The window to exchange $HAI for Hacken Equity Shares ($HES) is now open > Claim your spot today
Q1 2024 Web Security Report
By Hacken
As we delve into the first quarter of 2024, the landscape of crypto security reveals both persistent challenges and emerging trends in the midst of a bull run. From substantial financial losses to innovative recovery efforts, the crypto space continues to evolve amidst an environment of heightened threat activity. Our report aims to uncover the key findings of the quarter, providing valuable insights and recommendations to fortify the security of Web3 businesses.
Q1 2024 Security Highlights
- $824,405,224 Stolen: In Q1 2024, the crypto space witnessed 67 hacks totaling a staggering $824,405,224 stolen. This surge in malicious activity underscores the pressing need for enhanced security measures.
- $682,086,639: Access control breaches emerged as the most prevalent vulnerability, with $682,086,639 lost to such exploits. These incidents highlight the critical importance of robust access control mechanisms.
- $443,773,698 Recovered: Despite the onslaught of attacks, the sector demonstrated resilience, with $443,773,698 recovered or frozen post-incident. This represents a significant improvement in the industry’s ability to respond to and mitigate the impact of hacks.
- 56%: Share of rug pulls and smart contract vulnerabilities in all incidents, signaling the persistent threat posed by such tactics.
Key Observations
Evolution of Attack Vectors
While access control breaches remained prevalent, flash loans and smart contract vulnerabilities also emerged as significant attack vectors. Hackers are continually adapting their tactics to exploit vulnerabilities across multiple fronts.
Bull Market Drives Bad Actors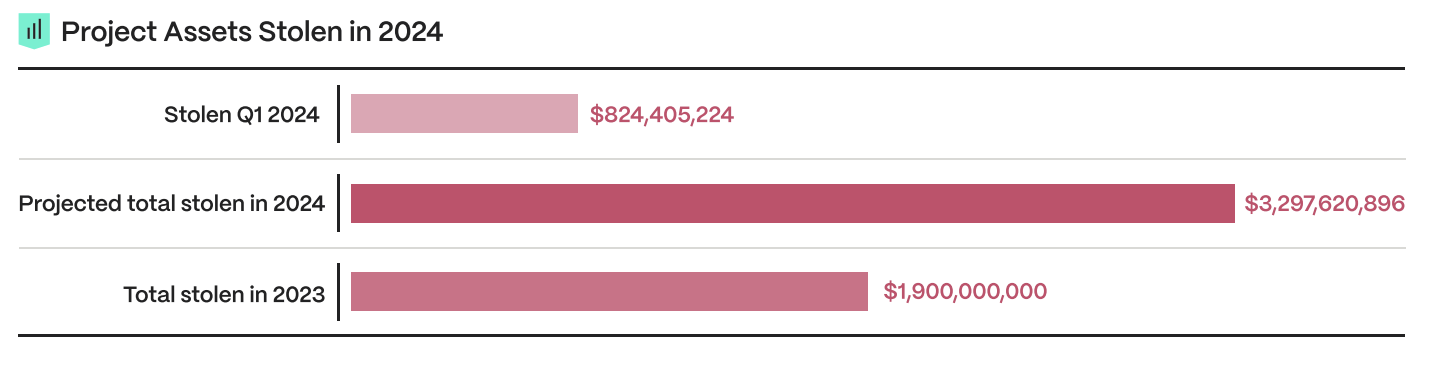
In 2024, increased hacking activity and losses compared to 2023 can be attributed to the bullish market sentiment driving heightened activity and the emergence of vulnerable protocols in ‘’under-discovered” vectors like gaming, tokenization, and new dApps.
Diverse Vulnerabilities Across Project Types
Security incidents spanned a wide range of project types, from tokens to gaming platforms and decentralized exchanges. This diversity underscores the pervasive nature of security threats across the entire Web3 ecosystem.
Recovery Efforts
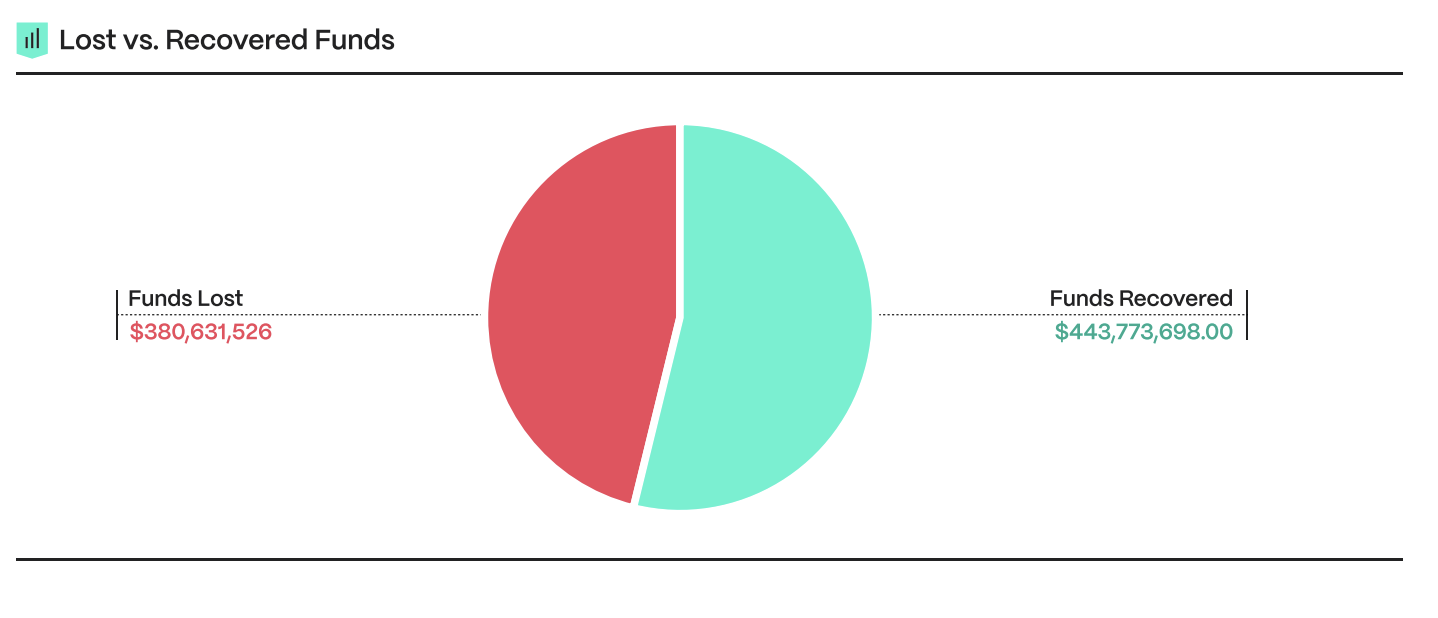
In Q1, over $443 million was successfully recovered or frozen from crypto hacks, amounting to 54% of the stolen funds. This represents a significant improvement in the industry’s responsiveness. Despite one standout incident involving PlayDapp, Web3 projects collectively managed to recover 23% of stolen funds, showcasing proactive measures from both teams and white hat hackers.
Most Of Hacked Projects Didn’t Have Audit
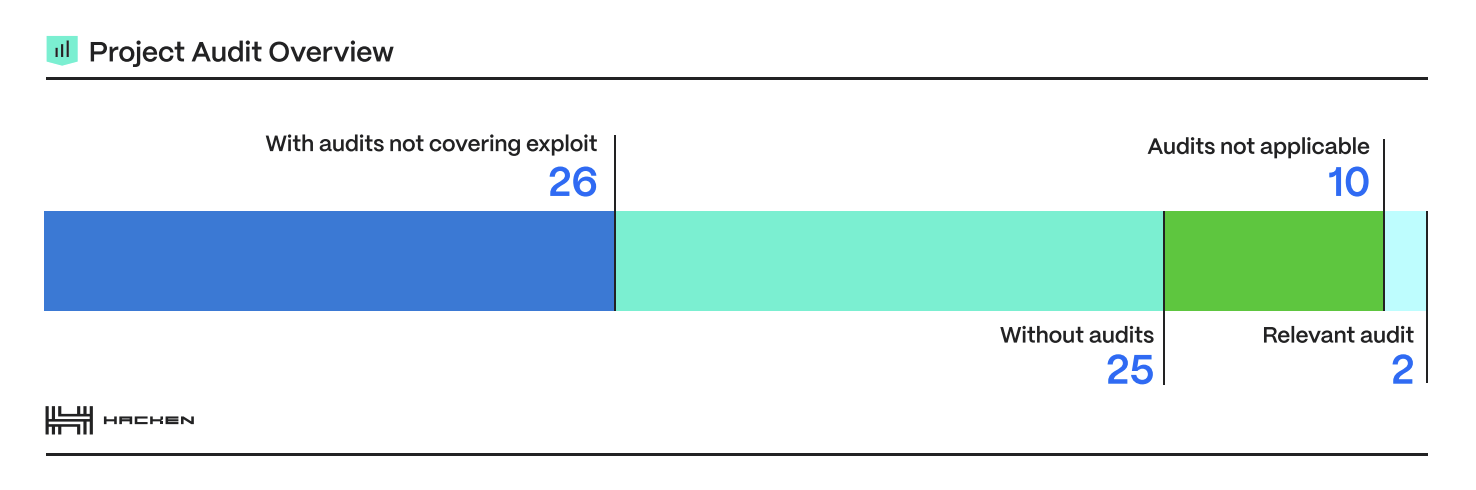
During Q1, only 44% of Web3 projects underwent smart contract audits, leaving vulnerabilities unresolved in 56% of cases. Exploits often occurred post-audit due to new code deployments or upgrades, highlighting the need for continuous security monitoring and updated audit scopes. Audits are crucial, but they don’t guarantee immunity; ongoing monitoring and security-first approaches are essential for risk mitigation.
Access these and other insights in the full report.
Exclusive Case Studies
Our report showcases in-depth case studies of two significant incidents: Shido and ALI. Here’s a brief summary of the attacks.
Shido Protocol Exploit
The Shido Protocol suffered a major exploit due to an access control vulnerability, resulting in the loss of over $35 million. This incident underscores the critical importance of robust access controls and security restrictions.
ALI Token Phishing Attack
The ALI token incident exemplifies the swift response and collaboration within the Web3 community, highlighting the efficacy of proactive measures in mitigating the impact of security breaches.
For a detailed analysis, access the full report.
Recommendations
- Comprehensive Auditing and Monitoring: Regular audits, combined with ongoing monitoring and assessment, are essential for identifying and mitigating security risks proactively.
- Proactive Security Culture: Fostering a security-conscious mindset among Web3 builders through education and awareness initiatives is paramount in mitigating risks beyond audits.
- Stringent Access Controls: Implementing robust access control mechanisms, such as multisig wallets, can significantly reduce the risk of unauthorized access and exploitation.
- Collaborative Security Efforts: Encouraging collaboration and information sharing within the Web3 community can enhance collective resilience against emerging security threats.
Conclusion
As we navigate the evolving landscape of crypto security, proactive measures and collaborative efforts are critical for safeguarding the integrity of the Web3 ecosystem. By prioritizing security, fostering a culture of vigilance, and embracing comprehensive security practices, businesses can mitigate risks and build a more resilient future in the crypto space.


Subscribe to our newsletter
Enter your email address to subscribe to Hacken Reseach and receive notifications of new posts by email.


