Multi-platform Penetration Testing
March–April 2025

Overview
MEXC is one of the world’s top cryptocurrency exchanges, serving over 40 million users globally. Known for its high-speed transaction engine and a massive selection of trading pairs (3,000+), MEXC is a go-to platform for both retail and institutional traders.
As MEXC scaled its operations and mobile footprint, it engaged Hacken to conduct a full-scale security assessment across its Android app, iOS app, and Web/API ecosystem. The objective of Hacken’s multi-platform penetration testing was to identify exploitable vulnerabilities, improve app resilience, and validate that MEXC meets high security standards for crypto users worldwide.
Audit Scope and Methodology
The security assessment covered three distinct platforms:
- Android Application (v6.3.1, Java)
- iOS Application (v6.1.0, Swift)
- Web Application & APIs (ddjhe.com, public and authenticated endpoints)
Testing was performed in accordance with Hacken’s established Pentest Methodology, combining manual and automated techniques, dynamic analysis, and real-world attack simulation.
Key Findings & Remediation
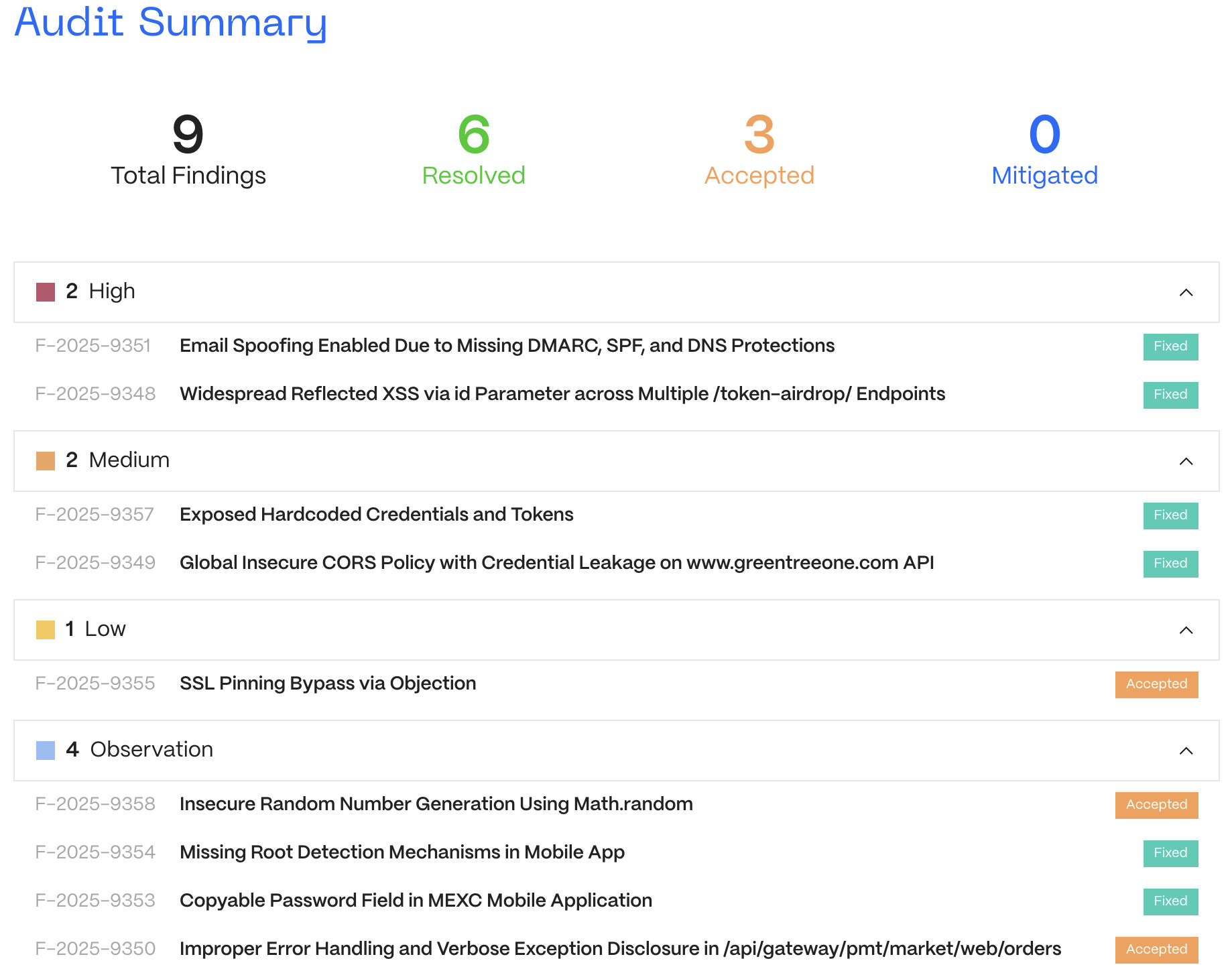
Android App Security Review
Our Android assessment revealed high-impact issues such as a reflected XSS vulnerability across multiple token airdrop endpoints and a missing DMARC/SPF configuration, making the domain spoofable for phishing. Additionally, hardcoded credentials, insecure CORS configurations, and SSL pinning bypass were uncovered.
All critical and high-severity findings were resolved, with MEXC updating their security headers, implementing strict sanitization, and improving server-side certificate handling.
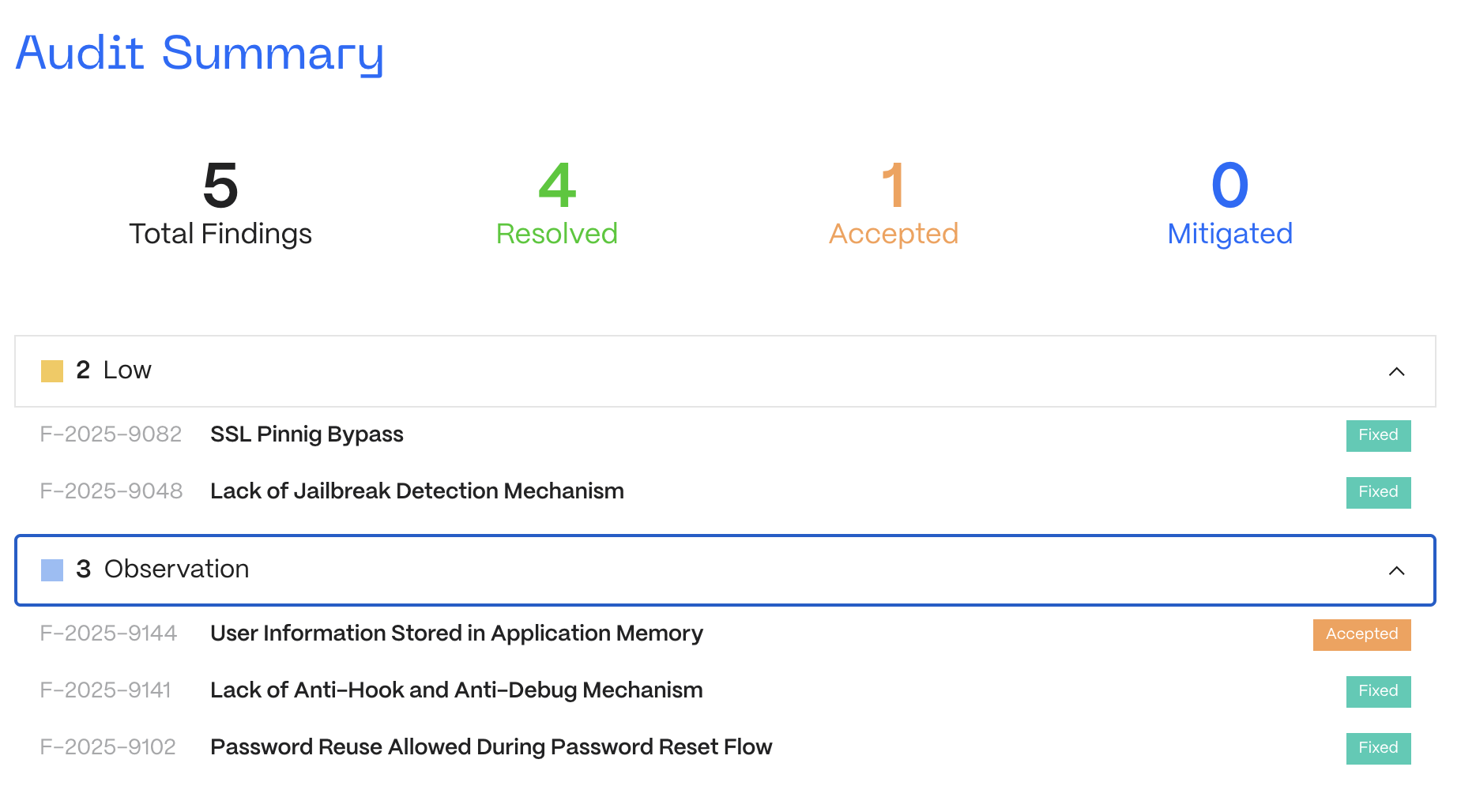
iOS Application Security Review
The iOS application was found to lack jailbreak detection and had SSL pinning mechanisms that were easily bypassed with dynamic tools like Frida. Additional concerns included user info stored in memory, password reuse during resets, and lack of anti-debug protection.
After the audit, the MEXC team implemented stronger runtime protections, enhanced pinning logic, and tightened secure data handling practices.
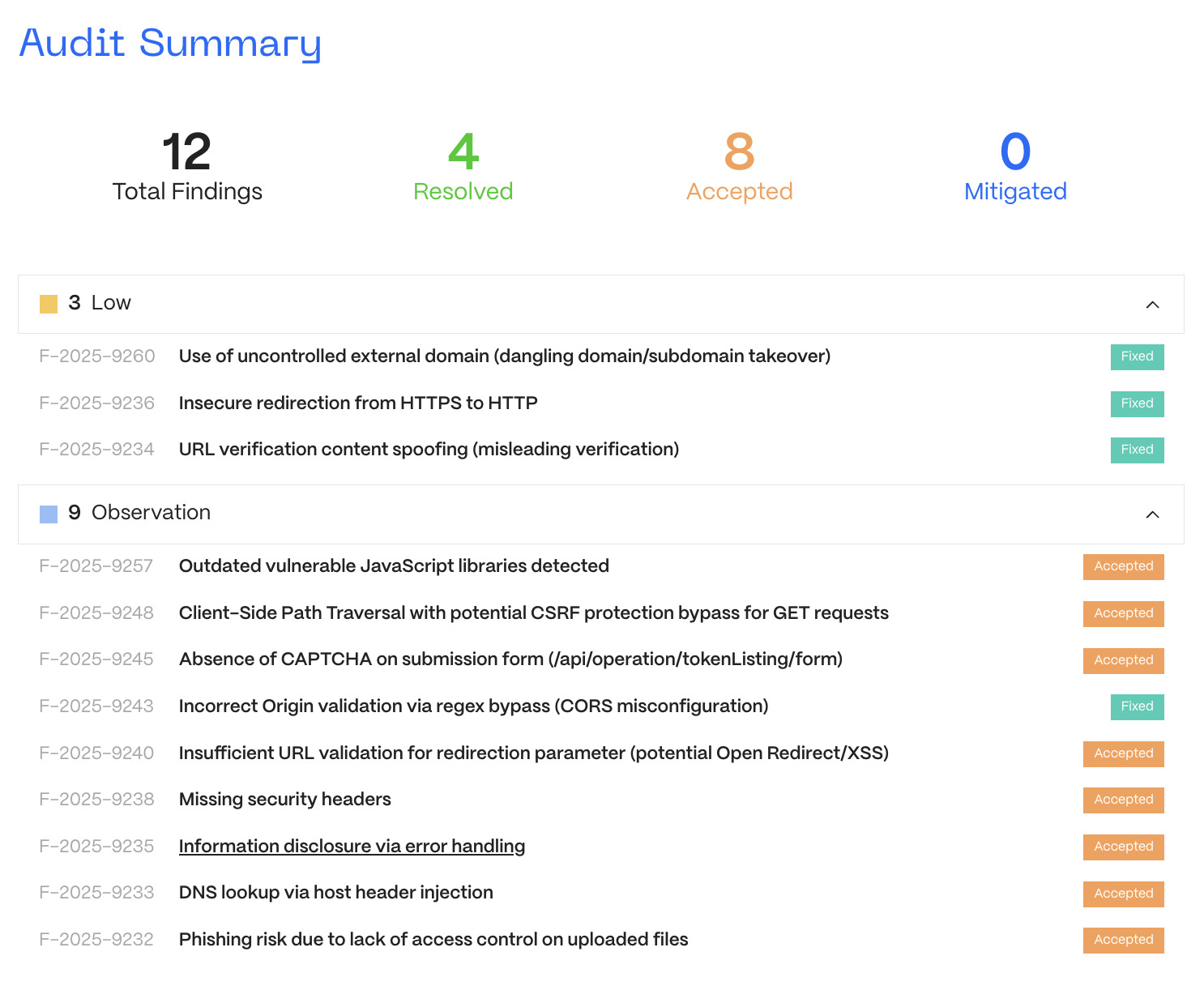
Web and API Assessment
The Web/API audit of MEXC’s DEX+ interface identified several low to medium-severity issues, including:
- Dangling subdomain allowing potential malicious app distribution
- Protocol downgrades from HTTPS to HTTP
- Missing security headers and outdated JS libraries
- Access control gaps allowing public access to uploaded files
The MEXC team promptly fixed misconfigurations and deprecated third-party links, updated all client-side libraries, and tightened upload handling logic.
Impact
MEXC’s commitment to security was evident in how swiftly they addressed reported issues across all platforms. The comprehensive pentest not only closed known vulnerabilities but also raised internal awareness on mobile-specific threats and secure API design.
By working closely with Hacken auditors, MEXC reinforced trust with its global user base and demonstrated a proactive approach to cybersecurity in the Web3 space.
Looking to Secure Your Exchange?
Get in touch with Hacken to schedule a tailored audit across mobile, web, and backend infrastructure.



