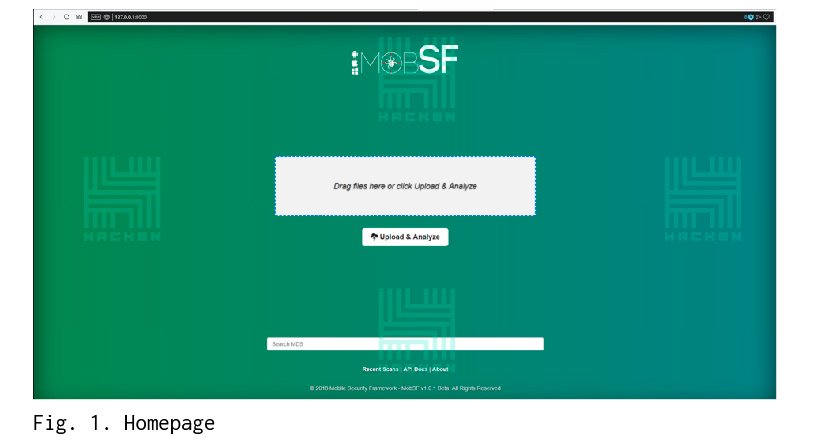 Step 2
Step 2
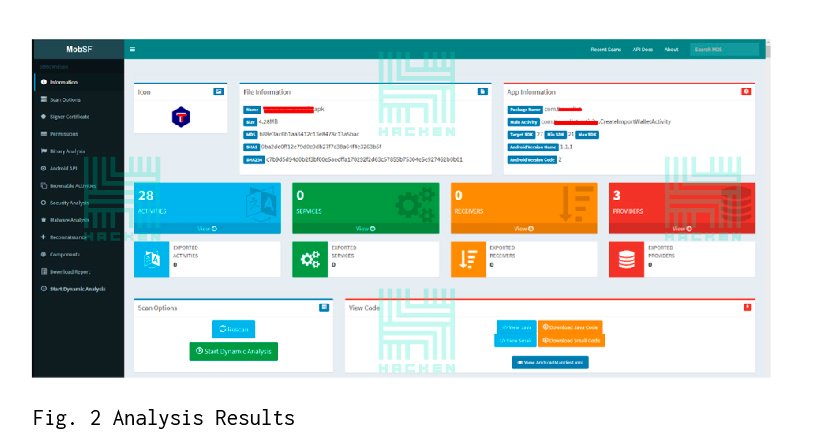
After the file has been downloaded and analyzed, a page with the analysis results appears. There is a menu on the left that allows you to navigate quickly across the entire page (the result is pretty voluminous though). Here is useful information in this screenshot:
- application hash sum;
- Supported Android OS Versions;
- the number and type of components (exported or not): it’s important, as exported components can lead to critical vulnerabilities;
- the ability to view and download java- and smali-files that can be analyzed either by other tools or manually;
- view manifest file for analysis.
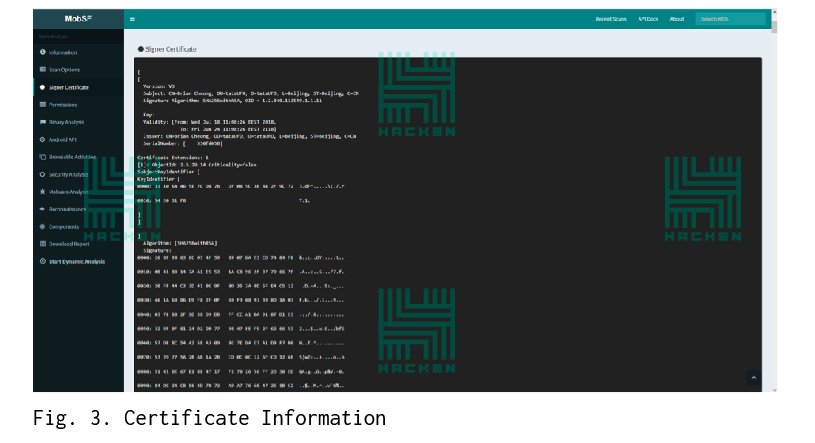
In fig. 3 you can see the information about the certificate used to sign the application.
Step 3
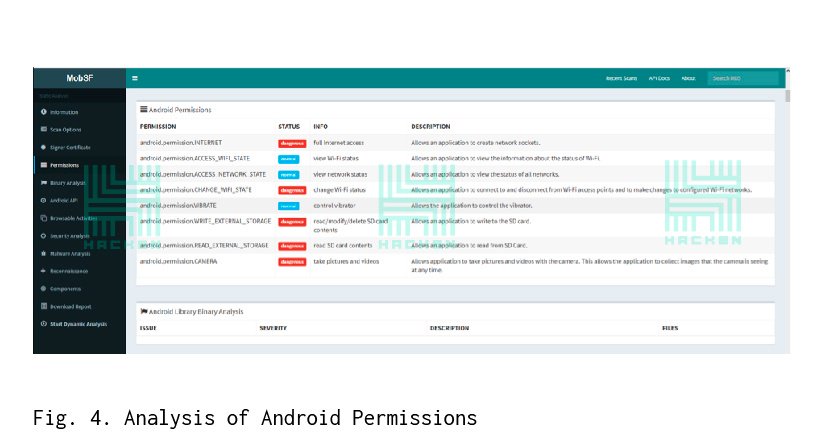
We can view the description of the permissions analysis, which is described in the AndroidManifest.xml file. MobSF analyzes the permissions of the Android application, determines its status concerning criticality, and the description of permissions. Here you need to understand the architecture of the Android OS to assess its actual criticalness.
The Security Analysis --> Code Analysis tab shows the analysis result of java-code by a static analyzer. It identifies potential vulnerabilities, determines their severity, and the files in which this type of vulnerability was found. These results can be considered false positive, and you need to recheck everything anyway.
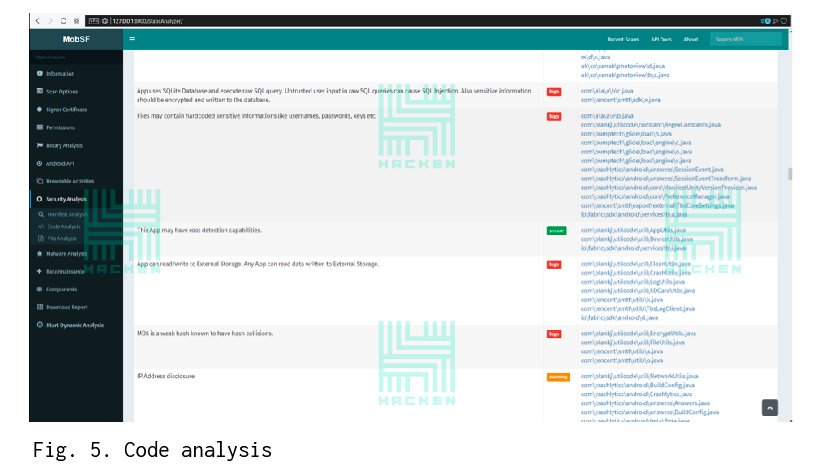
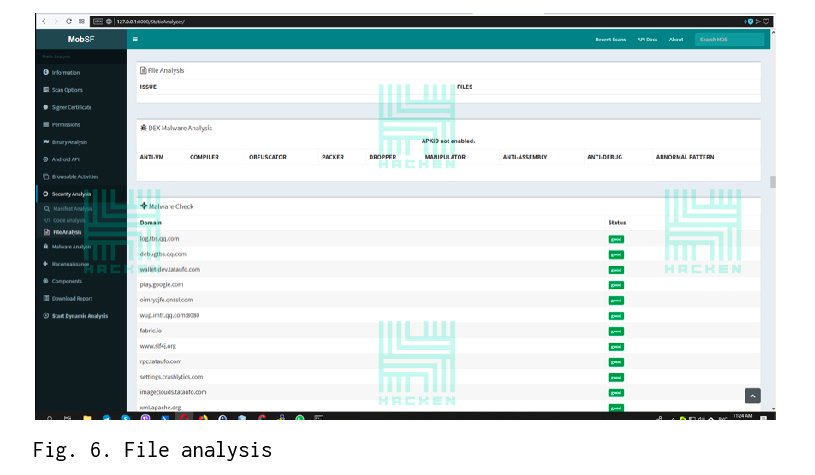
The next tab shows the analysis of files on the virustotal.com service. In this case, the file was not marked as infected.
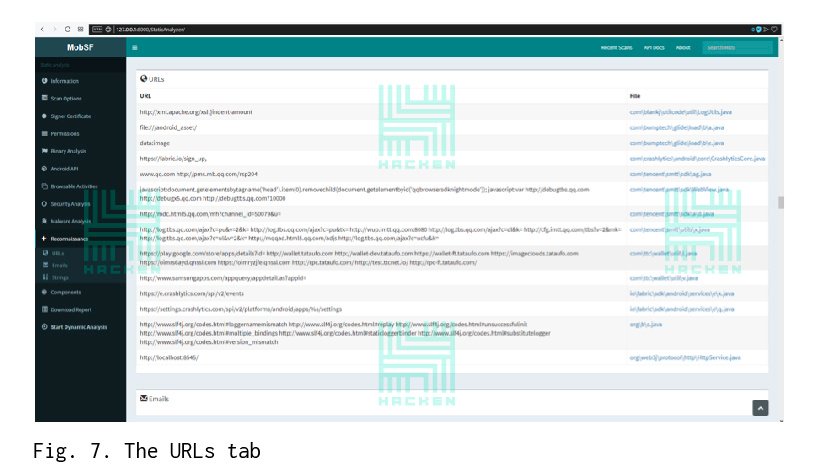
The URLs tab displays the list of URLs, IP addresses, and the files in which they are stored or called. This section analyzes where the Android app sends the data or where it stores the information.
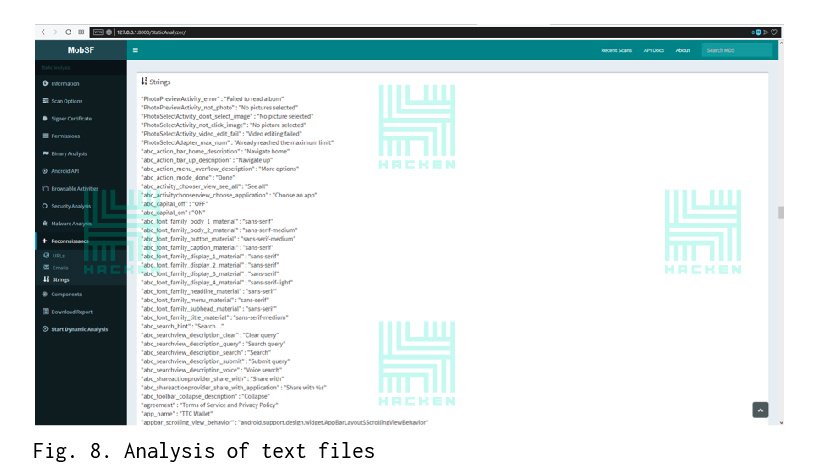
The “Strings” tab analyzes the text files that are in the res directory. When analyzing an application, these files may contain hard-to-find accounts and other sensitive data. However, we haven’t encountered such a problem.
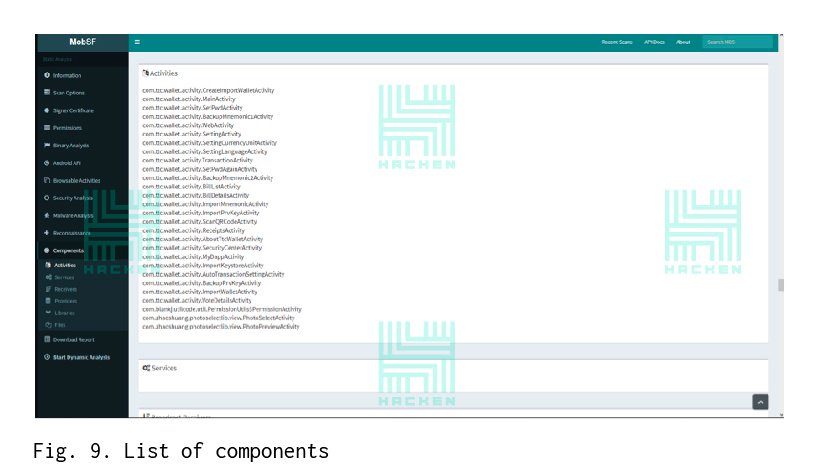
The “Components” tab displays a complete list of components (activity, service, content provider, and receives), imported libraries and files without defining the extension.
Want to order Mobile Pentest?
Step 4
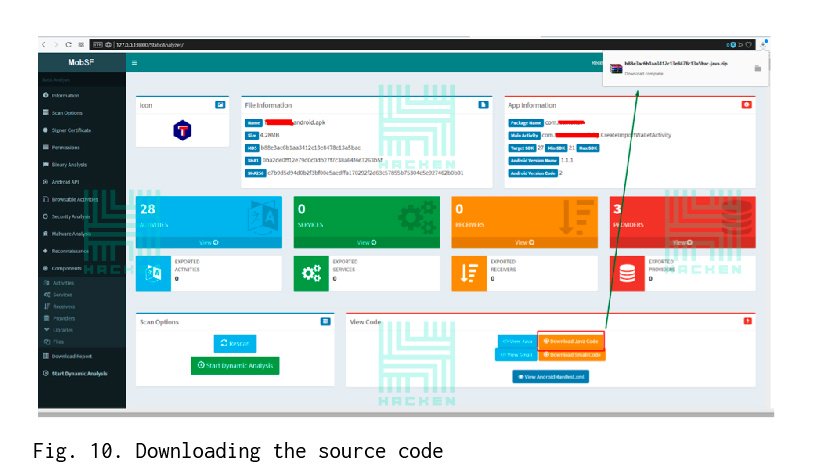
Additionally, the source code can be analyzed using the VCG scanner static analyzer. VCG needs source code. The source code can be downloaded via the Download Java Code button. The file is downloaded in a zip archive.
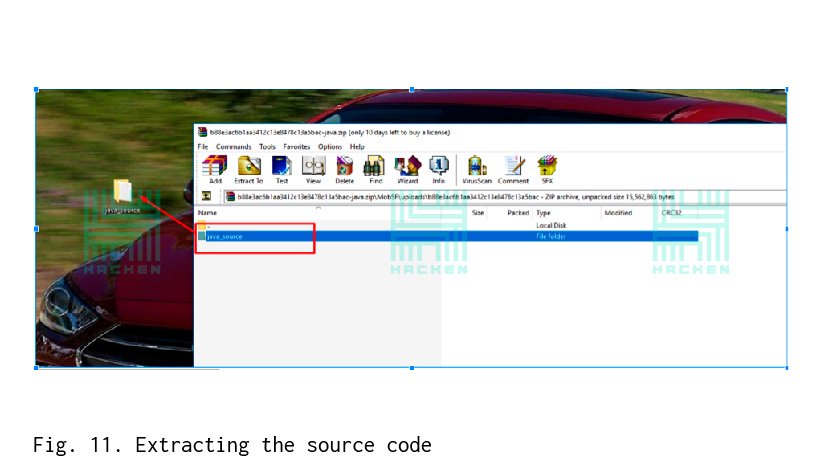
Next step is extracting the folder with the files from the archive.
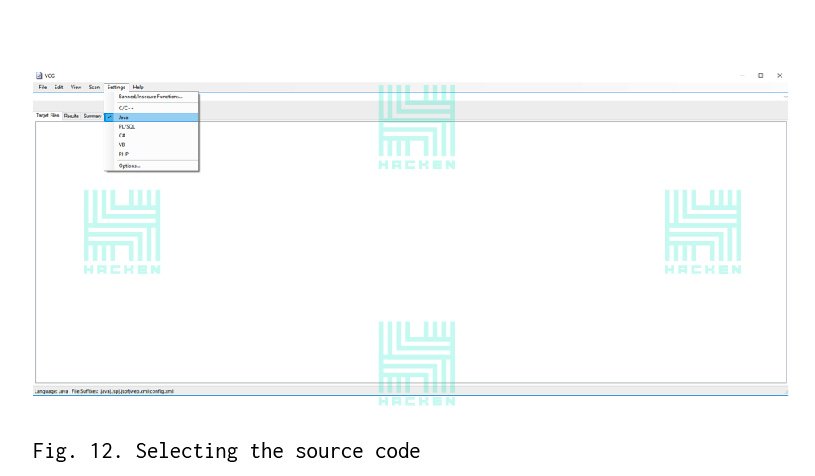
Source code scanning is performed as follows:
- In the “Settings” tab, select “Java” — Fig. 12.
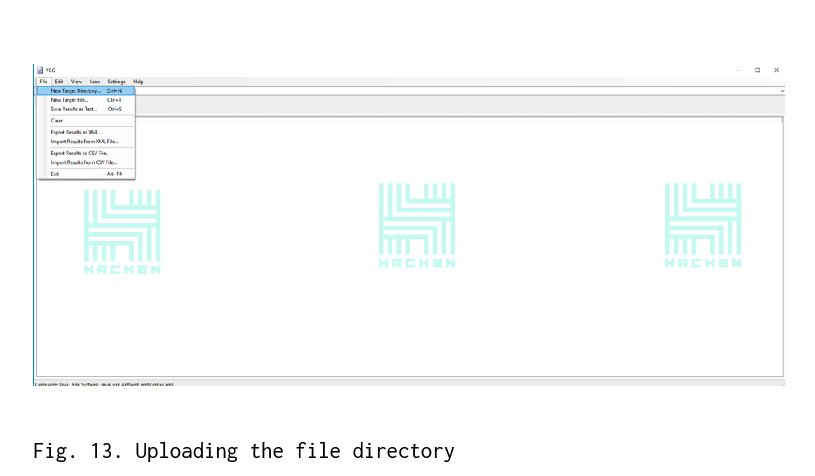
- In the “File” tab, select “New Target Directory” — Fig. 13.
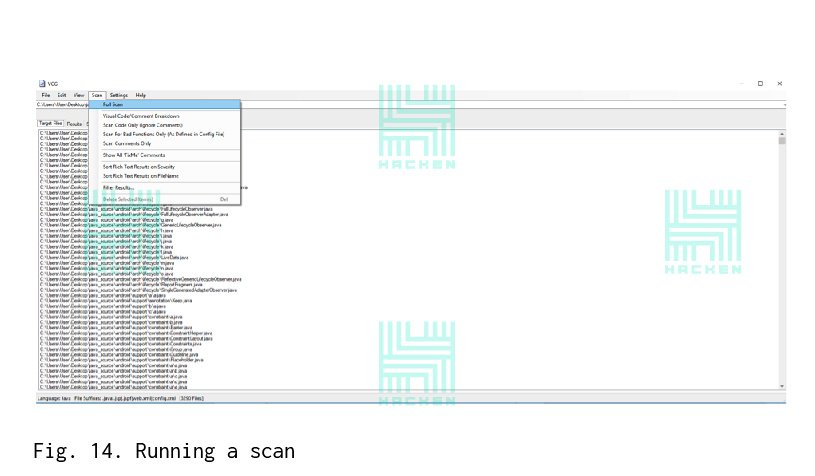
- In the “Scan” tab, select “Full scan” — Fig. 14.
Step 5
After the scan is completed, the scanner issues the name of the vulnerability, its criticality, a brief description, and place in the source code.
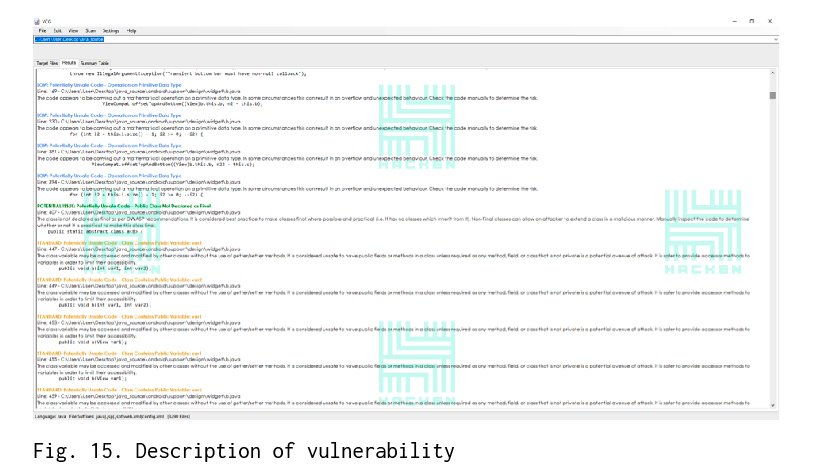
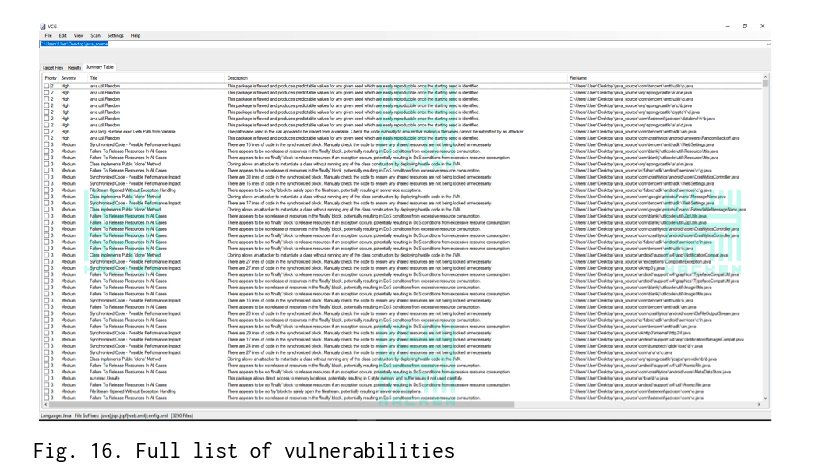
You can get a complete list of vulnerabilities and sort them according to their criticalness.
Conclusion
Static analysis of the application and source code provides a basic understanding of the architecture of the Android application and the potential vectors of attacks. According to the methodology used at Hacken, any pentesting of client’s applications starts with the static analysis. In the next article, we’re going to tell you how to conduct a dynamic analysis specifically dedicated to MobSF.
How Hacken can help
No system is perfectly secure; no system is without flaws and weaknesses. If you are convinced yours is safe and sound, you just don’t know about potential vulnerabilities yet. Hacken's specialists know how to secure the future of your business.
Table of contents
Tell us about your project
Read next:
More related Crypto Travel Rule: Global VASP Requirements in 2025
Crypto Travel Rule: Global VASP Requirements in 202511 min read
Discover
 What Is Web2.5? A Builder’s Guide to the Web2–Web3 Bridge
What Is Web2.5? A Builder’s Guide to the Web2–Web3 Bridge5 min read
Discover
 How to Choose a VASP License: Jurisdictions, Costs & Compliance
How to Choose a VASP License: Jurisdictions, Costs & Compliance5 min read
Discover